SaaS Management: Why It Matters & Top SMP Vendors (2026)

Every month, finance gets hit with another batch of SaaS invoices. IT sees a different mess: hundreds of accounts, unused licenses, and shadow tools no one remembers buying. Meanwhile, employees are stuck juggling logins, waiting on support, or using the wrong apps entirely.
The real problem? None of these departments have full visibility into the company’s SaaS spend or understand the true cost of SaaS sprawl. SaaS is easy to buy but hard to track. And when no one’s managing it, costs spiral, data leaks, and productivity takes a hit.
This growing chaos isn’t unique — it’s part of a global trend. Gartner estimates global SaaS spending hit $300 billion in 2025. IDC puts overall software spending in 2025 at $1.3 trillion.
This SaaS explosion has led to the rise of SaaS management techniques and, specifically, SaaS Management Platforms (SMPs) that do the heavy lifting for you.
In this guide, we’ll cover why SaaS management is important, how to start doing it today, and who the top SMPs in 2025 are.
Table of Contents
- What is Saas Management?
- Why do I need SaaS Management?
- What should a SaaS management plan include?
- Can I DIY Saas Management?
- Can I use legacy software tools for SaaS Management?
- How can I manage my SaaS, then?
- The top 5 SaaS Management vendors
What is SaaS Management?
By cataloging each subscription, tracking real‑time usage, and tying spend to actual value, IT and procurement can spot duplication, trim waste, and keep security reviews on schedule.
Beyond housekeeping, this discipline safeguards budget accuracy, speeds new‑hire setup, and curbs the risks of shadow IT. Mid‑size organizations often juggle hundreds of apps (indeed - companies in the 100-500 employee range average 536 apps according to Torii’s 2025 benchmark). Without a coordinated approach, costs swell and compliance gaps open.
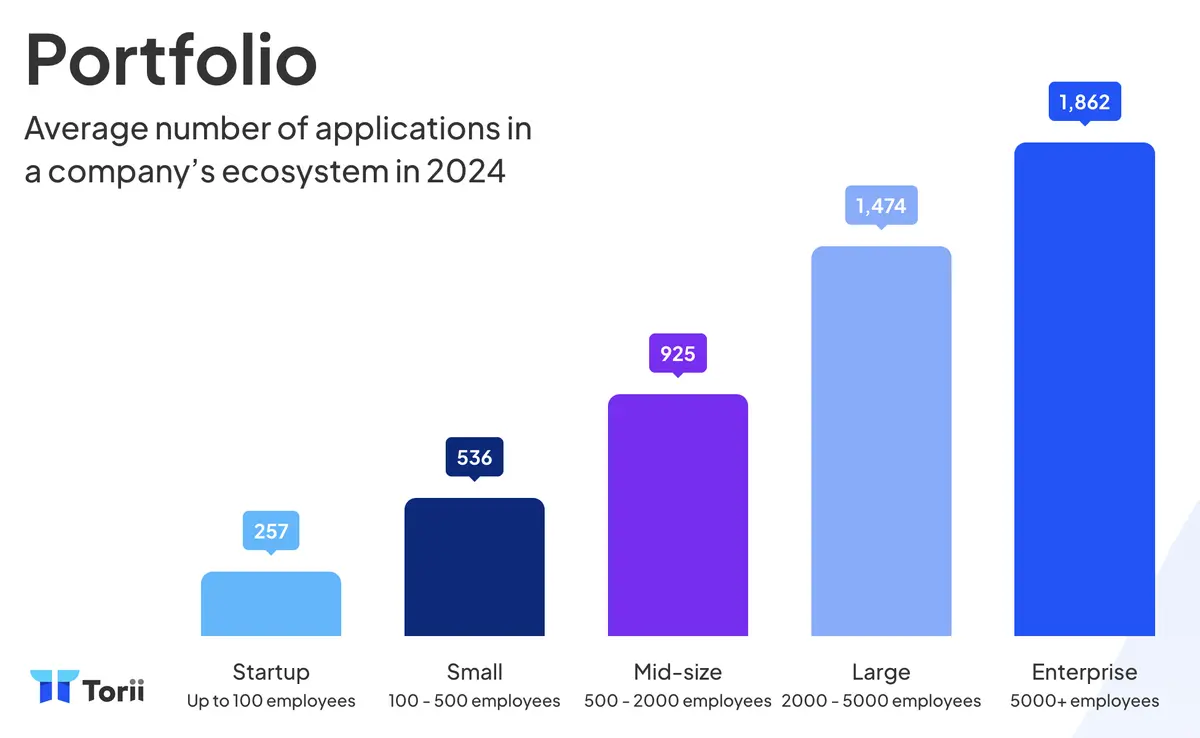
Generally, SaaS management is accomplished via third-party tools called SaaS Management Platforms, which automate the discovery of shadow AI and other SaaS tools, alerts, workflows, and so on. But the concept of ‘SaaS management’ could also refer to manual tracking and Google spreadsheets.
SaaS Management Quick Start Checklist
Before diving deep, here’s your actionable SaaS management checklist:
✅ Week 1: Audit current SaaS spend via credit card statements and SSO logs
✅ Week 2: Identify duplicate tools and unused licenses
✅ Week 3: Calculate potential savings (typically 20-30% of SaaS budget)
✅ Week 4: Evaluate SaaS Management Platform options
✅ Month 2: Implement automated workflows for onboarding/offboarding
✅ Ongoing: Monitor shadow IT and contract renewals monthly
Why do I need SaaS Management?
With every new tool added, the risk profile—financial, operational, and security-related—grows.
Wasted SaaS spend
If you have hundreds of employees, what are the odds that multiple teams have separate paid Notion accounts that could be merged? Or one team uses Asana and another Monday.com, and combining them would save costs? And what’s the likelihood you’re still paying for that ex-employee’s seat on Zoom?
These two problems - duplicate spend and zombie licenses (unused or orphaned licenses tied to former employees) - can cost companies hundreds of thousands a year. But without a clear-cut SaaS management strategy, who’s the owner? Is it the department heads tracking their teams, or the CFO tracking spend, or the IT team tracking tool usage?
Security risks
It’s fair to say that if employees are signing up for whatever tools they want, that your company will run into Shadow IT issues, which involves using tools that the IT/security team hasn’t approved.
While most SaaS tools aren’t malware, if a service isn’t approved - and especially if credit cards are involved - there’s the risk of malware, endangered PII data, and credit card theft. While one user adopts a known platform like HubSpot, others may try unvetted tools that fly under IT’s radar. There’s nothing inherently wrong with this (tools are tools for a reason), but without a SaaS management process in place, the odds of a security breach increase every month.

An overworked IT team
To address security risks, IT teams are usually tasked with maintaining access controls for employees. For instance, turning off Salesforce access if someone has left the company. On the flip-side, when someone has joined, the IT team may oversee the onboarding and access approval for all new hires.
While SSO tools like Google SSO or Okta can help prevent unauthorized access, they don’t monitor usage patterns or license wastage. The IT manager will still need to track this.
Or, if IT has discovered someone is using a new app, they have to manually reach out to the user and understand what it is. This is a thankless task that eats into their bandwidth.
Missed contract renewals
Imagine trying a tool on an annual contract and never finding value from it. You told yourself you would remember to reach out to cancel before the contract ends in six months. Inevitably, you forget. You finally get them to cancel it, but not before wasting hours and still having to pay a 25% buyout fee.
Now, imagine that across potentially hundreds of applications across thousands of employees. Without a SaaS management plan in place, these renewal windows will go missed.
What should a SaaS management strategy include?
A best‑in‑class SaaS program stands on four essential pillars:
The 4 Pillars of SaaS Management
- Discovery & Visibility - See every app in use
- Spend Optimization - Cut costs by 20-30%
- Security & Compliance - Reduce breach risks
- Workflow Automation - Save 160+ IT hours monthly Individually they solve distinct problems; together they turn every subscription, login, and byte of data into a measurable business advantage.
-
Discovery & Visibility: Before you can optimize or secure anything, you have to see it. This involves pulling spend data from corporate cards, parsing SSO logs, crawling browser extensions, and syncing vendor APIs. The result is a living catalogue that tells you:
- Which apps are in use, by whom, and on what plan
- How much each team actually spends, including expensed ‘credit‑card IT’ (tools purchased without IT oversight)
- Where sensitive data flows outside the core stack
-
Spend Optimization: Insight without action still leaks cash. You’ll need to mine your discovered apps to identify:
- Dormant seats and orphaned accounts
- Duplicate functionality across tools
- Upcoming renewals with price‑increase clauses
Regularly auditing duplicate tools and unused licenses can save you thousands to millions a year.
-
Security & Compliance: Every unsanctioned domain widens the blast radius. A risk‑posture index grades apps on data scope, SSO/MFA status, vendor security attestations, and contract terms. This enables you to:
- Prioritize security reviews by actual exposure, not vendor size
- Prove MFA coverage during SOC 2 or ISO 27001 audits
- Auto‑quarantine apps that fail minimum‑viable controls
-
Workflow Automation: Manual provisioning holds back IT velocity. It’s important to automate SaaS lifecycle events, so that when an employee is hired, transferred, or off‑boarded, the right licenses appear—and disappear—automatically. Benefits:
- New hires are productive on day one, not day five
- Finance gets real‑time cost deltas when seats are added or removed
- IT tickets for “access requests” virtually disappear, freeing engineers for higher‑value work
- Alerts are set up for upcoming contract renewals
Here’s a visual of those four pillars and who they most impact:
| Pillar | C-Suite Lens | Core Output | Tangible Win |
|---|---|---|---|
| Discovery & Visibility | CIO | App inventory | $400K spend surfaced |
| Spend Optimization | CFO | SaaS Savings | 1.2% EBITDA lift |
| Security & Compliance | CISO | Risk index | Faster audits |
| Workflow Automation | IT Manager | Zero-touch flows | 160 support hours back |
What are the hidden costs of not having a SaaS management program?
The invoice total reflects only a fraction of the true cost of SaaS. Four hidden cost drivers account for the rest.
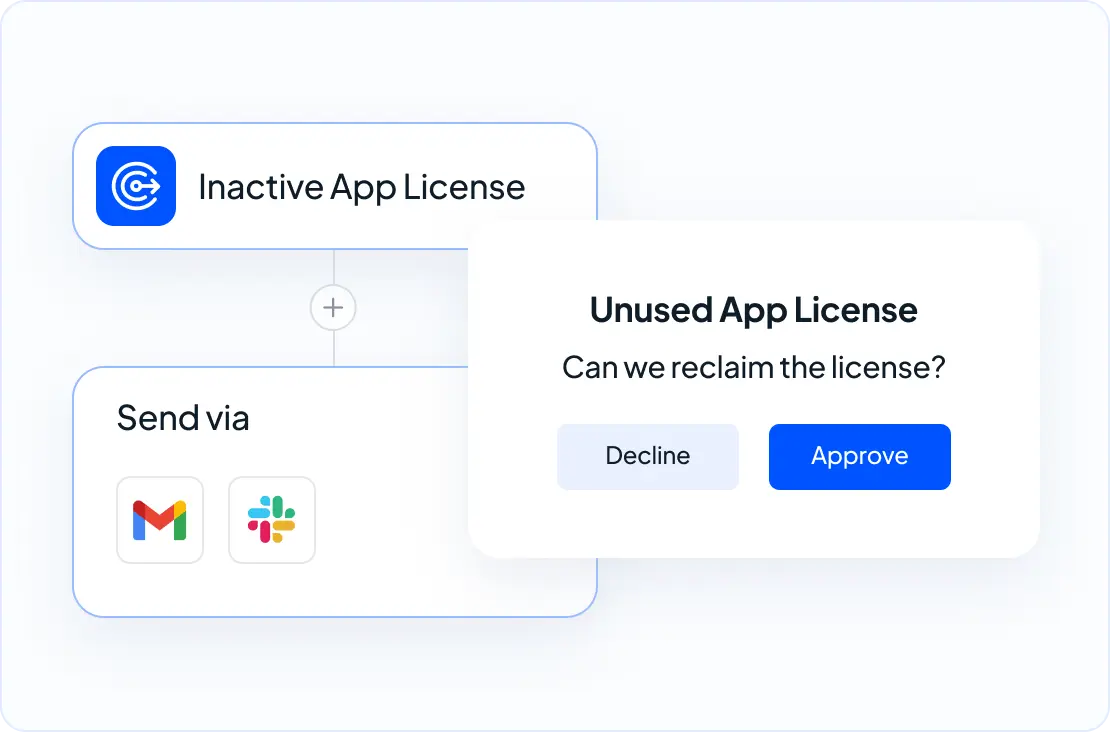
- Zombie licenses. Seats linger after role changes, time off, or departures. A 300-person firm paying $28 per Slack seat might carry 60 idle accounts, wasting $20,160 annually on unused seats.
- Duplicate tools. Marketing chooses Airtable, design goes with Monday.com, ops sticks to Smartsheet. Three workflows overlap at $12–$18 per user each month. Even with 40 shared users, the extra bill nears $8,000 a year.
-
Breach fallout. An app that bypassed security reviews raises incident odds. IBM put the average 2023 data-breach tab at $4.45 million. Even if just 1% of breach risk lands because of an unmonitored tool, the expected hit is about $44,500.
-
Context switching. Atlassian estimates a 9 percent productivity dip when employees juggle similar apps. For a $100,000 salary, that’s up to $9,000 in lost productivity per employee annually.
Add those up for a 100-person team and the “cheap” SaaS stack can drain more than $150,000 before the CFO spots the leak. For example:
| Item | Likelihood | Impact | Annual Cost | Owner | Mitigation Action |
|---|---|---|---|---|---|
| Zombie licenses | High | Med | $20,160 | IT | Quarterly review |
| Duplicate tools | Med | Med | $8,000 | Ops | Combine platform |
| Unvetted SaaS | Low | High | $44,500 | Sec | Add to SSO + MFA |
| Context switching | High | Med | $90,000 | HR | Standardize workflow |
10 Critical SaaS Management Mistakes (And How to Avoid Them)
Even with the best intentions, companies make predictable mistakes when managing SaaS. Here are the most costly errors and how to prevent them:
1. Over-Relying on SSO Logs for Discovery
The Mistake: Thinking SSO captures everything
- Many employees use personal accounts for work tools
- Mobile-only apps often bypass SSO entirely
- Free trials and freemium tools don’t appear in SSO logs
The Fix: Use multiple discovery methods
- Credit card monitoring for financial transactions
- Browser extension data for web-based tools
- Email scanning for SaaS signup confirmations
- Network traffic analysis for API usage
2. Ignoring Mobile-Only SaaS Applications
The Mistake: Focusing only on desktop/web applications
- Mobile productivity apps (Notion, Slack mobile)
- Field service tools used by remote teams
- Mobile-first platforms (Instagram Business, TikTok Business)
The Fix: Include mobile device management in discovery
- Require mobile app approval through IT
- Use mobile device management (MDM) reporting
- Survey remote teams quarterly about mobile tool usage
3. Poor Vendor Relationship Management
The Mistake: Treating all vendors the same way
- Missing opportunities for volume discounts
- Poor communication during renewals
- No central contact management
The Fix: Tier vendor relationships by spend and importance
- Tier 1 ($50K+ annually): Quarterly business reviews, dedicated CSM relationship
- Tier 2 ($10K-$50K): Annual check-ins, renewal planning meetings
- Tier 3 (<$10K): Standard renewal process, minimal touch
4. Inadequate Change Management During Implementation
The Mistake: Rolling out SMP without user education
- Employees don’t understand new approval processes
- IT team overwhelmed with questions about new procedures
- Resistance to “yet another tool to learn”
The Fix: Plan communication strategy before implementation
- Week -2: Announce program with clear benefits explanation
- Week 0: Department lunch-and-learns about new processes
- Week 2: Follow-up surveys and process refinements
- Month 1: Success story sharing across teams
5. Setting Unrealistic Cost-Saving Expectations
The Mistake: Promising immediate 40%+ cost reductions
- Creates unrealistic expectations with finance team
- Focuses on cutting tools rather than optimizing usage
- Ignores the time needed for behavior change
The Fix: Set progressive savings targets
- Quarter 1: 5-10% savings through obvious waste elimination
- Quarter 2: 10-15% through license optimization
- Quarter 3: 15-25% through workflow consolidation
- Year 1+: 20-30% sustainable savings through mature processes
6. Neglecting User Experience in Automation
The Mistake: Automating everything without considering user impact
- Over-restrictive approval workflows slow productivity
- Removing tools without providing suitable alternatives
- Complex processes that employees bypass
The Fix: Design automation around user needs
- Default to “yes” for low-risk, budget-approved tools
- Provide alternatives before removing existing tools
- Time-bound approvals (auto-approve after X days if no response)
7. Incomplete Offboarding Processes
The Mistake: Only deactivating SSO access during employee departures
- Contractor accounts often missed in offboarding
- Shared accounts continue running
- Data export/handover not planned
The Fix: Comprehensive offboarding checklist
- Day 0: Revoke SSO and primary accounts
- Week 1: Review and transfer ownership of shared accounts
- Week 2: Cancel/transfer personal subscriptions paid by company
- Month 1: Verify all access has been removed via audit
8. Not Planning for Shadow AI Tools
The Mistake: Applying traditional SaaS policies to AI platforms
- ChatGPT, Claude, and other AI tools have different risk profiles
- Data input policies need special consideration
- Usage monitoring is more complex
The Fix: Create AI-specific governance policies
- Approved AI tools list with data handling guidelines
- Prohibited data types (customer info, code, financials)
- Business use cases where AI tools are encouraged vs. restricted
9. Focusing Only on Cost, Ignoring Value
The Mistake: Measuring success purely by spend reduction
- Cutting tools that drive revenue growth
- Ignoring productivity gains from new platforms
- Missing opportunities for tool consolidation that improves workflows
The Fix: Balance cost and value metrics
- Productivity impact: Time saved through automation
- Revenue attribution: Tools that directly support sales/marketing
- Employee satisfaction: Quarterly surveys on tool effectiveness
- Process efficiency: Workflow improvements from tool integration
10. Lack of Continuous Monitoring
The Mistake: Treating SaaS management as a one-time project
- Initial cleanup followed by neglect
- No ongoing optimization of license counts
- Missing new shadow IT as company grows
The Fix: Establish “always-on” monitoring rhythms
- Weekly: New app discovery alerts review
- Monthly: License utilization optimization
- Quarterly: Vendor relationship reviews and renewal planning
- Annually: Full program assessment and strategy updates
Can I DIY SaaS Management?
If you’re a ten-person company with 20 total SaaS tools, then, yes. A Google Sheet would work fine. You might occasionally miss a renewal or delay an offboarding task, but those risks may not justify the cost of an SMP—yet.
But the risks of the spreadsheet approach increase substantially as your team grows. Even if you fully catalog your stack in February, will you check it weekly for renewal dates? Will you notice when employees sign up for tools they never report?
Can I use legacy software tools for SaaS Management?
A spreadsheet finds a line item here or there. SSO tracks sign-ins. SAMs are great for on-premise software. ITAMs can help with workflow automation.
But none of these historical tools are holistic solutions to the pillars identified above.
| Layer | Function | Who Covers It Well | What They Miss |
|---|---|---|---|
| Discovery | See every live app and user | SSO, CASB | Apps without SSO, shadow trials, card-based buys |
| Automation | Map rights to people or teams | SAM, ITAM | Real-time seat use, usage tiers, auto-renew terms |
| Control | Act on data, buy, cut, off-board | Expense tools, finance bots | Security posture, license swaps, workflow rules |
Rely on legacy tools and blind spots emerge quickly.
-
SAM (Software Asset Manager): Solid for Windows installs. Without live license meters, a quiet Slack workspace with 200 unused seats keeps burning cash.
-
ITAM (IT Asset Manager): Follows serial numbers and servers. Misses browser-only tools and freemium upgrades that flip to paid with no PO.
-
SSO (Single Sign On): Captures access events. Ignores per-seat cost and renewal dates; security enables MFA. Finance, meanwhile, keeps paying for former employees.
-
CASB (Cloud Access Security Broker): Alerts on risky data flows. Cannot renegotiate contracts or remove duplicate tools.
-
Expense systems (like Quickbooks): They alert you after the spend happens, when it’s too late to fix upstream problems like unused licenses or poor adoption.
What is a SaaS Management Platform?
A SaaS Management Platform (SMP) is a SaaS tool that offers you visibility and control over your company’s SaaS stack. These platforms connect to your existing IT, finance, and HR systems to monitor app usage, surface cost savings, reduce risk, and automate SaaS operations.
Unlike spreadsheets or point solutions, SMPs continuously map your entire SaaS ecosystem - tools, users, licenses, and spend - without manual upkeep.
SaaS Management Platforms address the four pillars above:
-
Discovery & Visibility: SMPs generally run agentless discovery across network, SSO, finance, browser extensions, and HR sources. They re-run in real-time, ensuring any new apps are unearthed.
-
Spend Optimization: Algorithms link every user, license, and cost center. Dashboards highlight duplicate tool usage and opportunities for reducing spend.
-
Security & Compliance: All tools are monitored and given risk ratings. Unauthorized and high-risk applications are surfaced immediately to the IT and security team for review.
-
Workflow Automation: SMPs have integrations with the individual SaaS tools, so that if you wanted to set a rule that any new employee would automatically get Notion and ChatGPT access, you could create workflows that automate those steps.
How do SMPs work?
A SaaS Management Platform pulls every subscription, license, and user into one dashboard. Instead of hunting through cards, spreadsheets, or payment gateways, teams open just a single UI. By combining the four pillars of discovery, spend, security, and automation into one console, an SMP turns raw logs into useful answers: who owns an app, what it costs, and whether it meets policy.
Here is the common flow inside most of these tools:
- You connect data sources
- Admin grants read access to IdP logs like Okta or Microsoft Entra
- Finance links expense feeds from NetSuite or SAP
- IT adds browser plug-ins and email scanners for last-mile discovery
- The SMP normalizes and enriches the data
- A backend map matches “Zoom.us,” “Zoom Video,” and “ZM” to one record
- License tables pull in plan tiers, seat caps, and renewal dates
- Risk scores tag apps lacking SAML or SOC 2
- Dashboards surface insights
- Dashboards rank spend and usage
- Alerts highlight duplicate spend or unused licenses
- High-risk apps identified
- Workflows and alerts offer control over your stack
- Drag-and-drop workflows for automating IT tasks
- One button removal of licenses across various tools
- Renewals post to calendars 90 days out
- Ongoing monitoring of new apps for Shadow IT tracking
- User alerts for employees to engage themselves
SMPs often get mentioned alongside other tools, yet, as we talk about above, each of those covers only part of the job.
- CASB watches traffic for unsanctioned SaaS but stops short of cost work.
- ITAM tracks perpetual licenses for on-prem gear; it misses frequent SaaS swaps.
- Expense-management apps flag large charges; they lack user and security context.
An SMP bridges those gaps by combining spend, access, and risk in one schema.
Teams usually begin with discovery, then turn on cost and security modules as data quality improves. With that base in place, off-boarding, rightsizing, and vendor scorecards run on autopilot, cutting waste and tightening controls well before the next audit season.
How to Successfully Implement a SaaS Management Platform (6-Week Guide)
Follow this proven 6-week implementation roadmap to maximize ROI from your SaaS Management Platform:
Building Cross-Functional SaaS Governance Teams
Successful SaaS management requires coordination across departments. Here’s how to structure governance that actually works:
Core Governance Team Roles
SaaS Program Owner (IT): Single point of accountability
- Responsibilities: Coordinate weekly governance meetings, escalate policy violations, maintain SMP
- Success Metric: Overall program KPIs, team satisfaction scores
Financial Controller (Finance): Budget and contract oversight
- Responsibilities: Budget allocation, renewal approvals, vendor negotiations
- Success Metric: Cost optimization targets, contract compliance
Security Lead (Security): Risk assessment and compliance
- Responsibilities: Security reviews, compliance audits, risk scoring
- Success Metric: Security KPIs, incident response times
People Operations (HR): Lifecycle automation
- Responsibilities: Onboarding/offboarding workflows, access policies
- Success Metric: Provisioning speed, employee satisfaction
SaaS Approval Workflow by Spend Tier
Tier 1 ($0-$100/month): Department head approval only
- Timeline: Same-day approval via Slack workflow
- Requirements: Basic security questionnaire, budget confirmation
Tier 2 ($100-$1,000/month): IT + Finance approval required
- Timeline: 3-5 business days
- Requirements: Security review, contract terms review, ROI justification
Tier 3 ($1,000+/month): Full governance team review
- Timeline: 1-2 weeks
- Requirements: Vendor security assessment, legal review, competitive analysis
Monthly Governance Meeting Agenda
Month 1: Discovery Review (30 min)
- New apps discovered via SMP
- Shadow IT findings and risk assessment
- Department app owner assignments
Month 2: Financial Review (30 min)
- Spend analysis vs. budget
- Upcoming renewals (next 90 days)
- Cost optimization opportunities
Month 3: Security & Compliance (30 min)
- Security score updates
- Compliance gap analysis
- Vendor security incident reviews
Escalation Procedures for Shadow IT
Low Risk Apps (productivity tools, design software):
- Process: IT reviews and approves or provides approved alternative
- Timeline: 48 hours
Medium Risk Apps (data processing, communications):
- Process: Security review required, may need data processing agreement
- Timeline: 5-7 business days
High Risk Apps (financial, customer data access):
- Process: Full security assessment, legal review, immediate access revocation pending approval
- Timeline: 2-3 weeks
Success Metrics for Cross-Functional Teams
IT Success: Reduced support tickets, faster provisioning
Finance Success: Budget predictability, cost savings achieved
Security Success: Improved compliance scores, faster incident response
HR Success: Employee satisfaction with access, onboarding efficiency
Pre-launch: Build the core team
Pick four owners: one each from Finance, IT, HR, and Security. They meet twice a week until the SMP is fully deployed. They will decide what tools to connect the SMP to (Okta, Quickbooks, etc.).
Week 1: Connect the applications
Department leaders will connect the important discovery tools to the SMP, enabling it to scour records to create a single SaaS source-of-truth.
Week 2: Associate SaaS tools with owners
Department leaders will then need to identify who in the company is the app owner for each app, and tag that in the SMP. This is a needed step so people have a point-of-contact for questions.
Week 3: Cut wasted SaaS spend
Now that you have full SaaS visibility, your team can dive into the numbers and make actionable decisions, such as:
- Identify apps that have unused licenses (which you pay for) and reclaim those
- Find tools you have multiple subscriptions for and which could be combined into a single plan
- Discover similar apps (like paid Evernote and paid Notion plans) that could be combined into just one tool
Week 4: Set up alerts
Add rules to the SMP to ensure the department leaders are getting notified of key events, such as contract renewal alerts for Finance and shadow IT alerts for security.
Week 5: Set up workflow automation
Now that the discoverability and alerts are set up, the IT team can work on building out automation to make their lives easier. This could involve detailed on-boarding workflows with 5-15 steps such as:
- Adding the person to certain Slack channels
- Automatically creating a Notion page for them
- Auto-provisioning them for a Salesforce account
- Email welcoming them
- And more
Week 6+: Set on autopilot
From here, the SMP should be constantly on, monitoring for new apps and surfacing any opportunities for spend improvements.
Do I have to maintain a SMP?
It’s important to remember that you can’t fully offload SaaS management to a third-party tool. An SMP may be able to discover high-risk apps, but it won’t be able to know if, say, you have an internal policy not to use Salesforce.
It’s important, then, to continue having quick syncs with Finance, IT, Security, and HR. The agenda never changes: check the live app dashboard, approve upcoming renewals, and call out risks that need a dive. Simple, predictable, and run by a single facilitator.
Indeed, strong programs rely on “evergreen hygiene cycles”.
- Monthly: refresh the app inventory, remove idle seats, check open support tickets
- Quarterly: rate every vendor on cost, risk, and adoption, then roll the scores into budget planning
- Annual: compare spend per employee to industry data, update policies, and test the offboarding flow front to back
Blend key SaaS metrics into dashboards that already exist. If the CIO publishes uptime stats in ServiceNow, slot license usage beside them. If FP&A looks at cash burn every Friday, add a chart of renewals due within 90 days. When teams spot the data where they already work, the message resonates.
Essential SaaS Management KPIs to Track in 2025
Measuring SaaS management success requires tracking the right metrics. Here are the key performance indicators that leading organizations monitor:
Financial KPIs
Cost Per Employee: Track total SaaS spend divided by headcount
- Industry Benchmark: $3,000-$5,000 per employee annually for mid-market companies
- Good Target: 15-20% below industry average through optimization
SaaS Waste Percentage: Unused licenses + duplicate tools as % of total spend
- Industry Benchmark: 20-35% waste is common without management
- Good Target: Less than 10% waste with active SMP monitoring
Cost Avoidance: Money saved through SaaS management activities
- Track: Duplicate subscriptions eliminated, unused licenses reclaimed, better renewal negotiations
- Good Target: 20-30% annual savings vs. unmanaged baseline
Operational KPIs
Time to Provision: Average days to grant new hire access to required tools
- Without SMP: 3-7 days typical
- With Automation: Same-day or next-day access
Shadow IT Discovery Rate: New unmanaged apps found monthly
- Industry Benchmark: 5-15 new apps discovered monthly per 100 employees
- Good Target: Consistent decline as governance improves
License Utilization Rate: Active users ÷ purchased licenses
- Industry Benchmark: 60-70% utilization is typical
- Good Target: 85%+ utilization across major tools
Security & Compliance KPIs
Security Score: Percentage of apps meeting security requirements
- Track: SOC2, SAML/SSO, MFA coverage, data residency compliance
- Good Target: 90%+ of business-critical apps compliant
Mean Time to Offboard: Hours to revoke access after employee departure
- Manual Process: 24-72 hours typical
- Automated: 1-4 hours with workflow automation
Risk Exposure: Number of high-risk apps in use without approval
- Good Target: Zero tolerance for high-risk apps handling sensitive data
User Experience KPIs
IT Ticket Reduction: Decrease in access-related support requests
- Common Result: 40-60% reduction in “can’t access” tickets
- Track: Before/after SMP implementation comparison
Employee Satisfaction: Survey scores for tool access and IT responsiveness
- Measure: Quarterly pulse surveys on IT service quality
- Good Target: 80%+ satisfaction with tool provisioning speed
Monthly KPI Dashboard Example
| Metric | Current | Target | Trend |
|---|---|---|---|
| Cost per Employee | $4,200 | $3,800 | ↓ |
| SaaS Waste % | 18% | <10% | ↓ |
| Time to Provision | 2.1 days | 1 day | ↓ |
| Security Score | 82% | 90% | ↑ |
| License Utilization | 76% | 85% | ↑ |
How can I choose the right SMP?
Choosing a SaaS management platform comes down to consistent results, not flashy demos. Below are some key features to look for in your SMP:
| Feature | ✅ |
|---|---|
| Broad discovery feed that merges SSO logs, card charges, and browser data | ☐ |
| Real-time license analytics by user, team, and daily cost | ☐ |
| Renewal calendar that pushes alerts to Slack or email, not just a dashboard | ☐ |
| Security scorecard covering SOC 2, SAML, MFA, data residency, and breach history | ☐ |
| Drag-and-drop automation connected to HRIS, ticketing, and chat tools | ☐ |
| Open APIs plus pre-built connectors for ERP, ITSM, and SIEM | ☐ |
Apply the same scrutiny to privacy: confirm where data sits, how long it stays, and who controls the keys. Evaluate customer success as well. Top providers assign a named representative and supply a 90-day playbook instead of pointing you to a generic inbox.
Price counts, but only once accuracy and trust are confirmed. A bargain headline fades quickly when extra charges appear for connectors or API calls. Ask vendors for a three-year cost sheet that factors in storage overages and new user tiers. If the numbers are fuzzy, flag them.
Below is a straightforward scoring matrix to keep the conversation grounded. Update it after every meeting.
Criterion Weight Vendor A Vendor B Vendor C
Discovery depth 20% 8 7 9
License analytics 15% 9 6 8
Security controls 20% 7 9 6
Automation builder 15% 6 8 7
API coverage 10% 9 5 8
Customer success 10% 8 4 7
Total score 100% 7.7 6.6 7.6
Many teams skip a pilot, but don’t. Choose a small business unit, hook up the core systems, and watch the data for two weeks. Any false positives or stale usage counts you uncover now will save headaches during a full rollout.
The top 5 SaaS Management vendors
Below is a breakdown of five leading SaaS Management Platforms.
Torii

Starting Price: Custom pricing (typically $3-8 per employee/month)
Best For: Mid-market companies (100-1000 employees) seeking comprehensive SaaS management
Torii is a SaaS Management Platform that unifies the SaaS needs of IT, Finance, Security, and HR - all in one place. Unlike other tools that focus on certain departments, Torii provides one platform for Finance to save money, IT to manage licenses, HR to onboard, and Security to monitor risk.
Pros:
- One tool that ties together what Finance, HR, Security, and IT want from an SMP
- Shadow IT discovery through a chrome extension, not just through finance feeds
- Automations that anyone in the IT team can own
- AI-forward, with their own custom Torii chatbot and MCP integration
Trade-offs:
- Vendor price benchmarks are lighter than Zylo or Vendr, so won’t get as much visibility into whether you’re paying more or less than the industry average
- Not as feature-heavy in the identity governance space
Productiv
Starting Price: Enterprise-level pricing (contact for quote)
Best For: Large enterprises (1000+ employees) with complex procurement needs
Productiv helps enterprises manage their software portfolios by combining employee usage data with contract information. The platform is geared toward procurement and finance teams, helping them with cost savings.
Pros:
- Best-in-class spend management and contract negotiation capabilities
- Top industry scores for spend and renewal management
- Strong integrations with enterprise systems
Trade-offs:
- Less focused on IT automation, so not an ideal tool for companies who want user lifecycle automation
- Shadow IT and risk management tools are less feature-heavy as spend management ones
Zylo
Starting Price: Enterprise pricing (typically $5-10 per employee/month)
Best For: Enterprise organizations focused on spend optimization and benchmarking
Zylo is an enterprise SaaS Management Platform that helps companies discover, manage, and optimize their software portfolios. The platform excels at SSO-based app discovery and provides deep benchmark data for contract negotiations.
Pros:
- Intuitive dashboard for identifying redundant spending
- Extensive benchmark data for SaaS spend
Trade-offs:
- Not an IT automation tool; focused on spend management
- Heavy dependence on SSO integrations for discovery, which limits real-time discovery
Bettercloud
Starting Price: $4-6 per employee/month
Best For: IT teams prioritizing user lifecycle automation
Bettercloud positions itself as the first end-to-end solution for IT teams to manage the SaaS user lifecycle. They provide centralized control of SaaS tools through a no-code workflow.
Pros:
- Excels at onboarding and offboarding automation
- Deep integration with core business tools like Google Workspace, Slack, and Salesforce
- Easy-to-use workflow builder
Trade-offs:
- Limited third-party integrations for niche SaaS applications
- Focused mainly on IT teams; doesn’t provide as robust contract negotiation and Shadow IT risk management as other tools
Lumos
Starting Price: Custom pricing (enterprise-focused)
Best For: Security-first organizations prioritizing identity governance
Lumos considers itself the first autonomous identity SaaS Management Platform. They focus heavily on automating identity and access management, while also offering SaaS discovery and spend management.
Pros:
- Excels at Shadow IT discovery and ongoing access management
- Great SMP for Security teams
Trade-offs:
- While strong in governance and security, their IT automation and spend optimization features are not as robust as other leading SMPs
- Their third-party integrations have good coverage of business-critical tools, but not low-risk but high-spend platforms
AI-Powered SaaS Management: The 2025 Revolution
Artificial intelligence is transforming SaaS management from reactive to predictive. By 2025, 70% of SaaS companies will embed AI capabilities, making AI-powered management tools essential for staying competitive.
How AI Enhances SaaS Discovery
Modern AI algorithms can:
- Auto-categorize applications: Machine learning identifies app types, risk levels, and business functions without manual tagging
- Predict usage patterns: AI analyzes historical data to forecast which tools teams will need during busy periods
- Detect anomalies: Unusual spending spikes or access patterns trigger automatic alerts
- Smart duplicate detection: AI recognizes when “Zoom,” “Zoom.us,” and “ZM” refer to the same vendor across different data sources
AI-Driven Cost Optimization
Advanced SMPs now use AI to:
- Recommend rightsizing: Analyze actual usage vs. purchased licenses to suggest optimal seat counts
- Predict renewal negotiations: Machine learning models suggest the best time to renegotiate based on usage trends
- Automate budget allocation: AI distributes SaaS costs across departments based on actual usage data
- Flag risky renewals: Identify contracts with low adoption rates before auto-renewal dates
Intelligent Security Risk Assessment
AI-powered security features include:
- Real-time risk scoring: Continuously updates app risk ratings based on new security incidents or compliance changes
- Behavioral analysis: Detects unusual user access patterns that might indicate compromised accounts
- Vendor security monitoring: Tracks security certifications and breach notifications across your entire vendor ecosystem
Managing Usage-Based and Hybrid SaaS Pricing Models
The shift toward consumption-based pricing is accelerating. 25% of companies now use usage-based pricing for AI features, with 22% adopting hybrid models that combine subscriptions with usage charges.
Common Usage-Based Pricing Models
API Call Pricing: Tools like OpenAI, Stripe, and Twilio charge per API request
- Challenge: Unpredictable monthly costs based on traffic spikes
- Management: Set spending limits and monitor usage in real-time
Data Processing: Platforms like Snowflake and Databricks charge for compute credits
- Challenge: Costs can spiral during heavy analytics workloads
- Management: Implement query optimization and scheduled processing
Storage-Based: Services charge for data volume stored or transferred
- Challenge: Data growth leads to exponential cost increases
- Management: Regular data cleanup and archiving policies
Tools for Usage Tracking
Most SMPs now include usage monitoring, but you may need additional tools:
- Cloud cost management: AWS Cost Explorer, Google Cloud Billing
- API monitoring: Datadog, New Relic for tracking API consumption
- Custom dashboards: Build alerts when usage approaches budget limits
What to expect from SaaS management moving forward
These are the most likely SaaS management changes in 2025-2027:
- The biggest change to SaaS management will be the proliferation of AI tools and consumption-based pricing (also called pay-as-you-go). Tracking Snowflake credits, OpenAI tokens, and pay-per-call APIs will become increasingly complex
- The rise of AI add-ons makes tracking SaaS costs more complex.
- SaaS tools previously reliant on licenses will test out consumption-based pricing
- AI protocols like MCP will make it easier to manage your SaaS tools directly from your chat widget
- Auditors will expect proof that every AI tool passes explainability and bias standards
Companies that invest in adaptive SaaS management platforms will stay ahead. Those that hold off may watch next quarter’s SaaS bill, security report, and compliance notes climb together.
Calculate Your SaaS Management ROI
Use our SaaS ROI Calculator to get precise savings estimates for your organization.
Quick ROI Estimator:
- Current annual SaaS spend: $__
- Potential savings (20-30%): $__
- SMP cost (avg $5/employee/month): $__
- Net annual savings: $__
Example: A 200-employee company spending $500K annually on SaaS could save $100-150K yearly, minus $12K in SMP costs = $88-138K net savings.
Audit your company’s SaaS usage today
If you’re interested in learning more about SaaS Management, let us know. Torii’s SaaS Management Platform can help you:
- Find hidden apps: Use AI to scan your entire company for unauthorized apps. Happens in real-time and is constantly running in the background.
- Cut costs: Save money by removing unused licenses and duplicate tools.
- Implement IT automation: Automate your IT tasks to save time and reduce errors - like offboarding and onboarding automation.
- Get contract renewal alerts: Ensure you don’t miss important contract renewals.
Torii is the all-in-one SaaS Management Platform, providing a single source of truth across Finance, IT, and Security.
You can learn more about Torii here.
Frequently Asked Questions
SaaS management is the process of discovering, managing, and optimizing software-as-a-service applications within an organization to reduce costs and enhance security.
SaaS management helps eliminate wasted spend, mitigate security risks, ease IT burdens, and avoid missed contract renewals.
An effective SaaS management plan should include discovery and visibility, spend optimization, security and compliance measures, and workflow automation.
Yes, small teams can use manual methods or spreadsheets for SaaS management, but as complexity grows, dedicated tools become necessary.
When selecting a SaaS Management Platform, ensure it offers comprehensive discovery, real-time analytics, renewal alerts, and robust security features.
Neglecting SaaS management can lead to costs from zombie licenses, duplicate tools, security breaches, and decreased employee productivity.
A SaaS Management Platform centralizes the management of subscriptions, licenses, and users while providing actionable insights for cost reduction and security improvements.

