The State of SaaS Visibility and Impact Report
Key Findings From This Report
Said Shadow IT is a top concern related to SaaS adoption
Have made exceptions to their SaaS security protocols
Are evaluating or planning to deploy SaaS management tools
Summary of the Findings
The new reality of distributed and remote work has driven Shadow IT to a whole new level, empowering employees to provision and manage their own cloud applications. While that’s allowed teams to innovate faster, it’s also led to increased security risk and a complete breakdown of old tools and methods for managing it. They weren’t designed for SaaS and the Shadow IT explosion, and simply cannot keep up. SaaS warrants a completely new approach. Businesses are beginning to realize this and take more effective measures for managing their SaaS stack and mitigating the risks.

Ever Since COVID...
Ever since Covid, organizations, and more specifically IT, have experienced a transition. They’ve become more agile, quickly adapting to remote and hybrid work models, while combating new and increasingly pressing security and compliance risks.
Notably, this shift to remote work and the rise in security concerns are connected. As teams became increasingly decentralized and remote, they relied more on cloud applications – or SaaS – to accomplish their work.
But, the full extent of COVID’s impact on SaaS-centric organizations has largely remained unknown.
That’s why Torii partnered with Pulse to survey 100 technology executives to find out just how much the pandemic, and SaaS, has impacted their day-to-day tasks and IT strategies.
Contents of the Report:
- Leadership is (Still) Unsure About the Role of Technology
- Application Adoption – The Tension of Autonomy and Control
- SaaS App Visibility and Security Risks are Top of Mind:
- Falling Short: Identity Access Management & Single Sign-On
- What Does This Mean for IT?
- SaaS Is Here to Stay – So How Can We Improve Security?
- SaaS Management Plans are in the Works
- Conclusion: The New Paradigm
- Still Have Questions? Download the Data Infographic
Leadership is (Still) Unsure About the Role of Technology
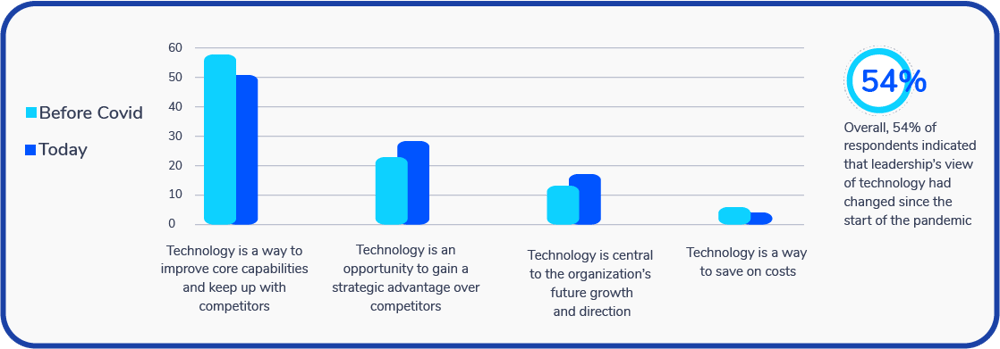
How does leadership view the role of technology within the company?
Key Finding: Over half (54%) of respondents report their company’s leadership views technology differently now than before the COVID-19 pandemic.
SaaS was once considered a way for IT to save money by avoiding the typical costs of installing and maintaining infrastructure and software; but today, that technology is central to the way we work. Employees now use SaaS to find new and creative ways to streamline their workflows and innovate.
In short, employees have become technologically-minded problem solvers, using an array of new, flashy, and efficient software to help bring their organizations into the 21st century.
Leadership is Finding Out What Their Employees Already Know
Interestingly enough, the COVID-19 pandemic has pushed leadership to recognize this powerful potential of their technology.
In fact, over half (54%) of respondents report their company’s leadership views technology differently now than before the COVID-19 pandemic, with 28% of respondents viewing their tech stacks as a strategic advantage, and 17% deeming SaaS as central to their organization’s future growth and direction.
Key Takeaway: Leadership is increasingly seeing tech as a proactive way to gain advantage and growth and decreasingly as a way to cut costs or reactively keep up with competitors.
In other words, executives are increasingly recognizing employees’ use of SaaS applications to drive ingenuity, streamline workflows, and even increase revenue.
Importantly, the increase in autonomous experimentation is also causing new security risks as it leads employees to experiment and test more applications without ever communicating with IT, thereby introducing new security risks.
Application Adoption – The Tension of Autonomy and Control
As more employees are experimenting and implementing new applications autonomously, the IT department is losing visibility.
We’ve actually found that the typical IT leader dramatically underestimates the number of applications within the company. The actual number is often three to six times higher than what they estimate.
Read More: Torii Infosheet – SaaS Insights, New Application Adoption
SaaS App Visibility and Security Risks are Top of Mind:
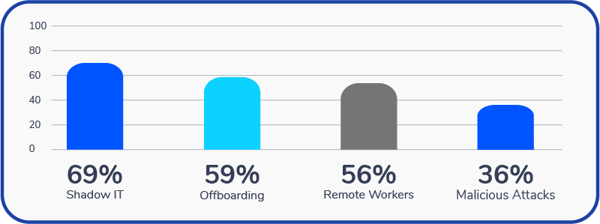
What are your top security concerns with relation to SaaS
Key Findings: The three biggest security-related concerns among tech executives include:
Shadow IT (69%)
Offboarding employees from applications (59%)
Remote workers exposing data (56%)
All of these security risks can be blamed on a lack of visibility. In short, your IT and/or security teams can’t manage what they can’t see. Therefore, lacking insight into your organization’s applications, how they’re used, and by whom, leaves your sensitive data and carefully-planned budgets at risk.
Consequently, employees’ rapid adoption of apps during the pandemic has led 41% of executives to report challenges with SaaS spend visibility and optimization as having the largest impact on how their organization operates.
To understand why, let’s take a look at the specific risks associated with the above security concerns.
1. Shadow IT:
Shadow IT refers to unsanctioned technology (or technology resources) that are used by employees without the IT department’s knowledge. Today, most Shadow IT takes the form of SaaS apps. This poses serious security and compliance risks for organizations whose sensitive data is constantly flowing through these applications but have no way to monitor its usage or combat security breaches.
Despite the security threats, Shadow IT isn’t going away. In fact, it is just increasing:
Key Findings:
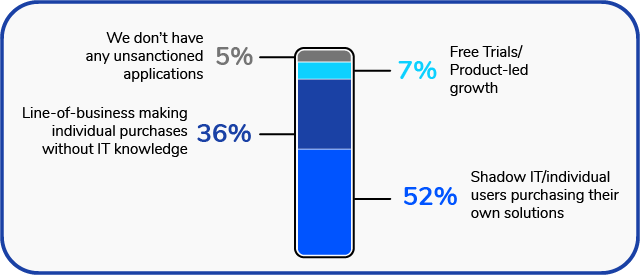
52% of survey respondents say individual employees are purchasing their own apps without IT’s knowledge
36% also reported the adoption of unsanctioned apps by line of business (LOB) managers
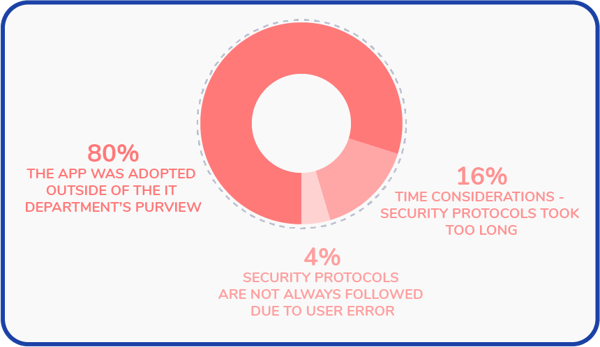
What is the main reason for your unsanctioned applications?
Because Shadow IT is a largely invisible issue (hence the name), it can be hard to identify its presence, let alone its costly, time-consuming impact—that is, until it’s too late.
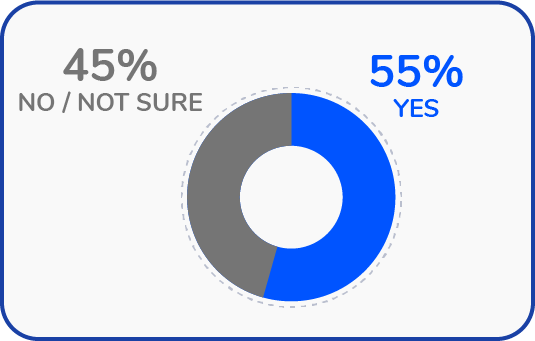
Key Findings: In fact, 55% of organizations have reported lapsing security protocols since the start of the pandemic, with 80% of these breaches being caused by applications adopted outside of IT’s purview.
Have you made exceptions to your security protocols for any of your SaaS applications?
Why were those exceptions to your security protocols made
Unfortunately, application adoption is not the only concern—Integrations also pose a significant security threat.
In addition to transforming employees into single-person procurement teams, SaaS has also turned everyone into a systems integrator. For example, an employee with access to Hubspot, Slack, GSuite, and other sanctioned apps can easily integrate them with other tools – some of which may fall under Shadow IT.
Key Takeaway: SaaS has turned everyone into a systems integrator!
If data flowing from unsanctioned to sanctioned apps is inaccurate or corrupted, it can compromise mission-critical data. Likewise, data flowing from sanctioned to unsanctioned apps is exposed in ways security teams are unaware of and, therefore, are unable to protect.
Important Note – The Value of Shadow IT: While the headline of this report reflects the concern with the security risks of unmonitored applications, Shadow IT can also represent value. Shadow IT, when properly monitored, is the result of creative and innovative teams trying things and driving value for the whole organization. The important aspect is mitigating threats while enabling that exciting experimentation. For more about how Shadow IT can also be a net good for the organization, read some of the resources below.
Read more about Shadow IT:
What is Shadow IT? [Three Steps to Take in 2022]
Shadow IT and SaaS Security: Are they Mutually Exclusive?
Shadow IT: The Good the Bad and the Ugly
One instance in which the risks of Shadow IT become painstakingly visible is during the employee offboarding process.
2. Offboarding:
As your organization adopts hundreds of applications, keeping track of them—let alone their users—quickly becomes an impossible task, especially without an Automated SaaS management platform to track this data for you.
For this reason, in many cases, organizations fail to offboard former employees from both Shadow IT and sanctioned applications. This means that offboarded employees can still access your organization’s apps and the sensitive data they contain. Your organization may also be at risk ofbreaking security and compliance regulations.
With this in mind, it’s unsurprising that 59% of executives consider offboarding and deprovisioning ex-employees “a top security concern.”.
Read More: [New Report] 76% of IT leaders say “Offboarding is a Significant Security Threat”
For those looking to fix their offboarding process, check out Torii’s IT Checklist for Employee Offboarding.
3. Remote Workers Exposing Data:
Although seemingly outdated, anxieties regarding remote work are actually warranted.
We’ve all heard horror stories about employees connecting to an unsecured network or falling victim to a phishing scam, leading to a massive and costly security breach.
With this in mind, as soon as your organization implements remote work options, an underlying anxiety is bound to form—how can your organization ensure its employees are accessing and disseminating sensitive data responsibly?
While it’s best practice to consistently educate your employees about securing their passwords, phishing scams, and other security threats, education alone cannot prevent all security breaches.
Unfortunately, the pandemic forced most organizations to adopt remote work before they had proper remote security protocols and tools in place.
Even so, simply implementing an Identity Access Management and/or Single Sign-On solution is not enough to secure your organization’s sensitive data.
Falling Short: Identity Access Management & Single Sign-On
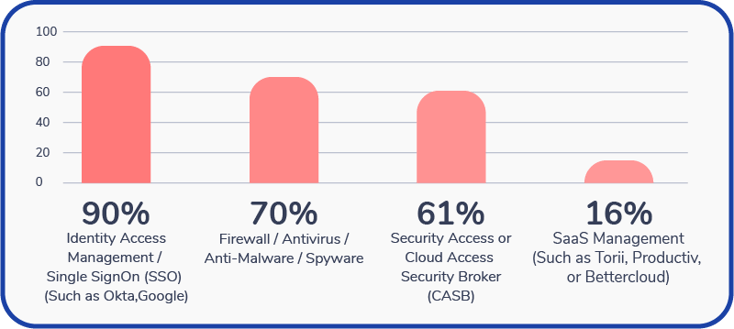
Key Findings: Despite high anxiety regarding Shadow IT, 90% of respondents reported using Identity Access Management (IAM or Single Sign-On (SSO).
Organizations have already adopted Identity Access Management (IAM) and Single Sign-On solutions (SSO) as a method of fortifying their sensitive data during a period of remote work and general uncertainty.
In fact, almost all survey respondents (90%) reported using Identity Access Management or Single Sign-On to reduce exposure to security threats.
Which of the following tools are you using within your organization to reduce exposure to security threats?
These applications add an additional layer of security and control to your organization’s SaaS login process, ensuring that only the right people have access to your tech stack.
Although implementing these solutions is a first great step to protecting your organization’s sensitive data, like most applications, IAM and SSO are not a silver bullet for all of your security needs.
IAM and SSO tools can only account for known (or sanctioned) applications. This means that they can’t uncover or have visibility into Shadow IT apps, which, as we’ve learned, pose some of the most serious security threats to your organization.
Key Takeaway: IAM and SSO tools are important for security, but they are not sufficient by themselves
One option that many organizations are taking is coupling their IAM and/or SSO solutions with a SaaS Management Platform. SaaS Management platforms uncover all of your organization’s apps, including those currently within Shadow IT.
Additionally, SaaS Management tools optimize your organization’s tech stack by eliminating Surprise SaaS Spend, unused licenses, and abandoned applications. Learn more about the benefits of pairing your SSO and SaaS Management solutions here.
Read more: 10 Things You Must Know Before Implementing a Single Sign-On (SSO) Solution.
What Does This Mean for IT?
IT’s Role Is Changing
Key Takeaway: Decentralized workflows and the rapid adoption of SaaS applications have forever transformed IT from tech stack gatekeepers to SaaS conductors.
IT no longer has sole control over application adoption. The impacts of SaaS, decentralization, and (most recently) the pandemic have pushed IT to re-evaluate their role within the organization.
Instead, many teams have turned their attention to becoming a SaaS orchestrators, helping all stakeholders from security, finance, procurement, and lines of business, get the most value from SaaS apps. All while controlling spend and de-risking SaaS adoption. Through this work, IT helps ensure that data remains accessible only to authorized users.
This way, employees can continue to innovate while IT ensures their organization’s data remains secure.
In fact, most executives consider management and control of the organization’s tech stack, and leading innovation to support business growth as valuable tasks, with 58% rating these tasks as 4 or 5 on a scale of 1 to 5.
This may be why most IT personnel (45%) have reported spending more time on valuable work since the shift to remote and hybrid arrangements.
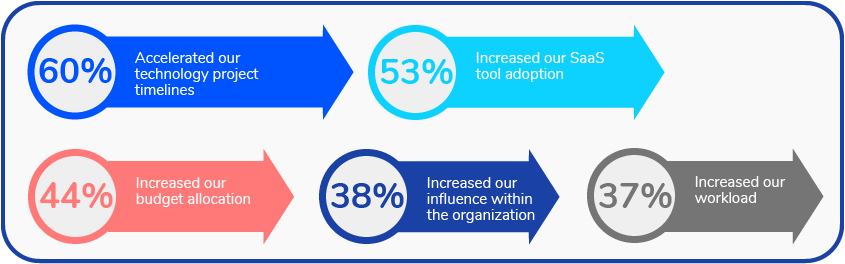
More SaaS, Faster Timelines, and Increased Budgets for IT
In addition to the shift in valuable and non-valuable work, respondents reported other changes. When asked about what specific ways the pandemic impacted, “Accelerated technology timelines” and “Increased SaaS tool adoption” topped the list (60% and 53%).
Other items included:
- 44% Increased budget allocation
- 38% Increased influence within the organization
- 37% Increased workload
Top 5 ways the pandemic impacted the IT department
Something of Note: Interestingly, while IT reported faster timelines, more tools, more budget, and more influence, only 37% of respondents noted an increase in workload.
IT’s Contributions are More Visible Than Ever Before
IT might struggle to maintain the visibility of its SaaS applications, but the rest of the company is finally noticing IT’s contributions.
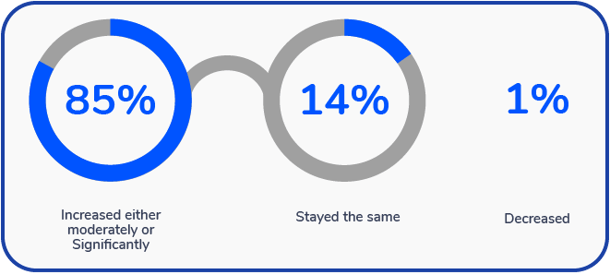
In fact, our research showed that 85% of IT teams feel that the changes due to the pandemic have increased the company’s visibility of IT contributions. 14% said it stayed the same, and only 1% of respondents claimed their visibility decreased.
How have the changes from the COVID-19 pandemic impacted your company’s visibility of IT contributions within the organization?
Despite Decentralization, IT Remains Involved in SaaS Purchasing
Much of this report focuses on how decentralization has spread the SaaS purchasing responsibilities across the organization. But, that doesn’t mean that IT is sitting on the sidelines.
When asked about who purchases the most SaaS applications within their organization, 89% of respondents said it was still IT. This shows that IT is still part of the process. Despite decentralization, IT still has valuable insight and knowledge that can help the rest of the organization make difficult decisions related to application selection.
However, it’s also worth noting that with Shadow IT, the question of “who purchases the most applications” is difficult to truly know. Without visibility to the rest of the organization, IT can only confidently know their own purchase actions. Not the rest of the organization. This leaves a significant opportunity for blindspots to occur.
With all of this in mind, what does the future hold for SaaS applications?
SaaS Is Here to Stay – So How Can We Improve Security?
Key Findings: 94% of respondents expect the number of SaaS apps in their company to continue to increase in the next two years
SaaS does include security risk, but the potential advantages make SaaS an inescapable center of gravity for the modern organization. In fact, 94% of survey respondents indicated that they expect the number of SaaS apps in their company to increase in the next two years.
SaaS Management Plans are in the Works
But, in order to uncover Shadow IT and better manage their growing SaaS stacks (and the risks associated with them), technology executives are implementing additional security measures. Respondents reported their plans to:
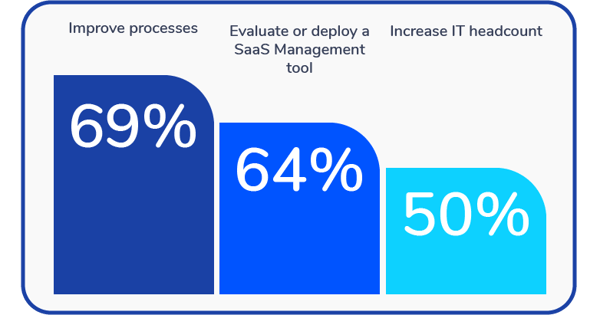
Does your organization plan to do any of the following to accommodate an increase in SaaS applications over the next two years?
- Improve processes (69%)
- Evaluate or deploy SaaS management tools (64%)
- This is in addition to the 16% who say they already use these tools
- Increase IT headcount (50%)
Conclusion: A New Paradigm
What can we conclude from these findings? There’s a lot to consider, but a handful of truths stand out.
- Decentralization is here and we haven’t really solved it
- Shadow IT and other security concerns are still top of mind
- The IT department has more prestige, budget, and resources to deal with these issues
For the IT department, the pandemic created a new almost paradoxical paradigm. One in which their contributions were more visible than ever, but their insight into the organization’s software was less visible than ever. However, as we move forward SaaS Management Tools, increased headcount, prestige, and budget allocation are available to IT to help gain back the insight they need.
Ultimately, this insight is the key. Better insight leads to smarter decisions. And, as our workplaces increasingly revolve around cloud applications, decisions about those apps become critical.
For the modern IT team they must prioritize visibility, optimization, and spend efficiency in order to lead their organizations in the cloud.