Non-human identities multiply fast.
Governance has to keep up.
Discover non-human identities beyond Active Directory and SSO, automatically assign owners, and automate governance.
Non-human identities multiply fast.
Accountability doesn’t.
Most “agents” aren’t agents at all. They’re bots recycling data data into flashy dashboards that leave security and IT teams in the dark.
That’s why we built Eko: the governance copilot that runs on continuous discovery and keeps you fully in control.

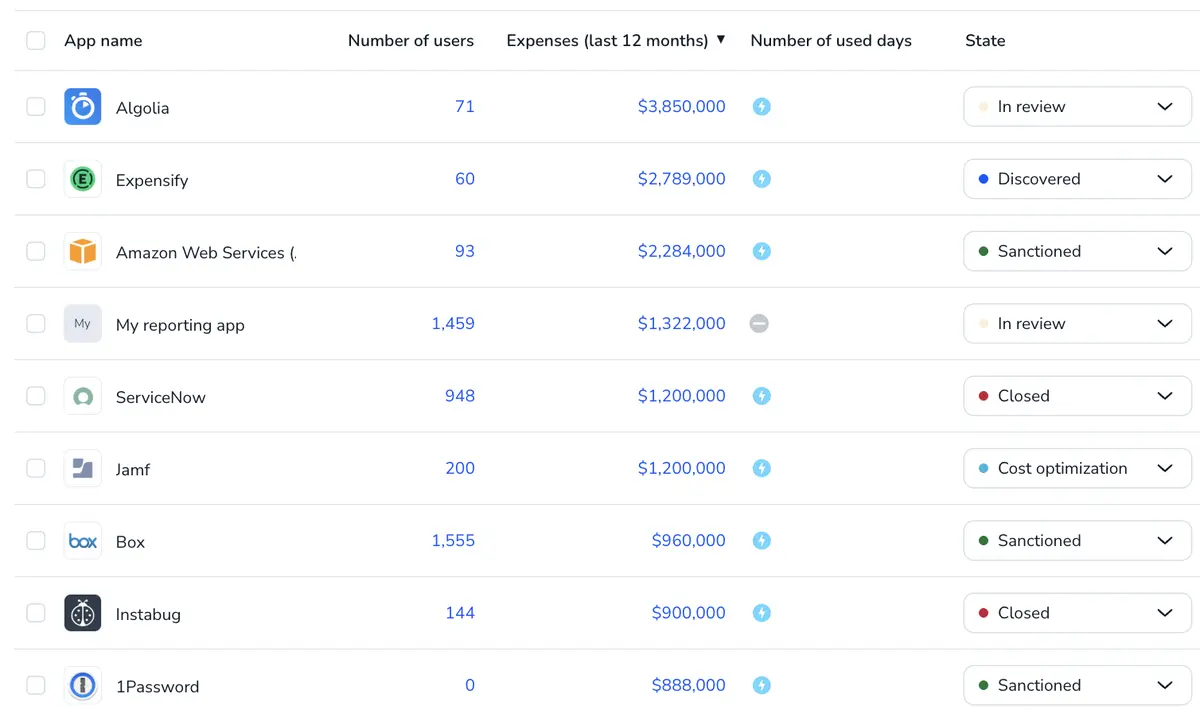
Discover non-human users beyond AD & SSO
Torii adds discovery layers others miss—so you capture the identities that never show up in a clean directory export.
- Multi-source discovery that starts at the browser
- MDM-based signals to surface identities and usage paths outside directory views
- Coverage across agents, bots, integrations, and service accounts
Auto-assign owners, enforce guardrails
Torii auto-assigns every non-human identity to the right owner—so governance stays accountable and scalable.
Automatically assign each NHI to its application owner—no manual triage
Delegate via the Task Hub—Security oversees, owners execute
Automatically reassign owners when people leave, so nothing goes unowned


Prioritize management with NHI risk scores
Torii assigns each NHI a risk score and delivers a prioritized list with reasoning—so the most exposed identities are addressed first.
Scores based on multiple signals like security posture, encryption, and vendor health
Get a prioritized list with reasoning so you know exactly why certain NHIs come first
Torii routes tasks to owners for action so issues are reviewed and resolved
Once we integrated Torii, it blew our minds. We found apps we didn’t even know we were using - or paying for.
Automate least-privilege enforcement
Torii automatically enforces least-privilege principles for NHIs—so you reduce risk without manual intervention.
Automatically adjust permissions to the minimum needed for each NHI
Enforce least-privilege policies continuously so no identity retains excessive access over time
Reduce manual workload by letting Torii handle permission cleanup automatically


Detect risk patterns & the policies to fix them
Eko, your governance copilot, identifies patterns of risky NHI adoption and usage, then suggests policies that prevent those risks at their source—so you can enforce lasting solutions.
Get evidence-based recommendations with drillable data for full context
See clear, natural-language explanations of the policy reasoning
Chat with your data to explore insights and confidently approve solutions
Audit ready by design
Torii automatically logs every NHI action and policy decision, providing a complete audit trail that keeps you compliant and ready for review.
Maintain a full audit trail of all changes and actions automatically
Easily access and share records for compliance checks and audits
Demonstrate governance and accountability with transparent, tamper-proof logs

Ready to get non-human identities under control?
Discover non-human identities beyond Active Directory and SSO, automatically assign owners, and automate governance.
Frequently Asked Questions
What are non-human identities (NHIs)?
Non-human identities (NHIs) are identities used by software—agents, bots, service accounts, integrations, and machine identities—that authenticate and perform actions without a person behind each login.
How does Torii discover NHIs others miss?
Torii uses additional discovery layers, including browser and MDM signals, to detect identities that AD/SSO-only approaches don’t capture.
What goes into Torii’s NHI risk scores?
Risk scores are based on multiple signals, including but not limited to, compliance and encryption indicators, plus incident-related signals and status changes used to prioritize remediation.