The Top 9 Employee Offboarding Tasks For IT in 2026
An employee’s final day can quickly turn into an IT security headache. Without a repeatable offboarding playbook, abandoned SaaS seats, lingering API tokens, and forgotten admin rights drive up costs and open security gaps. IT leaders need a clear checklist that shuts every digital door the minute a departure is announced.
Offboarding usually stretches across more systems than most teams expect. Cloud directories, dozens of subscription dashboards, shadow-IT purchases, and personal developer keys all hold pieces of the same access puzzle. Miss one piece, and the entire effort weakens. By treating offboarding as nine linked tasks, inventory, revoke, disable, secure, audit, and four more, teams move from confusion to routine control.
This guide breaks down those nine tasks in order, giving IT operators a practical, verifiable, ready-on-day-one blueprint for secure, cost-efficient employee offboarding.
Table of Contents
- Inventory all SaaS access
- Revoke user licenses promptly
- Disable IdP accounts and MFA
- Deactivate native SaaS accounts
- Transfer data ownership
- Rotate or revoke API tokens
- Audit and archive offboarding actions
- Conclusion
Inventory all SaaS access
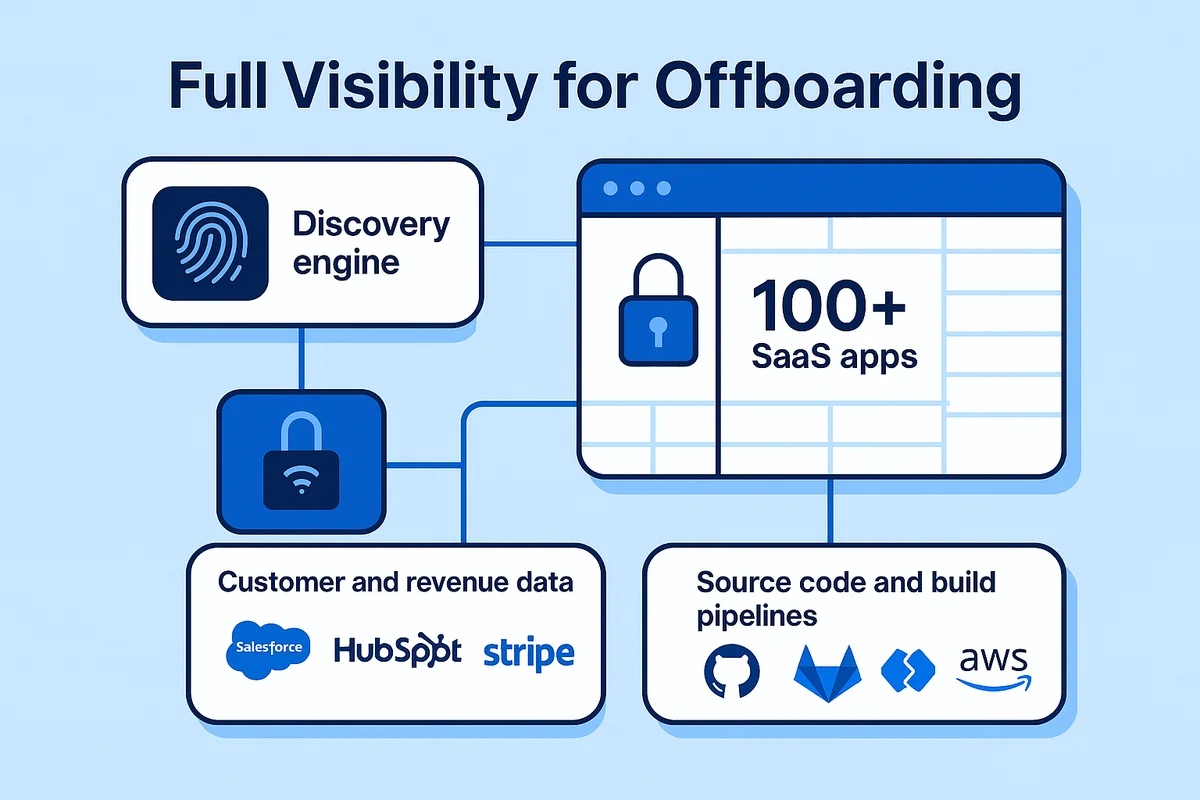
A clean offboarding starts with knowing where an employee’s digital fingerprints live. Gartner says midsize firms juggle roughly 125 SaaS tools, so a single exit can ripple across dozens of consoles. Miss even one and the worker keeps a door key while finance still pays.
Full visibility comes fastest from a discovery engine that watches sign-on events and billing feeds together. An IdP export from Okta can pull every app, role, shared account, and lingering API key tied to the user. Add a finance ledger or corporate card feed to surface the marketing pilot bought last quarter but never logged with IT. Finally, Shadow-IT scans flag SaaS domains the IdP missed when employees signed in with Google or Microsoft social auth.
Before you move on, tag any system that would cause real pain if left open. Then sort the sheet so those high-risk targets sit at the top:
- Customer and revenue data: Salesforce, HubSpot, Stripe
- Source code and build pipelines: GitHub, GitLab, AWS
- Financial or HR records: NetSuite, Workday
Tagging does two jobs. It guides the operator to shut off critical access in the next step before licenses or tokens can be copied. Second, it tells finance which subscriptions will free up real money when seats are reclaimed.
The main output from this phase is a single, timestamped “access map” in a shared folder, nothing fancy, just definitive. Each row shows the app name, user identifier, permission level, renewal date, and whether the account links back to SSO. Because every later task depends on this file, insist that a second admin spot-checks at least three entries for accuracy. A tidy list now saves a frantic audit later when someone asks, “Did we also catch the personal Auth0 token?”
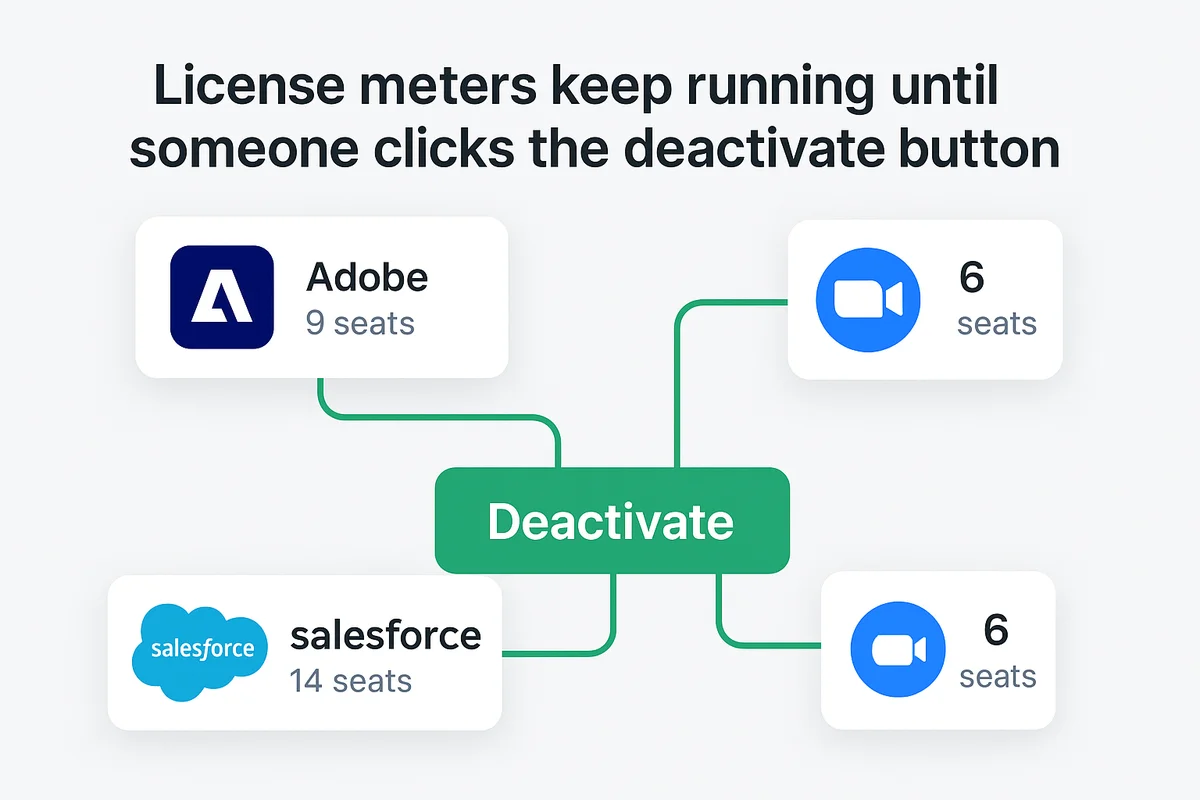
Revoke user licenses promptly
License meters keep running until someone clicks the deactivate button. That single click feels trivial, yet each minute of delay racks up charges or leaves a seat a former employee could exploit. Nobody wants to explain on the next finance call why nine leftover Creative Cloud seats added another $600.
Start by grabbing the seat counts surfaced in your access map spreadsheet. If the employee held several product bundles, break those out so you can unlink only what they used and leave shared modules untouched.
- Remove the user from Adobe Creative Cloud first, where hourly proration stops as soon as you free the seat.
- Open the Salesforce “Manage Users” view and toggle both license and permission set assignments, otherwise they linger separately.
- In Zoom, revoke the Pro seat, then cancel any scheduled meetings that would auto-reinstate it.
- For Microsoft 365, switch the license to a “coupler” account you control before deletion so OneDrive content stays reachable.
Timing each removal alongside HR’s exit clock avoids gaps attackers love. Line up the license taps with the departure checklist so no orphaned seats linger past the badge swipe.
Manual clicks work, yet scripting the vendor APIs keeps late-night departures safe. The Adobe Admin Console, Salesforce REST endpoints, and Google Workspace Directory API all accept a simple PATCH call to drop a license, and you can stack those calls in a single playbook that fires the instant HR updates the employee status field. Build a dry-run flag so finance can preview seat changes without committing them.
Some licenses refuse to disappear even after you remove the user. Annual prepaid contracts, bundled SKUs, or seats granted through a partner marketplace may stay active until the term renews. When that happens, move the license to a pool or training account so you still capture the value, document the block in your offboarding ticket, and set a calendar reminder to cancel at renewal. Always export the final seat roster after the dust settles; finance will need it when the next invoice lands.
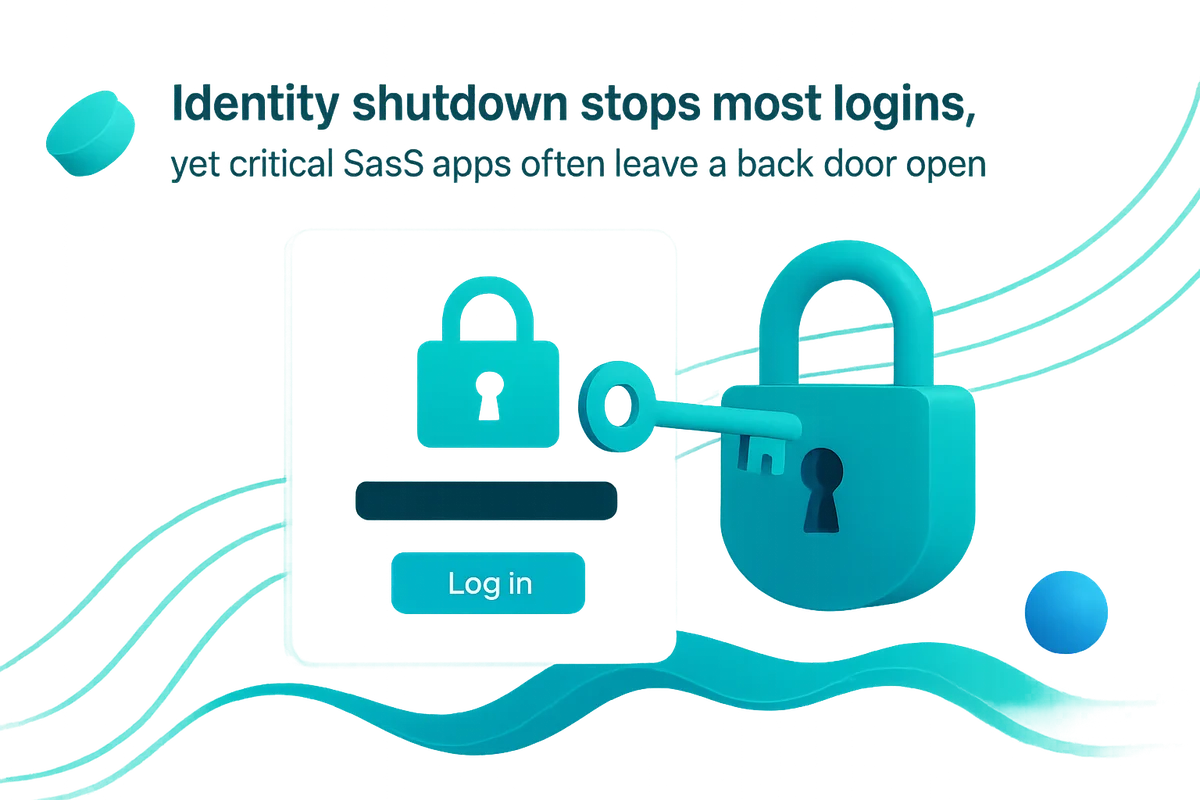
Disable IdP accounts and MFA
Most breaches start with stale user accounts that nobody remembered to turn off. Shutting that door at the directory level blocks dozens of SaaS windows from opening later.
Suspending or deleting a user in Azure AD, Google Workspace, or Okta cuts off the main sign-in routes, but only if the task finishes cleanly. Pick “block sign-in” or “suspend” when someone is on garden leave. Use “delete” once Legal and HR confirm the exit is final, because deleting the account revokes refresh tokens that a simple password reset leaves alive. The 2023 Verizon DBIR notes that 19 percent of insider incidents involve lingering credentials, so timing the change for the employee’s final minutes is worth the calendar reminder.
Token residue hides in phones, laptops, and browser caches, so the job is not done until every factor tied to the directory record is voided. Common misses include FIDO2 security keys registered for passwordless logins, push-based MFA pairs in Microsoft Authenticator, and recovery codes printed during onboarding. Handle them in bulk:
- Remove phishing-resistant keys by clearing the
StrongAuthenticationMethodsfield. - Wipe push factors with the “reset multifactor” command before the account is disabled.
- Regenerate emergency access codes; never leave them unchanged for the next hire.
Once the directory entry is gone, the cleanup still has to propagate. Downstream SaaS platforms connected through SCIM or JIT provisioning may cache accounts for hours, and some, like Slack, wait for a webhook confirmation before disabling a session. Queue a background sync immediately after the directory change, then verify the result with an identity governance report. If any app logs show the departed email address requesting new tokens after deactivation, the sync failed and manual intervention becomes the fastest fix.
Finally, export a snapshot of the user object (groups, roles, MFA status) before deletion so auditors can trace why access disappeared. The snapshot slides straight into your SIEM and saves the security team from guessing during a future incident review.

Deactivate native SaaS accounts
Identity shutdown stops most logins, yet critical SaaS apps often leave a back door open. These platforms still accept local passwords, magic-link emails, or cached browser sessions that cruise past your disabled IdP. If the departing engineer still has a laptop on in-flight Wi-Fi, one click could touch production data before midnight.
Start by listing the key systems and opening each admin console. For GitHub and Bitbucket, search by username, then flip the role to suspended rather than delete so pull requests stay intact. AWS needs deeper digging because users can hold both an IAM login profile and one or more long-lived console sessions; clearing the console sessions blocks the active cookies at once. Salesforce, monday.com, and QuickBooks keep local credentials even when SSO is on, so force a password reset, then set the “requires password change at next login” flag to false, ensuring the user never sees that next login screen.
Here are the most common hotspots you’ll want to cover during the shutdown:
- Source code and build automation: GitHub, GitLab, Bitbucket, CircleCI
- Cloud and infrastructure: AWS, Google Cloud, Azure Portal, Cloudflare
- Customer data: Salesforce, HubSpot, Zendesk, Stripe
- Finance and reporting: NetSuite, QuickBooks Online, Coupa
After each account change, hit the “log out everywhere” or comparable button. This step kills mobile tokens and browser cookies that might linger for weeks. Some SaaS vendors hide the option under advanced settings, so keep a crib sheet with exact paths to save minutes.
Edge cases pop up faster than most teams usually expect. A shared mailbox that uses the employee’s personal email for recovery means the reset link lands in a box you no longer control. Change the recovery address first, then disable the mailbox if policy allows. For service accounts created with the worker’s credentials, swap in a neutral email alias and rotate the password once handover scripts finish.
Finish with a short smoke test: try signing in as the user through a private browser window. The denial screen is your green light to move on.
Transfer data ownership
Work grinds to a halt when an engineer walks out and their files disappear.
Make sure the handoff happens before anyone hits delete, or the team will scramble, deadlines will move, and legal holds could break. Start by listing the employee’s main work surfaces: cloud drives, code hosts, ticket systems, and customer records. Rely on the access map from earlier steps, but pay attention to where the data sits, not how the user signed in.
Google Workspace provides built-in tools that make ownership transfers fairly painless. Kick off the built-in “Transfer ownership” wizard, select the destination manager, and watch every Doc, Sheet, and Slide switch hands in minutes. Shared Drives usually stay put, yet personal My Drive folders often hide project files that nobody else bookmarked. Confirm the target account has enough storage, or the move will stall midway and leave orphaned data behind.
Code repositories need the same careful treatment as documents and tickets. In GitHub choose Settings > Transfer and point the repo to an organization owner so pull request history stays intact. Bitbucket and GitLab offer similar flows, although large repos can exceed default transfer quotas and require a support ticket. For Jira or Asana tasks, bulk-change the “assignee” and “reporter” fields and trigger notifications so nothing slips through cracks.
Run through a quick checklist so every asset lands with the right steward:
- Google Drive, OneDrive, or Dropbox personal folders
- GitHub, GitLab, or Bitbucket repositories and associated project boards
- Jira, Asana, or Trello tickets, including attachments and comments
- Salesforce opportunities, Zendesk tickets, and HubSpot deals owned by the user
- Slack channels or private messages subject to eDiscovery retention
Companies in regulated industries have zero room for guesswork when handling user data. Audit logs must show who moved each file, when it happened, and where it went for HIPAA or SOC 2 evidence. Teams often forget chat archives; export them before the user is disabled, then vault the archive per the retention policy. Deleting first and restoring later sounds tempting, yet recovery points may miss real-time edits, costing hours of rework and raising compliance flags.
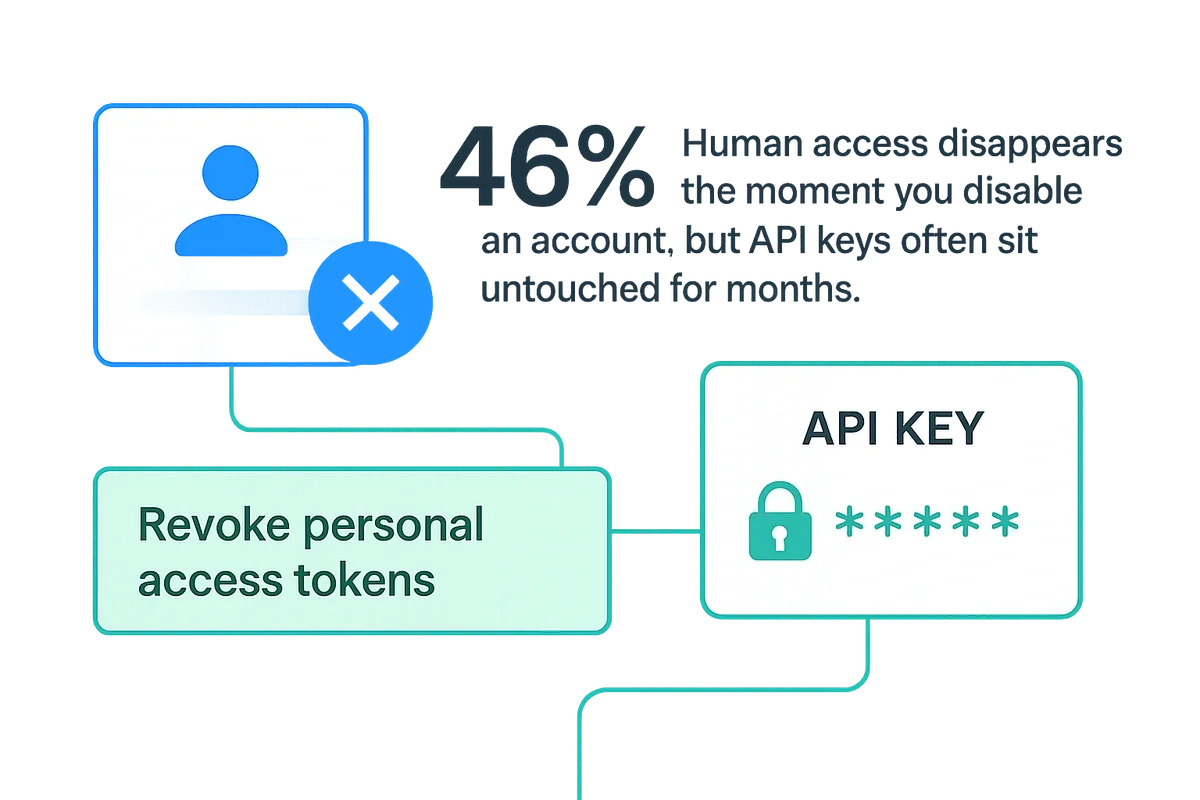
Rotate or revoke API tokens
Human access disappears the moment you disable an account, but API keys often sit untouched for months.
Verizon’s 2023 DBIR says nearly half of breaches start with stolen credentials, and many of those aren’t passwords at all. Personal access tokens in GitHub, legacy OAuth grants in Slack, and IAM keys in AWS hold permissions that almost never time out. They bypass SSO and MFA, so every switch you threw in the directory leaves them untouched and hands an ex-employee a route into production.
Start by gathering every token the directory linked to the user, then widen the net. GitHub’s REST API lists GET /user/{id}/tokens, Slack’s admin panel exports active OAuth grants, and AWS’s iam list-access-keys call returns key age in seconds so you can flag stale pairs. Scan the build servers and any CLI configs the developer touched; plain-text secrets in those spots often slip past audits.
- Revoke personal access tokens in source control, messaging, and cloud platforms.
- Invalidate refresh tokens stored in mobile apps with the vendor’s security endpoint.
- Rotate service keys the user shared, even if the account stays active.
- Send every token ID, revocation timestamp, and script result to your SIEM.
Webhooks are next because many reuse the same shared secret. Regenerate signing keys in Stripe, Segment, or HubSpot, then delete the old ones so callbacks keep flowing. If the offboarded engineer managed CI pipelines, scan environment variables for hard-coded tokens that could break tomorrow’s deploy. When rotation might hurt uptime, schedule a maintenance window and tell the DevOps channel so nobody is surprised.
Then run a dry-run build or the full integration suite. Any pipeline that fails now costs less than a 2 a.m. Incident later. After an hour, pull a fresh inventory and compare it to the original; no overlap means you’re finished.
Audit and archive offboarding actions
Offboarding isn’t finished until every click and command is written down. As soon as the identity team deactivates an Okta account, log the event with a UTC timestamp, the person or service that triggered it, the system touched, and a success code. Trying to rebuild those details later rarely works because SaaS audit logs roll over quickly and vendors live in different time zones. Bake the capture step into the revocation playbook so operators aren’t juggling an extra checkbox when nerves are already high.
When the events roll in, store them in a system built for retention, not in someone’s desktop spreadsheet. A cloud SIEM such as Splunk or Sumo Logic keeps raw JSON for years and lets auditors slice by user, app, or geography in seconds, while an immutable bucket in Amazon S3 Glacier works if budget is tight but audit windows are long. Pick a single source of truth and reference it in the security policy so nobody argues during an investigation.
Every record should follow a simple template that an intern can understand. Keep the fields predictable so a script can scan thousands of lines without pausing for edge cases.
- Event time in ISO 8601
- Application or system touched
- Human or service account initiating the change
- Action type, for example
DELETE_USER - Result code or error message
- Help-desk ticket number for traceability
When this structure is consistent, automated checks in Python or PowerShell can flag gaps before a regulator does.
Finish the process with a sanity check after the dust settles. Run a SaaS discovery scan 24 hours later and compare the fresh inventory against the exit checklist; any drift points to stale sessions, orphaned licenses, or zombie tokens that need another pass. Ship the same summary to finance and procurement so renewal forecasts match the cleaned seat counts, and to HR so they can prove the employee’s record is fully closed.

Conclusion
Guesswork has no place when you offboard someone from the SaaS stack. Begin by listing every app, license, identity, token, and data store so a single access sheet drives the work. Then drop the licenses and directory accounts, disable local logins, and hand off every file and ticket to its new owner. Wrap up by pulling any lingering tokens and logging each action for finance and auditors.
Complete each step and every departure becomes a quick checklist instead of a midnight scramble that leaves doors cracked open. A clear exit process protects data, budgets, and credibility.
Audit your company’s SaaS usage today
If you’re interested in learning more about SaaS Management, let us know. Torii’s SaaS Management Platform can help you:
- Find hidden apps: Use AI to scan your entire company for unauthorized apps. Happens in real-time and is constantly running in the background.
- Cut costs: Save money by removing unused licenses and duplicate tools.
- Implement IT automation: Automate your IT tasks to save time and reduce errors - like offboarding and onboarding automation.
- Get contract renewal alerts: Ensure you don’t miss important contract renewals.
Torii is the industry’s first all-in-one SaaS Management Platform, providing a single source of truth across Finance, IT, and Security.
Learn more by visiting Torii.
Frequently Asked Questions
The offboarding process starts with an inventory of all SaaS access tied to the departing employee, ensuring a full scope of their digital footprint.
Promptly revoking user licenses prevents unnecessary charges and stops potential exploitation of abandoned accounts by the departing employee.
IdP accounts should be suspended or deleted based on HR's confirmation, and all tied MFA methods must be reset or removed to ensure security.
Deactivating native SaaS accounts closes entry points that remain open even after IdP accounts are disabled, preventing unauthorized access.
Data ownership must be transferred using platform-specific tools to maintain continuity, ensuring no disruption to workflows or project deadlines.
API tokens should be revoked or rotated to eliminate unauthorized access, as they can often remain active even after user accounts are disabled.
The final step involves auditing and archiving all offboarding actions to create a traceable record that aids future compliance and security audits.

