Google Workspace Deactivation: What Happens to Your SaaS Licenses in 2026?
Turning off a Google Workspace user seems easy but rarely is.
That single click triggers a quiet chain of directory edits, API chatter, and cloudy guesswork across every connected SaaS service.
Finance spots a closed account while IT assumes the license count sorted itself out.
Miss one link and you’ll keep paying for seats no one touches.
Inside Workspace, suspending the account freezes the mailbox, but files, tokens, and downstream apps keep humming along.
Because each SaaS platform translates that identity through its own mix of SAML, SCIM, or raw API calls, outcomes vary wildly.
Unwatched, those orphaned seats pile up until the renewal invoice exposes the leak.
This guide unpacks what truly happens at every step, shows how that gap drains budgets and security, and gives you a repeatable, automated fix.
Table of Contents
- What happens when you deactivate in Google Workspace
- How do SaaS apps react to Workspace deactivation
- Where do orphaned licenses and costs arise after deactivation
- What workflow helps IT eliminate the deactivation gap
- How do SaaS management tools automate deactivation
- Conclusion
- Audit your company's SaaS usage today
What happens when you deactivate in Google Workspace
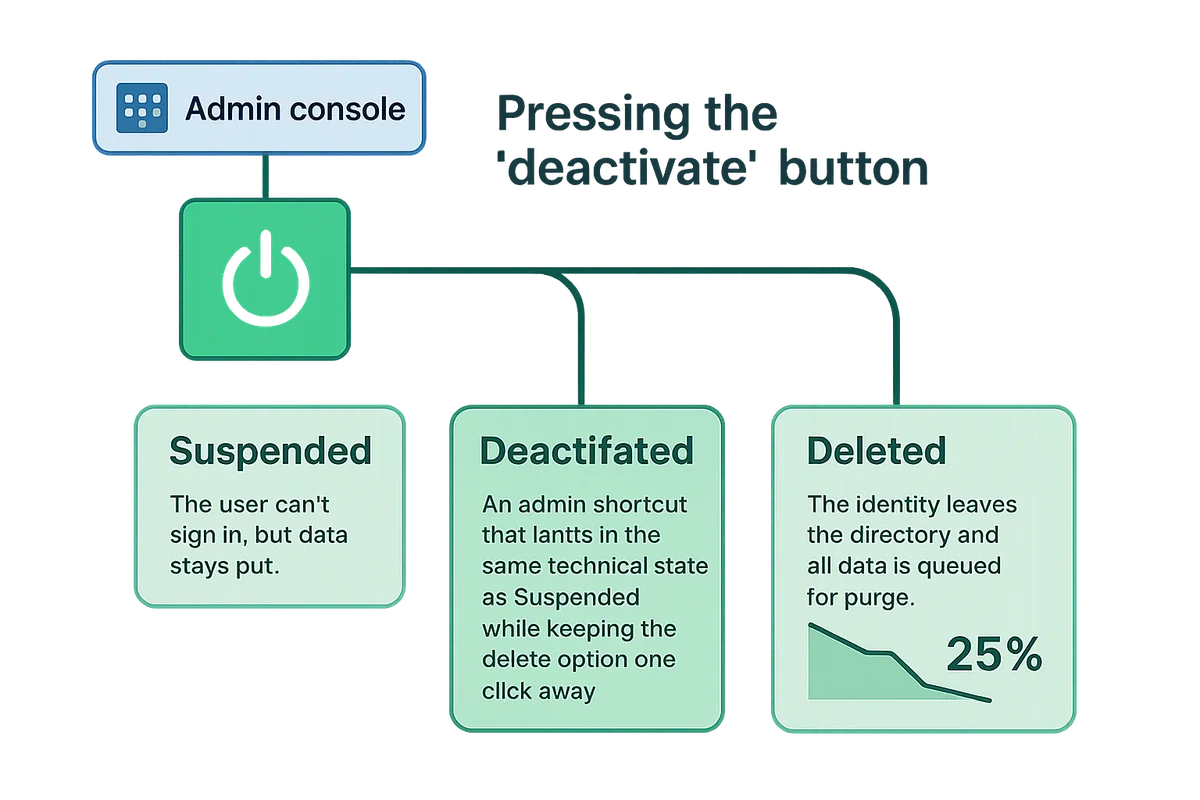
Pressing the “deactivate” button in the Admin console starts a process that appears simple but branches in several directions.
- Suspended: The user can’t sign in, but data stays put.
- Deleted: The identity leaves the directory and all data is queued for purge.
- Deactivated: An admin shortcut that lands in the same technical state as Suspended while keeping the delete option one click away.
Once deactivated, Workspace fires a tight sequence of internal jobs. The Gmail mailbox locks first, so no new mail arrives and POP/IMAP tokens stop working within minutes, while existing messages remain visible to Vault searches. Drive then earmarks every owned file for transfer to the admin’s account, but that hand-off only finishes when the admin confirms the move. Calendar shares remain intact, allowing coworkers to view past events until someone manually removes them. These delays matter because they create a gray window in which data exists without an active owner.
OAuth is next on the checklist, and this is where surprises surface. Workspace does not revoke the user’s third-party tokens immediately; instead each token stays valid until the app itself checks the user’s suspended state. If the SaaS never calls back (for example, a one-time export or weekly report), the token can linger for weeks, effectively giving the departed employee silent API access until the SaaS session naturally expires.
Even so, Google does nothing automatically about licenses in connected apps. The suspended user still counts as “active” to Slack, Salesforce, or any other app that was merely authenticated with Google Sign-In. Workspace lacks a reclaim loop, audit flag, or budget alert for those external seats. Admins who assume deactivation will cut related costs often discover later that finance is still paying for a ghost roster.
How do SaaS apps react to Workspace deactivation
Google cuts off communication first, but the linked SaaS tools run on their own timers. A Workspace suspension flips a bit in the directory, yet the SAML single sign-on certificate and any stored OAuth tokens can linger until the SaaS hears otherwise. Because every vendor connects to Google differently, one identity event can send several conflicting signals.
Federation hinges on two signals that move at different speeds. SAML tells the app “let this person in right now,” while SCIM or the Directory API handles the slower profile and license updates. Many vendors follow a “last assert wins” approach, so the most recent SAML login can override whatever SCIM reported earlier. If the user never logs in again, the SaaS relies only on the sync job you scheduled, whether that runs at midnight, hourly, or almost never.
When those signals drift out of sync, you’ll usually see one of three license outcomes on the backend.
- Automatic revoke, where SCIM removes the seat and downgrades the user profile.
- Entitlement freeze, where the seat stays tied to the person but blocks access until reactivation.
- Silent orphan, where nothing changes and the license keeps billing as though the employee still works there.
Real platforms show how different these outcomes feel day to day. Slack queries SCIM within minutes and flips the user to “Suspended,” instantly freeing the paid seat. Salesforce holds the license until an admin manually unassigns it, even if SCIM flags the account inactive. Zoom listens only to SAML, so a deactivated Workspace user can keep hosting meetings for weeks unless you enable Zoom’s separate SCIM connector.
Timing adds a final curveball that trips many offboarding checklists. Each SaaS decides when to poll Google, and bulk jobs often run during low-traffic hours. A Friday afternoon termination may not reach every app until Monday, giving the former employee a long goodbye and leaving Finance to pay for a seat that should already be back in the pool.
Where do orphaned licenses and costs arise after deactivation
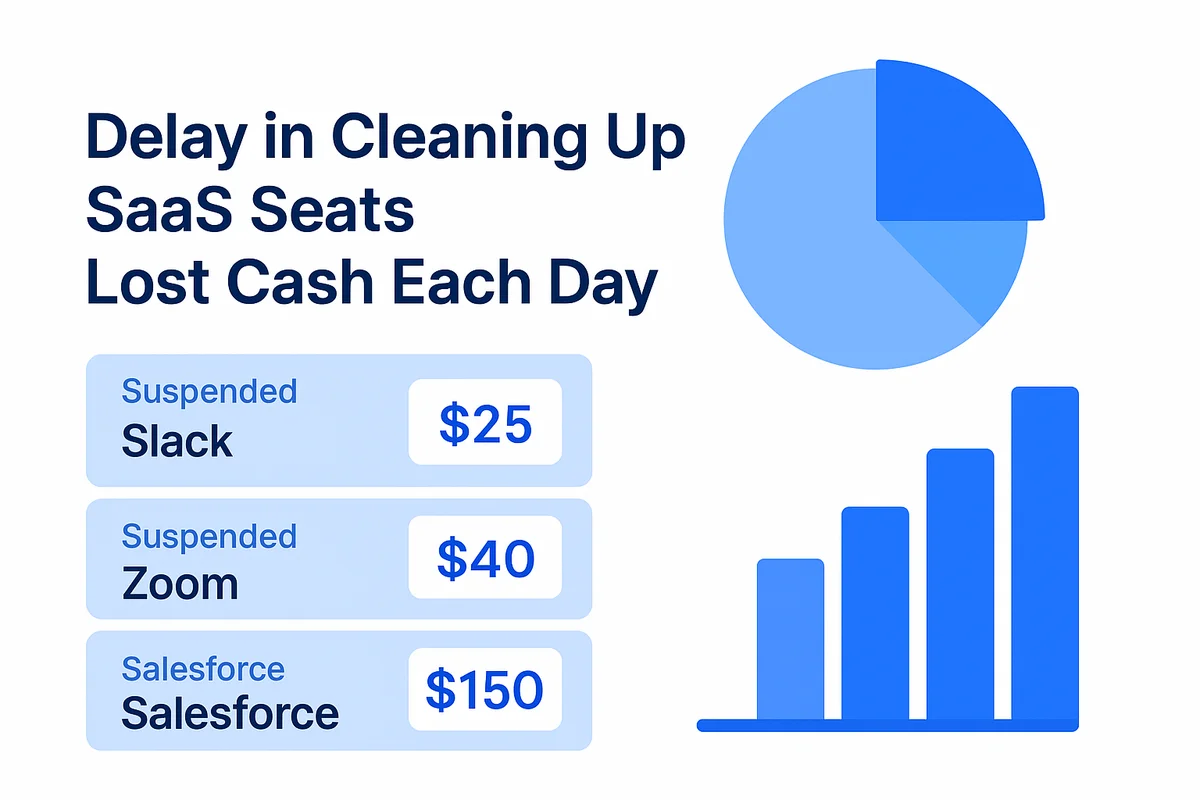
The delay between suspending a Workspace user and cleaning up SaaS seats drains cash each day. A finance team sees an employee leave, yet the spreadsheet tracking seats still shows “active,” so the vendor invoice keeps rolling. A $25 Slack seat, a $40 Zoom plan, and a $150 Salesforce license pile up; multiply those figures across hundreds of employees with normal turnover and the loss hits six figures before anyone asks why.
Unused licenses, though, represent only a slice of the hidden tab. When Google freezes an account, OAuth tokens that user granted to tools like Asana or GitHub often keep refreshing because those apps trust the last valid token, not the Directory. Former staff can still hit APIs or shared links from a personal device. Security teams then scramble to revoke tokens one by one after an alert or, worse, a breach investigation.
A patchwork of admin consoles makes the waste hard to spot. Workspace says the user is “suspended,” Zoom still shows “paid,” and Notion has the profile tagged “guest” yet billable. Pulling a clean audit trail across all three takes hours, so many companies never bother and simply pay the extra. During a SOC 2 review, that limited visibility counts as a control gap because auditors expect proof that access and spend close within 24 hours of off-boarding.
- Slack: $25 x 30 orphaned seats x 12 months = $9,000
- Salesforce: $150 x 15 seats x 12 months = $27,000
- Zoom: $40 x 40 seats x 12 months = $19,200
- Shadow IT tokens: breach investigation average = $14,000 per incident
Even a mid-size firm can leak $70,000 or more a year, and that figure ignores the opportunity cost of unclaimed volume discounts or the legal bill if stale credentials fuel data exposure. Small gaps in identity hygiene, left unchecked, turn into budget line items nobody ever approved.
What workflow helps IT eliminate the deactivation gap
Cleaning up user access moves faster when off-boarding starts the moment HR finishes the exit chat. Give it an extra hour, and tokens keep working, files drift, and managers reshuffle seats without a paper trail.
Start with a daily HR export or webhook that plants the departing employee’s ID in the ticket queue before the farewell email lands. One trigger then pauses the Google account, fires off SCIM calls, and spins up a checklist for the leftover manual tasks.
A tight, well-ordered checklist keeps every handoff clear for the whole team:
- Suspend the Google user, then route mail to a shared inbox so customers never reach a dead end.
- Send SCIM deactivation to high-risk apps (GitHub, Okta, Slack) within 60 seconds to shut the door before SAML accepts another token.
- Transfer Drive, Calendar, and Shared Drive ownership, then flag unusual external shares for review during the 30-day hold.
- Park SaaS seats in a quarantine group that finance can count but nobody can use, keeping entitlement math honest.
- Schedule a day-30 audit, capture mean time to reclaim, and file the proof in your SOC 2 folder before the auditor asks.
When roles aren’t clear, policy turns into guesswork across time zones. Give IT the technical steps, finance the seat-value check, and compliance the breadcrumbs; with columns assigned, the runbook survives vacations and reorganizations. Set an SLA like “license closed within four business hours” and post the monthly scores so people see the trend.
Tag each license in Google Workspace or the SaaS catalog before you hit suspend. Sorting seats by cost center and criticality lets scripts recycle the pricey ones first, prevents surprise renewals, and hands procurement solid data for vendor talks six months down the road.

How do SaaS management tools automate deactivation
Manual off-boarding scripts fall apart the moment a new SaaS app sneaks into the stack. Their rigid triggers catch Google Workspace status changes yet skip dozens of side apps that never phone home after a user is suspended. A SaaS management platform closes that gap by tracking identity events in every connected tool at API speed instead of waiting for a nightly cron job.
Good platforms funnel each deactivation event into a rules engine that acts immediately, notifies the right people, and records every step for later audits. Core features usually fall into four buckets:
- Real-time listeners that capture Workspace suspends, last SAML assertions, and token refresh attempts
- Cross-app license catalogs that show who owns each seat and its monthly cost
- Policy builders that revoke, downgrade, or transfer seats through SCIM or direct API calls
- No-code approval flows that send Finance or HR a Slack prompt before the reclaim switch flips
Because all actions remain tied to the original identity, the system keeps OAuth tokens, admin logs, and asset transfers in one timeline. That central view means a SOC 2 auditor can trace “user left company” to “license recycled” without hopping between ten consoles. It also cuts the “where did that seat go?” questions that surface during quarterly true-ups.
Concrete numbers usually persuade finance teams faster than any well-designed slide deck. BetterCloud customers report 80 percent faster off-boarding when policies trigger on the first Directory API change rather than an IT ticket. Savings feel small per seat, but when Zoom, Asana, and Salesforce all bill on the same day, reclaimed licenses quickly cover the platform fee.
Even with similar feature lists, the right platform choice still makes or breaks a rollout. Check coverage breadth first; a library of 300 connectors sounds great until the one tool Finance loves is missing. Confirm role-based access controls so HR can trigger off-boarding without seeing payroll data, and insist on immutable audit trails stored for at least seven years. Finally, preview the reporting layer, and if reclaimed seats and dollar impact aren’t obvious in two clicks, the platform will gather dust.
Conclusion
Deactivating a Google Workspace account barely scratches the surface of license cleanup. Suspending the user shuts off Gmail and transfers Drive files, but those connected third-party tools keep running and charging. That hidden drag hits both your budget and your security stack.
Pair a clear offboarding checklist with a SaaS management platform that tracks every token and seat, and you can reclaim licenses quickly while keeping auditors happy. Treat deactivation as a workflow, not a button; the savings follow fast.
Audit your company’s SaaS usage today
If you’re interested in learning more about SaaS Management, let us know. Torii’s SaaS Management Platform can help you:
- Find hidden apps: Use AI to scan your entire company for unauthorized apps. Happens in real-time and is constantly running in the background.
- Cut costs: Save money by removing unused licenses and duplicate tools.
- Implement IT automation: Automate your IT tasks to save time and reduce errors - like offboarding and onboarding automation.
- Get contract renewal alerts: Ensure you don’t miss important contract renewals.
Torii is the industry’s first all-in-one SaaS Management Platform, providing a single source of truth across Finance, IT, and Security.
Learn more by visiting Torii.
Frequently Asked Questions
Deactivating a user freezes their mailbox, but files and associated tokens remain active, potentially allowing unauthorized access until all connected SaaS applications update.
SaaS apps react differently; some revoke access immediately, while others may keep the account active until the next scheduled sync or manual intervention.
Orphaned licenses are accounts that remain active after a user leaves, leading to ongoing charges for unused seats and budget drains for organizations.
IT should implement a structured offboarding process that initiates account suspension and license reclamation immediately after receiving notice of an employee's departure.
SaaS management tools automate the deactivation process by tracking identity events and managing license changes efficiently, reducing the risk of orphaned licenses.
Regular audits help identify unused licenses, track application costs, and ensure compliance, ultimately optimizing budget management and reducing security risks.
Organizations should create a detailed checklist for offboarding processes, ensuring clear roles and responsibilities are established to facilitate efficient license management.

