How to Create a SaaS Offboarding Process That Actually Works in 2026
Offboarding employees from SaaS accounts is rarely glamorous, yet it’s where many breaches start.
Teams understand the stakes, yet hand-built spreadsheets and frantic Slack pings still rule the last-day scramble. When you link role-based policies, live app inventories, and deprovisioning that follow HRIS status changes, you cut both data loss and wasted spend while sparing IT from midnight clicking marathons. A clean audit trail plus cost reconciliation transforms offboarding from a fire drill into a repeatable control that satisfies security teams and finance leaders alike.
This guide shows you how to build that secure, automated SaaS offboarding workflow step by step, starting today.
Table of Contents
- Craft a clear, role-based exit playbook
- Map every app the leaver touches
- Trigger smart, automated deprovisioning on status change
- Secure data and lock down the trail
- Close the loop and measure improvements
- Conclusion
- Audit your company's SaaS usage today
Craft a clear, role-based exit playbook
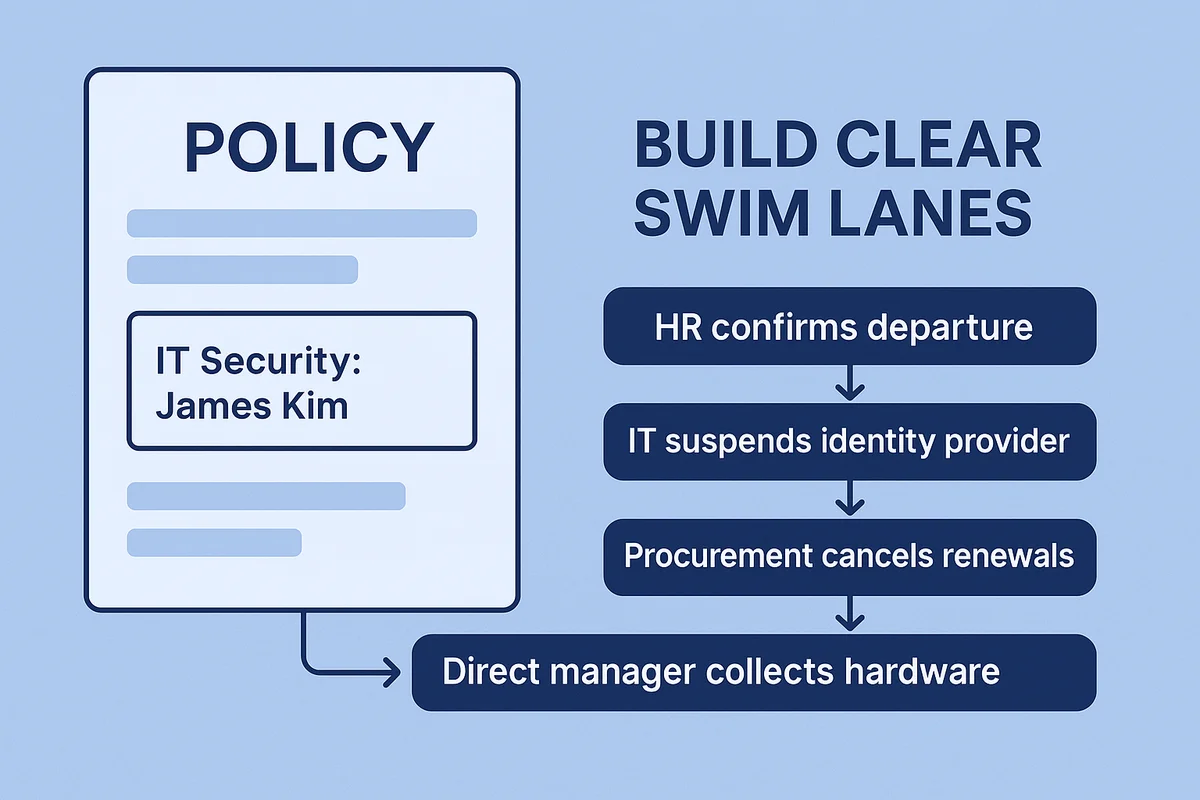
Offboarding chaos starts when no one knows who owns each task. The fix begins with a role-based policy that lists people, not departments, so a badge or license never lingers longer than it should. Write the owners directly into the policy, such as “IT Security: James Kim,” and update the roster every quarter.
Build the policy around clear swim lanes, then connect each exit step to its corresponding lane.
- HR confirms the departure in Workday and records last paid day.
- IT suspends the identity provider and clears privileged vaults.
- Procurement cancels vendor renewals and updates blanket POs.
- The direct manager collects hardware and signs off on data transfers.
The moment HR marks the worker “inactive,” automation kicks in. A webhook from the HRIS pings the offboarding workflow, starting a 15-minute countdown for mission-critical systems such as the identity provider, code repositories, and customer data stores. Less sensitive apps, like survey tools, can wait up to 24 hours, but the timer is still tracked. If the manager needs the user’s mailbox kept alive for client handoffs, they tick a “forward email” box in the form, which reroutes the sequence instead of forcing a late-night help-desk ticket.
Departure scenarios vary, so each one needs its own guardrails. Voluntary exits follow a friendly checklist that covers revoking access and archiving email. Terminations tighten the screws: immediate suspension, executive approval for any data export, and a legal hold if the user is under investigation. Flags for legal hold freeze deletion steps until counsel signs off, while HR and Security get read-only visibility into progress.
All of this only works if everyone references the same source of truth. Store the policy and its JSON checklist template in a private GitHub repo that demands pull requests for every change. That way, when IT adds a new SaaS tool or procurement updates dollar thresholds, the revision flows straight into each stakeholder’s personal task list without another status meeting.
Map every app the leaver touches
To see every app a departing employee has touched, start with data streams the company already collects yet seldom combines. Feed sign-ins from Okta into the same lake that stores your CASB shadow-IT discoveries, then layer in corporate card transactions, contract records, and admin exports from tools like Atlassian or HubSpot. Once timestamps are normalized and user IDs match, the full footprint appears in minutes instead of after a four-hour spreadsheet hunt.
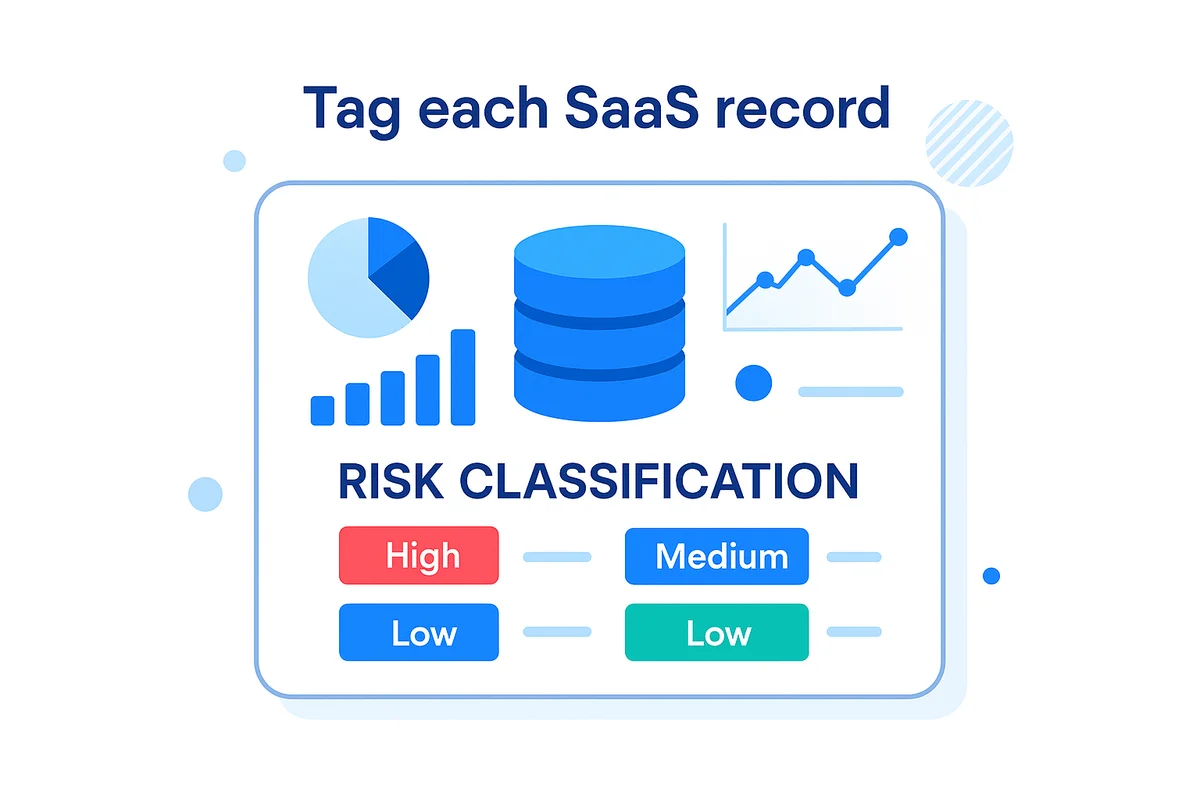
Not every SaaS record carries the same risk, so tag each one as you ingest it. A simple three-tier model keeps the follow-up work manageable:
- High: customer data, source code, financial or health info
- Medium: internal project docs and analytics dashboards
- Low: marketing calendars or training portals
As the inventory populates your dashboard, filters reveal which high-risk apps still have active sessions, while low-risk entries can wait a day before you cut them off.
Rogue signups often hide outside SSO, but corporate cards expose them on every statement. Query expense feeds for line items like “Stripe ‑ Seat” or “Figma*” that match the user’s email domain, then cross-reference vendor billing portals for any account keys not yet claimed in IT’s admin center. Platforms such as Productiv provide APIs to automate that lookup and surface shadow licenses you would have missed by checking SSO alone.
Before scheduling the deprovision job, pull the manager into a 15-minute access review. Walk through the high and medium tier apps, confirm shared logins that might lock out a team, and flag any personal email forwards or API tokens the script could miss. The manager signs off in your ticketing system, and the inventory snapshot locks in as the definitive record for the coming workflow, giving audit and finance one source everyone can reference.
Trigger smart, automated deprovisioning on status change
Access needs to vanish the moment HR flags an employee inactive in the HRIS.
That single field should toss a webhook straight to your identity provider, not wait around for a midnight batch job, because each extra minute leaves room for mischief.
Most shops connect Rippling or Workday to Okta with a tiny JSON payload that says, in effect, “suspend user now.”
- The IdP pauses SAML and OAuth sessions right away, stopping single-sign-on tokens before they can refresh.
- A lambda or workflow engine walks your SaaS catalog, hitting SCIM or vendor APIs in order of importance: CRM and code repos first, lightweight survey apps last.
- Next come MFA resets, clearing push tokens from Duo and Google Authenticator so previously enrolled devices don’t slide through.
- As each vendor confirms, the script frees the license and records the response ID for evidence.
Managers occasionally need a brief window to pull project files or hand off customer threads.
Bake that exception into the same automation so IT isn’t chasing one-off requests.
A Boolean flag on the ticket can delay the IdP suspension but still block writes, or keep the mailbox open while routing new mail to a shared queue watched by the team lead.
Thorough verification matters just as much as sending the revoke call itself.
Fire a follow-up job two hours later that compares expected license counts with the vendor report; any mismatch pings Slack for manual review.
Because some tools, including Atlassian Cloud, hide license events, a nightly API pull reconciles seats and drops the CSV into your SIEM.
For high-risk systems, add a callback requirement: the workflow closes only when the vendor returns a 200-level code and the user status reads “deactivated.”
Any other response is tagged “pending” and escalated automatically, tightening the process without dumping more work on admins.

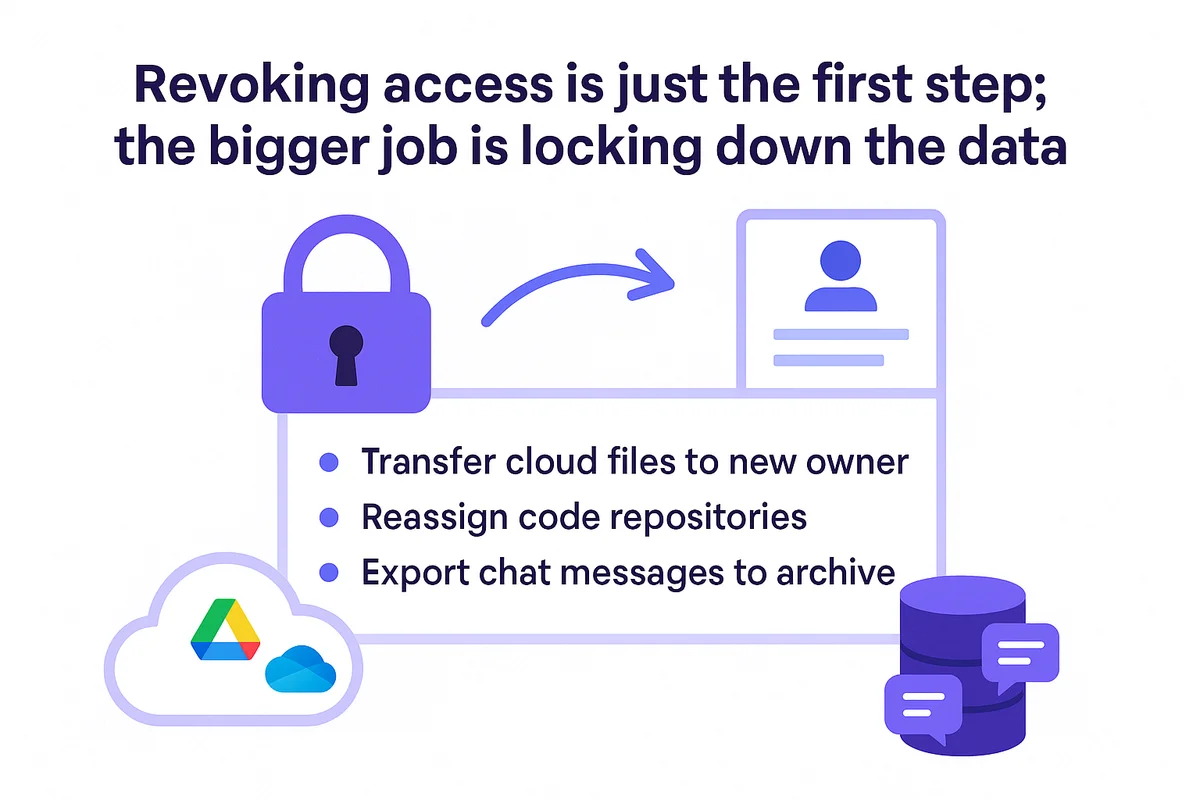
Secure data and lock down the trail
Revoking access is just the first step; the bigger job is locking down the data. After an IdP token is killed, shift to moving assets so nothing stays in limbo. Start with cloud storage: use Google Workspace Admin SDK to hand Drive files to the manager or run the Microsoft 365 Invoke-PST script for OneDrive. Code needs a home too, so flip GitHub repo ownership and reassign open pull requests. Chat histories often include contract details, so export Slack or Teams messages to a dedicated S3 bucket before retention clocks expire.
- Transfer Google Drive or OneDrive files to the new owner
- Reassign GitHub or GitLab repositories and CI tokens
- Export Slack or Microsoft Teams data to a cold archive
- Forward email to a shared mailbox, then archive the PST
Every click above must hit a tamper-proof audit trail that satisfies SOC 2 CC7.4. Pipe each system’s webhook into a central log collector, whether that’s Splunk or a lightweight fluentd box, and store the JSON alongside user IDs, IPs, and precise timestamps. Append before-and-after permission snapshots so an external auditor can see the access delta without digging through tickets. If an API call fails, log the error code and queue a retry to keep ghost accounts from sneaking past weekly reconciliations.
Retention and discovery policies determine where those archives live and how long. Encrypt exports at rest with KMS keys, tag them by data class, and set lifecycle rules: seven years for finance, two for marketing, legal hold overrides for anything under litigation. Tools like Vaultree let you search ciphertext directly, keeping e-discovery fast without decrypting gigabytes of files. A periodic hash check confirms no silent corruption crept in during storage-tier moves.
Keep a close eye on the exit window for departing staff. SIEM rules should flag large file downloads, unusual Git clone bursts, or sudden mailbox forwarding changes inside the last 30 days of employment. Escalate anomalies to security within an hour, because catching exfiltration after the laptop is turned in is too late.
Close the loop and measure improvements
Offboarding ends only when every downstream system confirms the employee is fully closed out. A clean hand-off begins in procurement: cancel open purchase orders in Coupa or your ERP, mark any recurring SaaS subscriptions “inactive,” and set reminders for renewal dates so dormant seats don’t creep back onto invoices. Finance compares the reclaimed license list with the month’s vendor bills and flags gaps; teams often discover they paid 5 to 8 percent more than necessary after the numbers align.
Payroll and benefits operations must move with the same urgency. Once HR records the last working day in Workday, an integration script should trigger final pay, severance, COBRA notices, and pension updates in minutes, not days. Syncing these steps with the IT checklist prevents a former teammate from logging vacation hours after access is gone, a mistake auditors still catch.
Store every deprovisioning detail inside the employee’s HRIS profile so auditors see one story. Immediately push the structured JSON log to your GRC or SIEM, whether that’s Splunk or another tool, so security analytics can correlate former-employee events with any spikes in data access. When tickets, API calls, and manager approvals share the same unique offboarding ID, cross-platform searches take seconds.
When you measure results, offboarding shifts from compliance chore to cost lever. Track median time to deprovision, percentage of licenses reclaimed within 24 hours, dollars saved per quarter, and the count of exceptions granted. Publishing these metrics in a simple dashboard keeps leadership interested and highlights scripts that need work.
After each cycle, hold a brief retrospective to note what broke or improved:
- Which checklist steps caused the most delay, and why
- Systems that lacked API coverage, forcing manual workarounds
- Invoice mismatches uncovered during license reconciliation
- Security alerts triggered post-separation and their resolutions
- Action items, owner, and target fix date for each finding
Stakeholders can scan this document in under ten minutes, yet it still drives the tweaks that keep your offboarding machine sharp.
Conclusion
Offboarding works only when everyone involved knows what to do. We defined clear roles for HR, IT, procurement, and managers, maintained a live checklist, kept current app inventories, and set up triggers that shut down accounts within minutes while routing data to the right owners. Audit trails, anomaly alerts, and cost metrics pull the entire flow back to compliance and budget sanity.
With roles, inventories, automation, and follow-through in place, SaaS offboarding stays quick, safe, and easy to audit.
Audit your company’s SaaS usage today
If you’re interested in learning more about SaaS Management, let us know. Torii’s SaaS Management Platform can help you:
- Find hidden apps: Use AI to scan your entire company for unauthorized apps. Happens in real-time and is constantly running in the background.
- Cut costs: Save money by removing unused licenses and duplicate tools.
- Implement IT automation: Automate your IT tasks to save time and reduce errors - like offboarding and onboarding automation.
- Get contract renewal alerts: Ensure you don’t miss important contract renewals.
Torii is the industry’s first all-in-one SaaS Management Platform, providing a single source of truth across Finance, IT, and Security.
Learn more by visiting Torii.
Frequently Asked Questions
Effective offboarding is essential to prevent data breaches and control costs, ensuring that access is revoked promptly and securely.
A role-based exit playbook clearly defines who is responsible for each task during offboarding, preventing chaos and ensuring timely completion.
Automate deprovisioning by integrating your HRIS with identity providers to trigger immediate access revocation upon employee status changes.
Secure data by transferring ownership of files, exporting communications, and maintaining an audit trail to ensure data protection.
Utilize existing data streams such as sign-ins and corporate card transactions to track all applications an employee accessed.
Best practices include maintaining clear logs of all actions, comparing vendor reports, and monitoring for anomalies during the offboarding process.
Companies can enhance offboarding by defining roles, automating processes, and regularly reviewing and adjusting their workflows for efficiency.

