The Difference Between a SaaS Management Platform and CASB
Business teams keep piling on SaaS tools. Licenses sprawl, attack surfaces widen, audit questions pile up. The CFO spots wasted seats, and the CISO finds shadow IT. Both want answers that don’t slow growth.
Two product families can help. A SaaS Management Platform keeps a live inventory, ties usage to cost, and can tweak licenses through direct application APIs. A Cloud Access Security Broker reviews network logs and SaaS API events, enforces data-loss policies, and blocks risky sessions. Both discover apps, but each pursues a different outcome.
We’ll cover where an SMP saves money, where a CASB trims risk, and how using both aligns IT, finance, and security objectives at every growth stage.
Table of Contents
- What an SMP Does for Efficiency
- How a CASB Locks Down Cloud Apps
- SMP vs CASB: Five Big Differences
- Real-World Scenarios Using One or Both
- Conclusion
- Audit your company's SaaS usage today
What an SMP Does for Efficiency
A SaaS Management Platform keeps a company’s cloud software stack under control. It plugs into every sanctioned workspace, finance tool, and single sign-on feed, then watches for new logins or purchases that pop up. Each new signal lands in a single, real-time inventory so IT, finance, and procurement look at the same list.
Most teams lean on an SMP for five repeatable jobs:
- Continuous discovery that flags any app, paid or free, the moment a user signs up
- License right-sizing that finds idle seats and schedules downgrades ahead of renewal
- Click-through workflows for onboarding or offboarding that sync accounts across HRIS, the identity provider, and the app itself
- Renewal dashboards that tie usage to cost centers and forecast spend a quarter in advance
- Procurement add-ons such as PO creation, approval routing, and contract reminders
API access drives the whole loop. An admin key from Microsoft 365 or Workday hands the platform raw counts: active seats, storage consumed, last login time. The engine compares that data with payroll rosters, pinpoints who left the company, and sends a de-provision request back into the app. Per-seat spending drops without manual spreadsheets.
The main metric is efficiency. Success looks like lower per-user software costs, quicker employee ramp-up, and no surprise renewals. Risk scoring, malware checks, and data loss prevention sit outside the brief; another tool handles those. The SMP instead hands the CFO a cleaner budget and gives IT back the hours once lost in siloed admin panels.
How a CASB Locks Down Cloud Apps
A Cloud Access Security Broker stands between users and cloud apps and enforces security policy. It monitors every login, file share, and chat message moving to SaaS tools, then instantly decides whether the action is safe.
Core jobs include
- Spot unsanctioned apps by reading firewall and secure web gateway logs
- Classify sensitive data with pattern matching and optical character recognition
- Block or quarantine files that break data loss rules
- Detect risky behavior like impossible-travel logins or mass downloads
- Prove compliance by logging every action for audits
Most platforms run in two modes. Inline mode creates a reverse proxy endpoint, so traffic flows through the CASB before it reaches the SaaS host. This lets the broker remove a Social Security number from an upload or switch Google Drive to view-only. API mode connects to the SaaS provider afterward. It scans stored data, then retroactively encrypts old files or deletes public links. Many organizations use both: inline shields live sessions, while the API cleans up anything that slips through.
The broker listens to the identity provider as well. When Okta flags a risky login, the CASB can demand step-up multifactor authentication or end the session. A link to the incident-response platform completes the workflow, so a suspicious Dropbox share opens a ticket and locks the account until an analyst signs off.
Gartner reports that nearly half of cloud traffic is now “shadow IT.” With that share rising each quarter, having a gatekeeper is no longer optional. Netskope found that companies running a CASB cut accidental data exposure by 80 percent within six months. The improvement comes because the tool turns a plain policy, “no customer data outside the CRM”, into technical controls users can’t bypass. Tight guardrails, fewer pop-ups, and clear logs keep security and legal teams confident while everyone else keeps moving fast.
SMP vs CASB: Five Big Differences
SaaS Management Platforms track spend and usage, while CASBs monitor risk and policy. Both pull data from cloud footprints but go no further.
Discovery depth separates them. An SMP hits the admin API in Slack, Salesforce, and similar apps to count every paid seat the moment seems. A CASB reviews traffic from a web gateway or firewall, then jumps into app APIs to flag uploads the network overlooked. The SMP produces a roster of paid, idle, or freemium accounts tied back to cost centers. The CASB produces a timeline of who handled regulated data, when, and on which device.
Look at what each platform records and the intent is obvious. License counts, renewal dates, purchase orders, and business owner tags sit in the SMP console. File hashes, user risk scores, DLP rule hits, and compliance labels sit in the CASB.
Automated actions differ too.
- SMP: reclaim idle seats, push right-size purchase requests to Coupa, open Jira tickets for off-boarding.
- CASB: encrypt a file in Box, force MFA mid-session, quarantine a risky account until the SOC clears it.
Stakeholders go where their metrics live. Finance, procurement, and IT asset managers open the SMP to follow the money. Security engineers and compliance teams stay in the CASB to follow the alerts.
Integration style widens the gap. SMP vendors such as Torii and Zylo prefer direct OAuth links into hundreds of apps. CASBs such as Netskope or Microsoft Defender for Cloud Apps sit inline as a forward proxy and request API scopes only when deep file inspection is required.
That split shows up in budget talks. SMP projects usually come out of the CIO’s operations line and aim for savings in the first quarter; ASICS, for example, cut SaaS spend by 15 percent after enabling Zylo. CASB projects sit with the CISO, who measures incident counts.
When a team knows which outcome matters, money saved or risk reduced, the choice is straightforward.

Real-World Scenarios Using One or Both
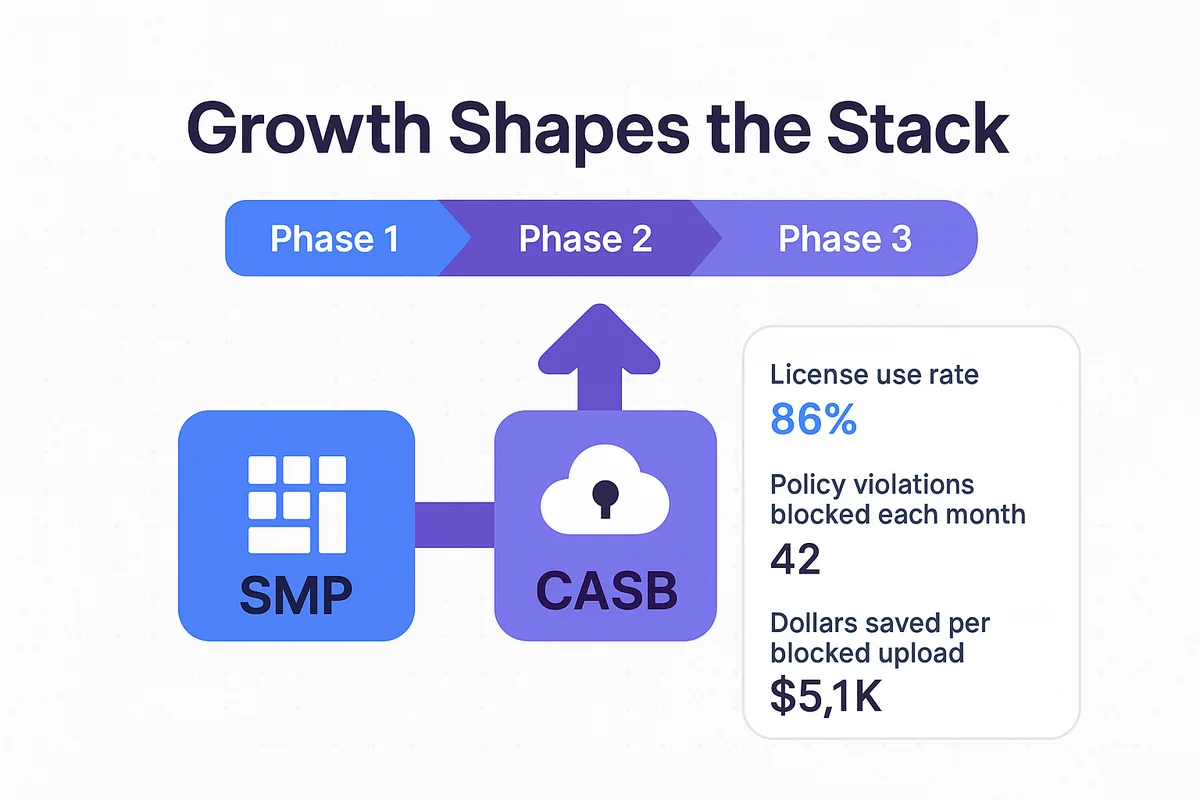
Growth shapes the stack. Finance needs hard numbers. Security wants fewer blind spots. The typical rollout unfolds in three stages.
- Phase 1: Stand up a SaaS management platform (SMP) to inventory every license and flag under-used seats.
- Phase 2: Layer on a cloud access security broker (CASB) to enforce data policies and attach risk scores to each app.
- Phase 3: Combine insights from both tools to combine contracts and eliminate redundant spend.
The order can change, but the hand-off stays the same. Feed the CASB the SMP license list to mute alerts on unused accounts. Push any high-risk event back to the SMP so it pulls that seat in minutes, not weeks.
A shared scorecard covers both views:
- License use rate
- Policy violations blocked each month
- Renewals closed on time
- Dollars saved per blocked upload
As those metrics improve, the CIO sees spend drop, the CISO sees risk drop, and the company moves past single-tool coverage into real SaaS maturity.
Conclusion
SMP tracks apps and spending. CASB protects data and sessions. The article broke down what each tool sees, how it responds, and who needs the outcome. We touched on SMP jobs such as cleaning up licenses, tightening the purchase flow, and mapping costs back to teams. Next came the CASB side: monitoring traffic, enforcing DLP, and blocking risky activity. A side-by-side chart compared what each tool discovers, the steps it can take, and who typically owns it inside the company.
Choose the tool that meets today’s objective, then add the next layer when the time comes.

Audit your company’s SaaS usage today
If you’re interested in learning more about SaaS Management, let us know. Torii’s SaaS Management Platform can help you:
- Find hidden apps: Use AI to scan your entire company for unauthorized apps. Happens in real-time and is constantly running in the background.
- Cut costs: Save money by removing unused licenses and duplicate tools.
- Implement IT automation: Automate your IT tasks to save time and reduce errors - like offboarding and onboarding automation.
- Get contract renewal alerts: Ensure you don’t miss important contract renewals.
Torii is the industry’s first all-in-one SaaS Management Platform, providing a single source of truth across Finance, IT, and Security.
Learn more by visiting Torii.
Frequently Asked Questions
A SaaS Management Platform (SMP) helps organizations manage their cloud software inventory, optimize software licenses, and track usage against costs, ensuring efficiency and budgetary control.
A Cloud Access Security Broker (CASB) monitors user activities in cloud apps, enforcing security policies and preventing data loss by blocking risky actions while ensuring compliance through auditing.
Key features of an SMP include continuous app discovery, license right-sizing, automated onboarding/offboarding, renewal dashboards, and procurement integration to streamline software management.
A CASB prevents data breaches by identifying unauthorized apps, classifying sensitive data, blocking dangerous activities, and logging actions for audits, ensuring organizational compliance.
SMPs focus on tracking software spending and usage, while CASBs prioritize security by monitoring risks and enforcing policies within cloud applications.
Initial steps include deploying an SMP to understand software usage, followed by implementing a CASB to secure cloud applications and enforce data policies, aligning IT and finance.
Using both an SMP and CASB allows businesses to track costs while enhancing security, thus enabling better resource allocation and minimizing risks as the organization grows.

