5 Ways to Detect Shadow AI Apps in Your Organization in 2026

Generative AI slipped into offices the same way SaaS once did, quietly and on personal credit cards. It leaves security teams to discover new language models, chatbots, and code assistants only after sensitive files have already walked out the door. Shadow AI is real, and finance, IT, and compliance all feel the pinch.
Clues sit in plain sight across accounting systems, SSO consoles, and web browsers. When analysts connect a curious line item on an expense report with a fresh OAuth token and a spike in calls to api.openai.com, they can move before regulators or customers spot the leak. Patterns surface quickly once finance and SOC data share the same workbook.
Following the money, the tokens, the extensions, the packets, and the people lets security leaders spot shadow AI early and keep data safe.
Table of Contents
- Follow the money
- Check OAuth consent logs
- Audit browser extensions
- Monitor outbound AI traffic
- Interview users
- Conclusion
- Audit your company's SaaS usage today
Follow the money
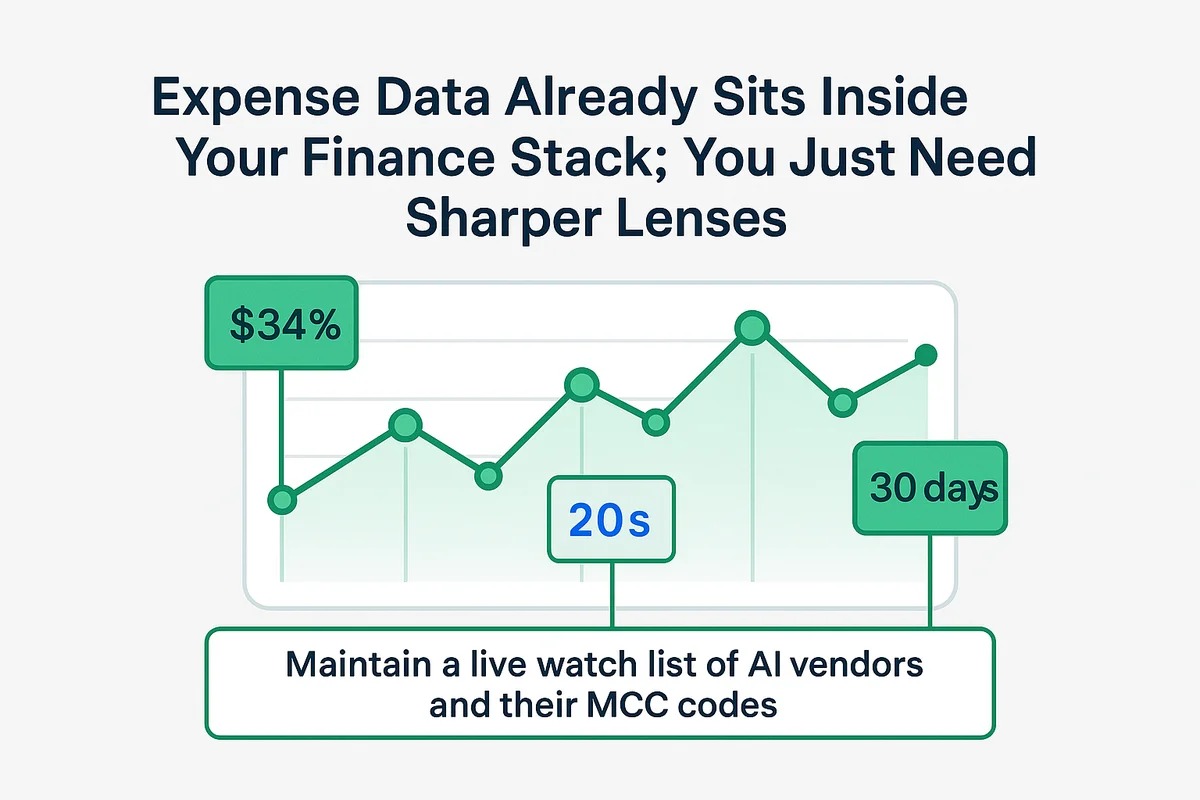
Expense data already sits inside your finance stack; you just need sharper lenses. Generative AI subscriptions rarely cost more than a team lunch, so they slide under spend thresholds built for six-figure SaaS renewals. That small price tag turns finance into the earliest detection system once you teach it what to notice.
Start by exporting the last quarter of card and reimbursement activity to a spreadsheet. Sort by merchant category code, then scan descriptions for “GPT,” “Copilot,” “Claude,” “Midjourney,” or plain words like “AI helper.” PwC reports that 34 percent of employees expense unapproved software at least once a year, which means the signal exists, you only have to isolate it. Pattern recognition matters more than single hits; clusters of twenty- to thirty-dollar charges every 30 days often reveal seats on OpenAI or comparable platforms operating quietly.
- Maintain a live watch list of AI vendors and their MCC codes.
- Alert on recurring micro-transactions between 15 and 50 USD.
- Tag expense notes containing “prompt,” “AI,” or “copilot” for review.
- Auto-route flagged items to security before reimbursement is approved.
Finance already automates VAT validation and duplicate detection, so sending suspect AI spend to security taps the same plumbing. Create a rule in Concur or Coupa that fires when the merchant name matches your watch list or the claim notes mention a chatbot. The workflow then emails the requester, the manager, and a security analyst with three quick questions about data type, volume, and vendor terms. Payment stays on hold until answers land, which usually takes an hour, not weeks.
Keeping the loop tight turns every team member into a partner instead of a hall monitor. Employees still get the productivity boost of a language model, while legal and procurement gain enough time to negotiate data-protection clauses before corporate information leaves the building. When finance, security, and department heads share the same dashboard, the conversation shifts from blame to risk-weighted approval. That shared visibility marks the first step toward turning shadow AI into sanctioned AI.
Check OAuth consent logs
OAuth consent logs read like a ledger of every outside service your staff ever invited into the company vault.
Most identity providers let you export a CSV full of app names, user counts, and the precise scopes tied to each token.
As you scan, flag any entry that wants broad access to email or files even though it only claims to offer writing help.
Microsoft’s security team found that 35 percent of risky apps requested Mail.ReadWrite even though their marketing material never mentions email.
Naming tricks complicate things, so match permissions first and branding second.
An extension named “FocusTool” might quietly send prompts to a large language model cluster.
Any token holding Files.ReadWrite.All deserves top priority because it lets the service edit every SharePoint or Drive file the user can reach.
When five marketers approve the same app on the same day, chances are a manager just launched a shadow AI pilot.
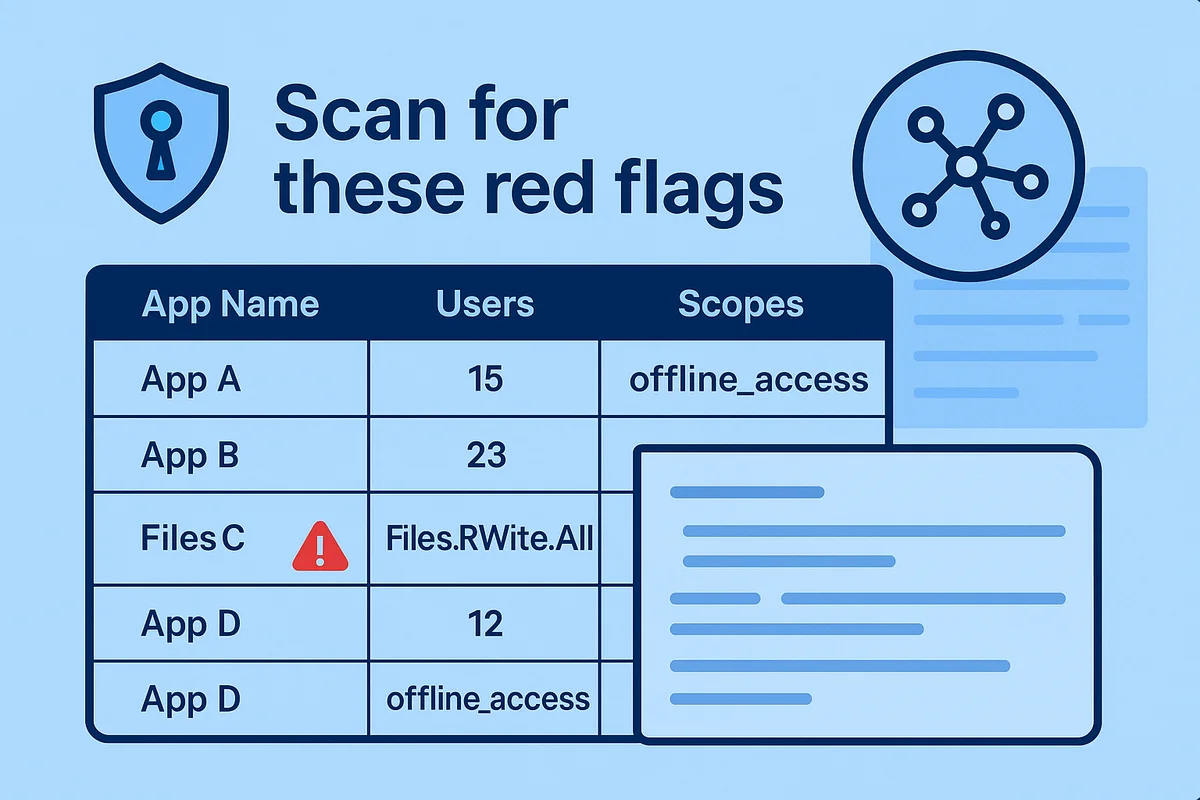
- Scan for these red flags:
offline_accessshown withChat.ReadorTeamsMessage.Send- More than ten users authorizing the app inside a 48-hour window
- Tokens older than 90 days that no one touched for the last month
- Friendly names such as “Helper,” “Sidekick,” or “CoPilot” paired with sweeping scopes
- Consent coming from guest accounts or forgotten shared mailboxes
Remember, the age of each token matters more than most teams realize.
A sudden spike signals fresh adoption, while stale yet active permissions suggest a forgotten integration still siphoning data.
Plot authorization dates against hire dates; if interns appear in the log before they join officially, someone circulated a universal link that bypassed single sign-on.
Move swiftly when reducing risk to prevent unnecessary data exposure.
Conditional access in Google Workspace can block any app asking for Files.ReadWrite.All until an admin signs off.
Okta’s workflow engine lets you yank every token from a suspicious publisher in minutes, then post a Slack notice telling users to reconnect through approved channels.
When Zapier truly needs access for an approved automation, issue a narrow-scope token and set it to expire so privileges never turn permanent.
Regular pruning welcomes innovation without leaving the vault completely open.
Audit browser extensions
Browser extensions routinely evade SaaS discovery scans and can pipe company data to outside AI engines. Chrome alone hosts more than 180,000 add-ons, while new ChatGPT helpers appear every week from unfamiliar publishers. One click on “Add to Chrome” may grant an extension access to every field you type into Salesforce, Jira, or the wiki, turning a quick productivity boost into a silent data leak.
Export a full extension roster from every managed browser on Windows, macOS, and Chromebooks. Tools you already own, such as Intune, Jamf, or the cloud policy dashboard in Google Chrome Enterprise, can dump extension IDs, publisher names, install dates, and requested permissions to a CSV. Because the list shifts all day, schedule the pull twice daily and feed the delta to your SIEM so anything new sparks an investigation before lunch.
When the file lands, scan each line for red flags that hint at generative AI traffic leaving the building.
- Permission set includes activeTab plus wildcard host access
- Code was updated within the past seven days, hinting at rapid feature drops
- Publisher domain registered less than a year ago
- Description, title, or support URL mentions “GPT,” “Claude,” “Copilot,” or “AI writer”
Flagged extensions move into a review queue where security checks the manifest.json, scans Chrome Web Store comments for data-leak complaints, and runs the code through static analysis. One twenty-minute review often uncovers hard-coded API keys or endpoints that send clipboard content straight to api.openai.com, proof the publisher never planned for enterprise controls.
Finding a risky plugin is only half the battle; removing it fast is the real metric. Push a forced uninstall through the same management console that spotted it, send the employee a brief note explaining why, then log the incident for compliance. Follow-up metrics, such as a drop in wildcard permissions and fewer support tickets about blocked extensions, show the process works and keep leadership committed.

Monitor outbound AI traffic
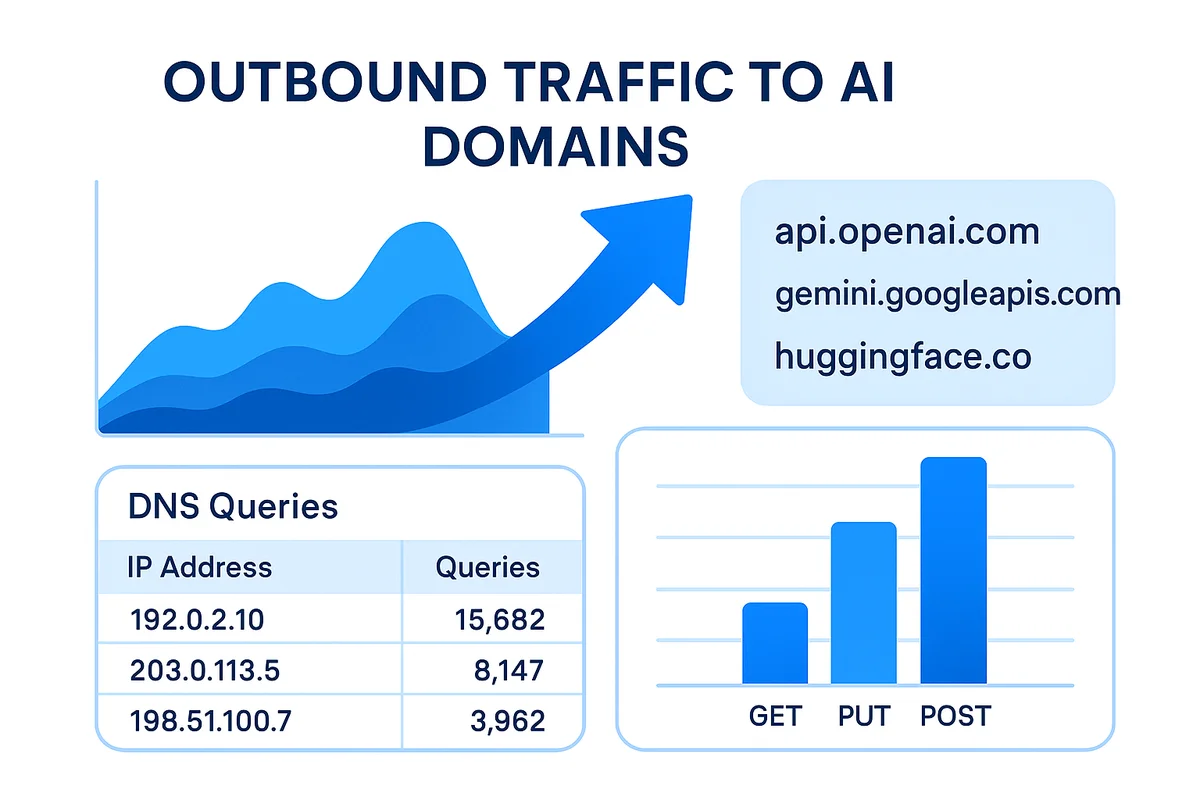
Outbound traffic shows where your company’s data goes when it leaves the perimeter. Grab raw firewall logs and CASB records instead of waiting for a tidy dashboard that glosses over the spikes.
Create a watchlist of high-velocity AI domains and match it against egress DNS queries in real time. The api.openai.com domain rarely blends in, but lesser-known endpoints like gemini.googleapis.com or Hugging Face often sit under generic “cloud services” labels and slip by until someone checks.
Volume and method quickly reveal whether the traffic is harmless testing or outright exfiltration. Short, bursty GET requests from a single laptop usually mean a developer is poking at an SDK, while steady PUT or POST streams hauling megabytes hint at a script quietly dumping spreadsheets.
Map each source IP back to your CMDB so every spike ties to a team, not a mystery host. If a content-marketing VM starts sending repeated 5 MB posts to Anthropic at 2 AM, loop in legal and privacy before assuming it is harmless.
Turn findings into action fast by converting them into practical controls.
- Redirect calls to approved AI vendors through a proxy that strips personal identifiers.
- Auto-quarantine unmanaged hosts that send more than 500 KB per hour to unvetted endpoints.
- Push a just-in-time banner reminding users that uploads may enter public training sets.
Bring these numbers to the risk committee so they can prioritize which vendors need a security review this quarter.
Interview users
Employees already spot the AI shortcuts that slide past official checks every day. Instead of hunting down every unapproved app, set up brief chats and ask for examples of tasks they speed up, drafts they refine, or code they rework with outside bots. Gartner found 41 percent of surveyed staff using generative tools without approval earlier this year, so expect a little caution and keep the groups small.
Cap the meeting at fifteen minutes and match questions to the person’s day-to-day work. A finance analyst hears “invoice verification,” a marketer hears “headline tweaks,” and a developer hears “unit test stubs,” so adjust wording so. Open with something neutral, such as “What slows you down most?”, then bring up AI; people share more when they don’t feel cornered.
These prompts draw out real details without turning the chat into an interrogation, and employees tend to open up.
- “Walk me through the last time you pasted text into an online tool?”
- “Which steps in your routine feel repetitive enough to hand off to software?”
- “Have you shared screenshots or datasets with a bot to get faster answers?”
- “If that tool disappeared tomorrow, how would your workload change?”
Capture the answers in a basic matrix that shows each workflow and its risk score. Tie the data involved, such as customer PII, source code, or revenue forecasts, to your existing classification framework so legal can spot exposure quickly. When risk runs high, move users to an approved platform or spin up a sandbox that keeps records on prem while still giving them modern language or vision models.

Conclusion
Shadow AI surfaces in budgets, logs, browsers, networks, and even casual chats. Review expense lines for AI subscriptions, examine OAuth tokens, inventory extensions, monitor outbound calls, and simply ask people what they use. Connecting finance, security, and end-user insights lets guardrails expand in step with real demand. Managed this way, the program scales without turning every experiment into a headline.
Detecting and directing shadow AI through spend reports, audit logs, browser add-ons, network traffic, and open conversations keeps work flowing and trust intact.
Audit your company’s SaaS usage today
If you’re interested in learning more about SaaS Management, let us know. Torii’s SaaS Management Platform can help you:
- Find hidden apps: Use AI to scan your entire company for unauthorized apps. Happens in real-time and is constantly running in the background.
- Cut costs: Save money by removing unused licenses and duplicate tools.
- Implement IT automation: Automate your IT tasks to save time and reduce errors - like offboarding and onboarding automation.
- Get contract renewal alerts: Ensure you don’t miss important contract renewals.
Torii is the industry’s first all-in-one SaaS Management Platform, providing a single source of truth across Finance, IT, and Security.
Learn more by visiting Torii.
Frequently Asked Questions
Generative AI often enters organizations quietly, similar to SaaS, and it can be used without approval through personal credit cards, leading to potential data leaks.
Shadow AI refers to the unauthorized use of AI tools within organizations, often without IT oversight, creating risks for sensitive data exposure.
Finance teams can analyze expense reports for suspicious charges related to AI tools and automate alerts for unapproved software purchases.
OAuth consent logs provide insights into which external services employees have granted access, helping identify potentially risky applications.
Auditing browser extensions is crucial because they can bypass security measures and may transmit sensitive company data to external AI platforms.
Organizations can analyze outbound traffic to detect unusual data flows towards high-risk AI domains and implement proactive controls.
Conducting brief interviews with employees can uncover the use of unapproved AI tools and operational inefficiencies, leading to better compliance.

