4 Ways to Monitor User Activity in Microsoft 365
Keeping track of what’s happening across Microsoft 365 can feel messy. You want enough oversight to catch risky behavior, prove compliance, and troubleshoot issues without drowning in noise. The key is knowing where to look and how to interpret the signals.
Here’s a practical walkthrough of four go-to methods: tenant-wide audit trails, sign-in and app activity, file and sharing events, and alert-driven monitoring. Then you can pick what fits, layer them, and stay confident.
Table of Contents
Use Microsoft 365’s UI
Here, you’ll use the Microsoft Purview compliance portal to search the audit log and review user activity across Microsoft 365. This is the built-in way to see who did what, and when.
Check your permissions
You need the right role to run audit searches. Microsoft’s docs list these as valid options:
- Global admin
- Compliance admin or Security admin
- Exchange roles: Audit Logs or View-Only Audit Logs
Turn on auditing
Auditing is on by default for most tenants, but it is quick to confirm.
- In the Microsoft Purview compliance portal, go to Solutions, then Audit.
- If you see Start recording user and admin activity, select it. If you do not see this, auditing is already on.
- It can take up to 60 minutes for activity to start appearing. Microsoft’s docs cover this in “Turn audit log search on or off.”
Note:
Audit (Standard) keeps most events for up to 180 days. Audit (Premium) can keep data longer. Microsoft’s “Microsoft Purview auditing solutions” doc explains retention.
Open Audit and start a new search
- In Audit, select New Search.
- Pick a Date range. Start with a smaller window to get faster results.
- Choose Activities. You can:
- Browse by service, such as SharePoint, OneDrive, Exchange, or Teams.
- Use the search box to find common actions like File accessed, File deleted, Sharing invitation created, Mailbox login, Send As, or Added member to team.
- Under Users, add one or more users to focus the results. You can also leave it blank to search all users.
- Optional filters help narrow things down:
- File, folder, or site URL for SharePoint and OneDrive activity
- IP address
- Workload or location
Microsoft’s “Search the audit log in the Microsoft Purview compliance portal” doc walks through these filters.
Run the search and review results
- Select Search. Results list each event with the activity, user, time, item, IP address, and workload.
- Select any record to open the details panel. Look for who did it, what changed, the target item or mailbox, the client IP, and the outcome.
- If you get too many results, add a user, tighten the date range, or pick fewer activity types. Then run the search again.
Export or save your query
- Select Export results to download a CSV. You can export all results or just the ones now listed.
- Select Save query to reuse the same filters later. This helps when you run the same checks each week.
Microsoft’s docs cover both in “Export audit search results to a CSV file.”
Set up an alert policy for ongoing monitoring
If you want a heads-up when certain actions happen, create an alert policy.
- In the Purview compliance portal, go to Solutions, then Alerts, then Alert policies.
- Select New alert policy.
- Name it, pick an activity to watch, choose users or all users, set the alert threshold, and add who should get emails.
- Turn it on and save.
This is outlined in Microsoft’s “Create alert policies in the Microsoft Purview compliance portal.”
Quick doc references to look up in Microsoft Learn
- Search the audit log in the Microsoft Purview compliance portal
- Turn audit log search on or off
- Microsoft Purview auditing solutions
- Export audit search results to a CSV file
- Create alert policies in the Microsoft Purview compliance portal
Use Torii
Instead of working inside Microsoft 365 directly, you can use Torii, a SaaS Management Platform, to track Microsoft 365 user activity. SMPs centralize your SaaS subscriptions in one dashboard, giving you a single source of truth across all your tools.
To monitor Microsoft 365 user activity from Torii, do the following:
1. Sign up for Torii
Contact Torii and request a complimentary two-week proof of concept.
2. Connect your Microsoft 365 account to Torii
Once your Torii environment is active, link your Microsoft 365 tenant to Torii (assuming you already have an account). Here are the instructions for the Microsoft 365 integration.
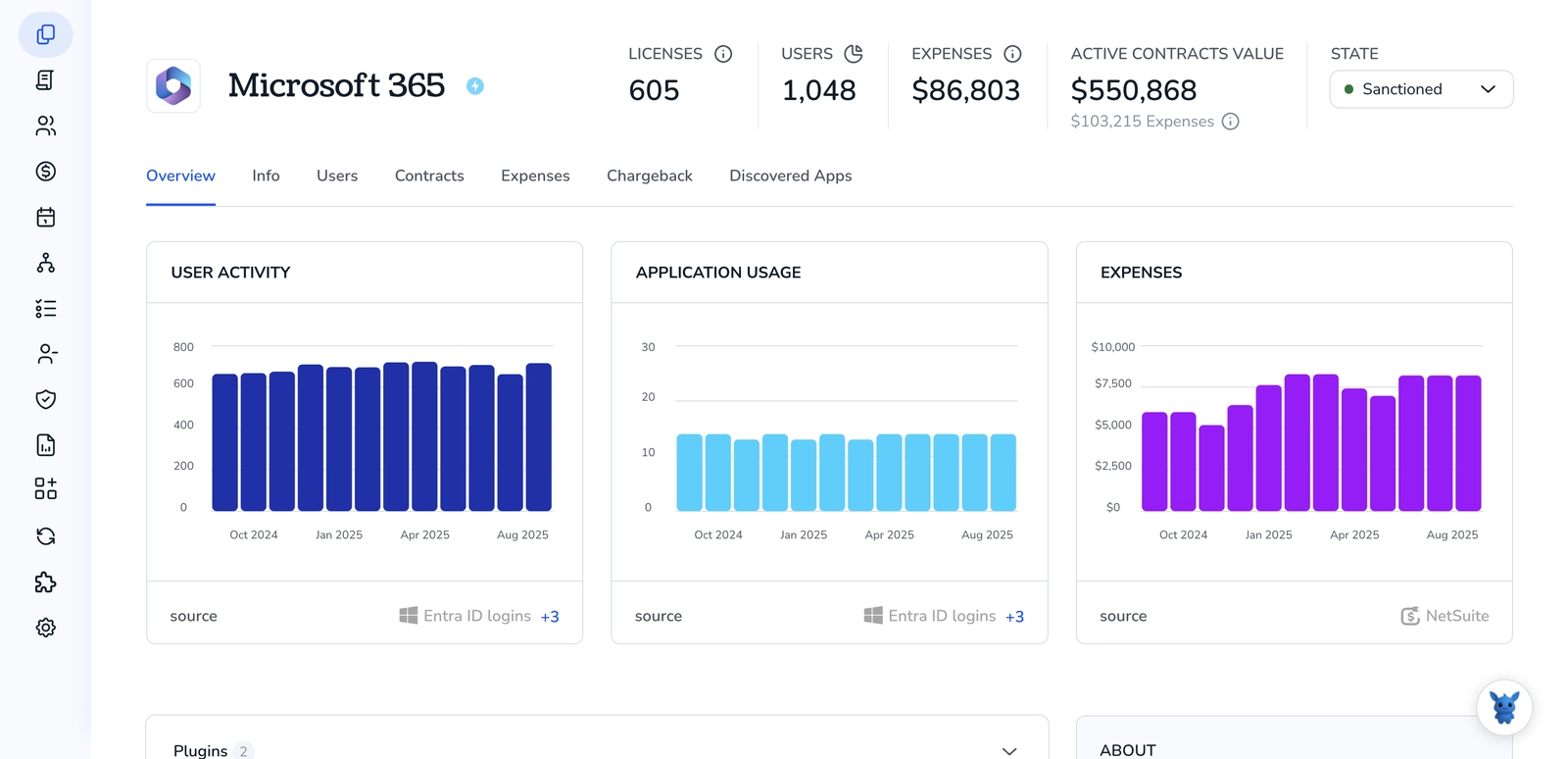
3. Search for Microsoft 365 within Torii
Use the search bar at the top of the Torii dashboard to find Microsoft 365. This opens your Microsoft 365 app page, where you can review details like license counts, total spend, upcoming renewal date, and more.

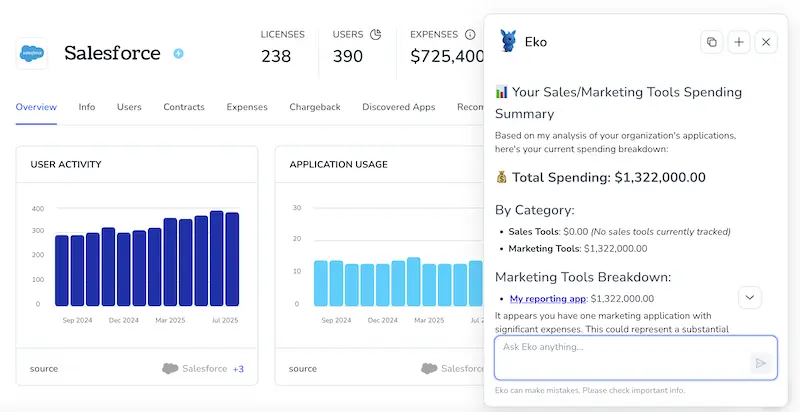
Or, chat with Eko
Torii’s AI helper, Eko, enables you to retrieve Microsoft 365 details inside Torii through a natural-language chat. Click the Eko icon in the lower-right corner of the dashboard and ask for Microsoft 365 information. The results will appear right in the chat window.
Use Microsoft 365’s API
Here, you’ll use Microsoft Graph endpoints to pull sign-in logs, directory audit events, and service usage reports. This gives you a reliable feed without touching any admin UI.
Get an access token with the right permissions
Use OAuth 2.0 client credentials to call Microsoft Graph. Your app needs these application permissions, consented by an admin:
- AuditLog.Read.All for sign-ins and directory audits
- Reports.Read.All for usage reports
Example curl is:
curl -X POST "https://login.microsoftonline.com/{tenant-id}/oauth2/v2.0/token" \
-H "Content-Type: application/x-www-form-urlencoded" \
-D "client_id={client-id}&client_secret={client-secret}&scope=https%3A%2F%2Fgraph.microsoft.com%2F.default&grant_type=client_credentials"
The response includes access_token. Use it in the Authorization header.
Pull sign-in activity from audit logs
The Microsoft Graph auditLogs signIns endpoint returns each sign-in, including app, IP, location, and status. Filter by time and user to keep calls fast.
Example curl is:
curl -X GET "https://graph.microsoft.com/v1.0/auditLogs/signIns?$top=50&$filter=createdDateTime ge 2025-08-01T00:00:00Z" \
-H "Authorization: Bearer {access-token}"
To focus on a single account by object ID:
curl -X GET "https://graph.microsoft.com/v1.0/auditLogs/signIns?$top=50&$filter=createdDateTime ge 2025-08-01T00:00:00Z and userId eq '00000000-0000-0000-0000-000000000000'" \
-H "Authorization: Bearer {access-token}"
Notes:
- Use $top to control page size. If @odata.nextLink is present, follow it until exhausted.
- CreatedDateTime is the standard cursor for incremental reads.
Pull directory audit events
Use auditLogs directoryAudits to see changes like user updates, group membership, and app admin actions.
Example curl is:
curl -X GET "https://graph.microsoft.com/v1.0/auditLogs/directoryAudits?$top=50&$filter=activityDateTime ge 2025-08-01T00:00:00Z and category eq 'UserManagement'" \
-H "Authorization: Bearer {access-token}"
Tips:
- Common categories include UserManagement, GroupManagement, ApplicationManagement, RoleManagement.
- Use activityDateTime as your incremental cursor.
Pull per-user service activity reports
For workload-level user activity (Teams, Exchange, OneDrive, SharePoint), use the Microsoft Graph Reports API. These endpoints return CSV streams.
Teams example, last 7 days:
curl -L -X GET "https://graph.microsoft.com/v1.0/reports/getTeamsUserActivityUserDetail(period='D7')" \
-H "Authorization: Bearer {access-token}" \
-H "Accept: text/csv"
OneDrive example for a specific day:
curl -L -X GET "https://graph.microsoft.com/v1.0/reports/getOneDriveActivityUserDetail(date=2025-08-17)" \
-H "Authorization: Bearer {access-token}" \
-H "Accept: text/csv"
Other useful endpoints:
- Reports getEmailActivityUserDetail for Exchange email activity
- Reports getSharePointActivityUserDetail for SharePoint activity
Make the calls incremental and reliable
Store cursors so you only fetch new data each run.
- For sign-ins: last seen createdDateTime
- For directory audits: last seen activityDateTime
- For reports: last processed date or period window
Example pattern:
- Keep the most recent timestamp from your last page.
- On the next run, pass that timestamp plus one second in your $filter.
Handle paging and throttling
- If the response includes @odata.nextLink, call it until all pages are read.
- On HTTP 429 or 503, wait the Retry-After value, then try again.
- Keep $top modest, for example 50–200, to reduce retries during busy periods.
Join and normalize events
Unify by these common fields to get a clean user timeline:
- UserId and userPrincipalName
- IpAddress
- AppId or appDisplayName
- timestamps: createdDateTime for signIns, activityDateTime for directoryAudits
This gives you a single feed across sign-in events, directory changes, and workload activity, all from Microsoft Graph’s documented resources: auditLogs signIns, auditLogs directoryAudits, and Reports API user detail endpoints.
Frequently Asked Questions
You can monitor Microsoft 365 using four methods: search tenant audit logs in Microsoft Purview, create alert policies, integrate a SaaS management platform like Torii, or pull sign-in, directory, and usage reports via Microsoft Graph APIs.
To run audit searches you need roles like Global admin, Compliance admin, Security admin, or Exchange Audit Logs/View-Only Audit Logs. For API access use application permissions consented by an admin such as AuditLog.Read.All and Reports.Read.All.
In Purview go to Solutions > Audit and select Start recording user and admin activity if present. Wait up to 60 minutes for events, then choose New Search, set date range, pick activities and filters, run the search, and export or save queries.
Torii centralizes SaaS data: sign up for a trial, connect your Microsoft 365 tenant, open the Microsoft 365 app page to view licenses, spend and renewals, and use Eko, Torii's chat assistant, to ask natural-language questions about user activity.
Use Microsoft Graph endpoints: auditLogs/signIns for sign-ins, auditLogs/directoryAudits for directory changes, and Reports get*UserDetail endpoints for workload activity. Authenticate with OAuth client credentials and request AuditLog.Read.All and Reports.Read.All as application permissions.
Make API pulls incremental by storing the latest createdDateTime or activityDateTime, handle @odata.nextLink paging until exhausted, respect Retry-After on HTTP 429/503, and keep $top modest (50–200) to reduce throttling and retries.

