The Top 10 Employee Onboarding Tasks For IT in 2026

Every new hire shows up eager to get started, yet overlapping tools can slow them down. Manually stitching together accounts, policies, and permissions across dozens of SaaS apps drains admins and tests patience on day one.
Here’s a smarter, faster approach for organizations managing modern tech stacks. By automating identity creation, SSO links, RBAC mapping, MFA enrollment, and license sizing, teams reclaim hours once lost to repetitive setup work. New employees begin productive work on day one, and auditors see clean, timestamped trails.
Line these tasks up in order and you’ll build an onboarding engine you can trust every time. It delights employees, keeps regulators comfortable, and frees IT to chase real innovation instead of fixing accounts.
Table of Contents
- Automate Identity and Account Provisioning
- Set Up Single Sign-On
- Apply Role-Based Access Control
- Enforce Multi-Factor Authentication
- Assign Correct SaaS License Tiers
- Create Self-Service SaaS Request Workflows
- Sync Directories with SCIM
- Enforce Device-Based SaaS Access
Automate Identity and Account Provisioning
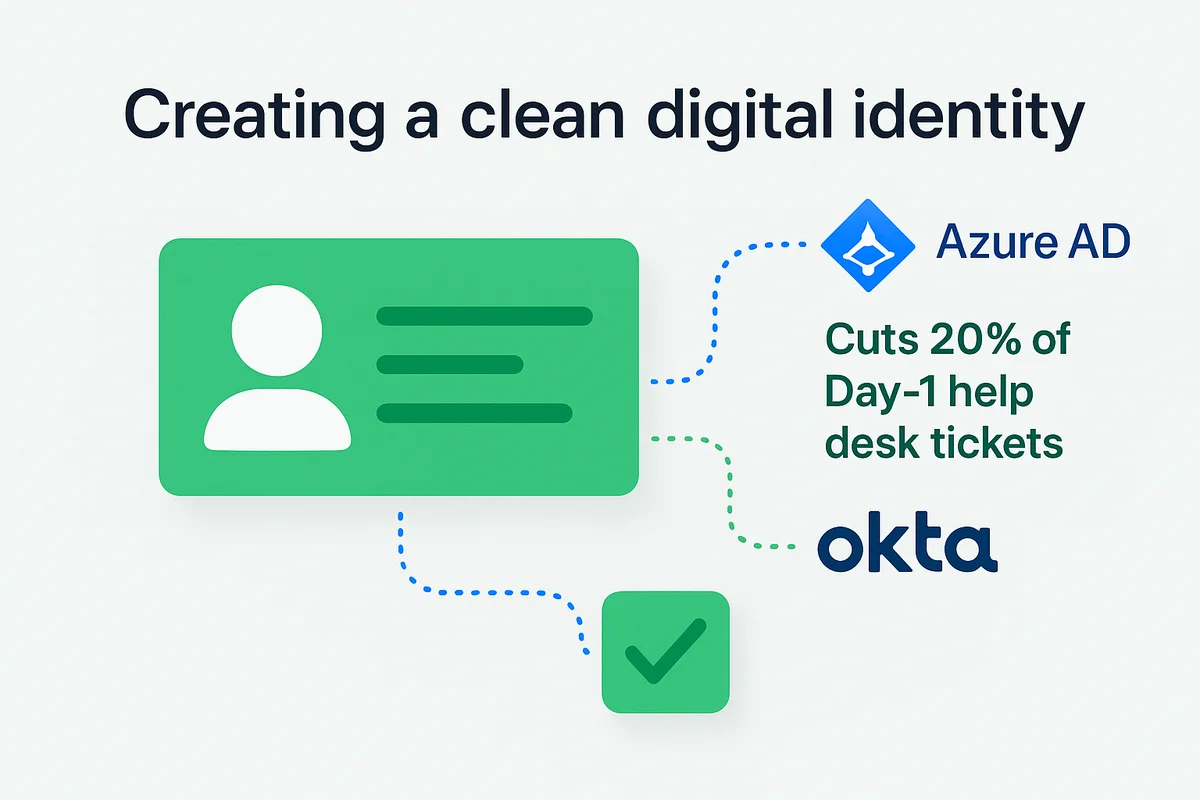
Creating a clean digital identity first keeps every later onboarding step from wobbling out of alignment.
Most teams start in Workday or a similar HR system, which kicks off a “new-hire” event. The real work begins when Azure AD or Okta picks up that webhook and builds the user object in seconds. The directory record becomes the single source of truth; every SaaS tool trusts it, nothing is typed twice, and Gartner notes that this cuts 20 percent of Day-1 help desk tickets. Templates handle much of the heavy lifting. Pick Sales, Engineering, or Finance, and the platform autofills department, location, and manager fields so you do not chase missing metadata later.
The same push adds the person to Google Workspace, Slack, and Jira without bouncing between admin consoles. Each downstream app receives a SCIM payload that maps attributes as they sit in the directory. Audit logs in the IdP show what was created, by whom, and at what time, which is handy when ISO 27001 auditors come knocking.
- HR creates the worker record and sets start date.
- Directory service ingests the record and applies the role template.
- SCIM connectors push identities to targeted SaaS apps.
- Help desk verifies completion through the IdP activity feed.
# Sample event: Workday webhook to Okta
curl -X POST https://example.okta.com/api/v1/scim/v2/Users \
-H "Authorization: SSWS ${TOKEN}" \
-H "Content-Type: application/scim+json" \
-D '{
"userName": "[email protected]",
"name": { "givenName": "Tara", "familyName": "Lee" },
"active": true,
"groups": ["Sales-NewYork"]
}'
Even a lightweight script like the one above removes keystrokes that invite typos or duplicate accounts. If the hire’s start date shifts, the record stays dormant until that day, then wakes up automatically. Finance no longer pays for orphaned seats, IT stops playing spreadsheet tag, and the new employee opens her laptop to find every core app ready. Users remember that kind of welcome.
Set Up Single Sign-On
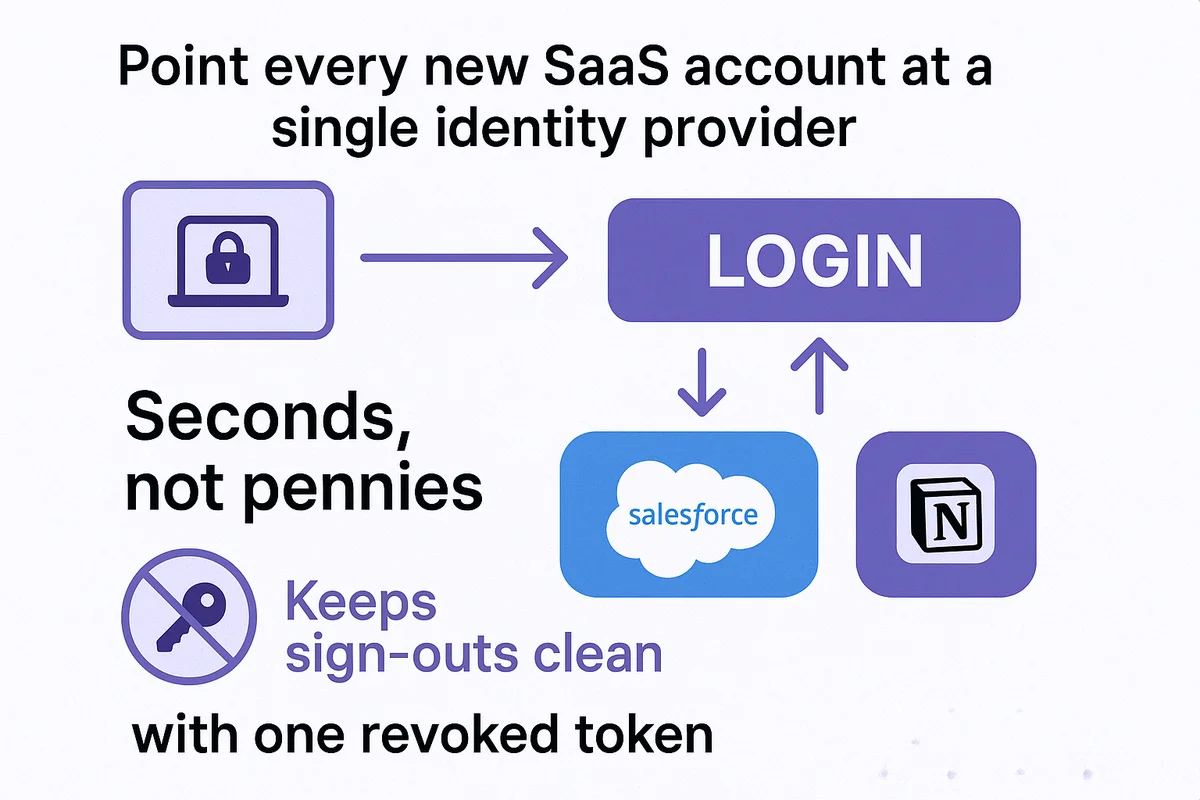
Every extra password your employee types costs seconds, not pennies. The fix is simple: point every new SaaS account at a single identity provider so workers click once and get on with real work. Centralizing logins also keeps sign-outs clean because one revoked token now shuts dozens of doors instead of one.
Choosing the right connector usually comes down to which protocols the app speaks. SAML 2.0 rules mature enterprise apps like Salesforce, while newer tools such as Notion often lean on OIDC. Both use secure assertions, yet SAML needs an X.509 certificate that expires, usually every one to three years. Mark that date in your ticketing system before it sneaks up and causes an outage. OIDC swaps certificates for rotating JSON Web Tokens, so the blast radius of a lost key stays smaller.
Wiring the flow takes minutes once the groundwork is clear.
- Export the metadata file from Azure AD or Okta and drop it into the SaaS admin console.
- Select IdP-initiated for apps showing a dashboard launcher; choose SP-initiated when users bookmark direct URLs.
- Map
email,firstName, andlastNameto the app’s schema, then flip the switch to “required.” - Test with a non-admin account, capture the SAML response in your browser dev tools, and keep that screenshot for auditors.
Profile synchronization matters just as much as authenticating users in the first place. Push optional attributes like department and manager so org charts auto-populate inside project spaces and chat profiles. Salesforce can even convert those fields into territory rules, while Notion uses them to pre-share team workspaces. Keep attribute names consistent with your SCIM directory to dodge case-sensitivity bugs. Finally, enable automatic certificate rollover if your IdP offers it, then save a backup copy in a secrets vault to protect against accidental deletion. Now the next new hire clicks once, signs in everywhere, and never knows how many moving parts you just hid behind that blue login button.
Apply Role-Based Access Control
Granting the wrong access on day one costs real money and time. The 2019 Verizon DBIR attributed 45 percent of insider incidents to privilege misuse, highlighting how quickly extra permissions turn into genuine risk.
Begin by looking at the role data HR already keeps for every employee. Each job code such as Sales AE, Marketing Ops, or Dev Engineer maps to a bundle of SaaS permissions, not to a person. Store that bundle in a small JSON file or in the CMDB so it sits in source control and can be reviewed like any other change. When a new hire record appears, the identity platform reads the job code and pushes the right entitlements to every connected app.
Real traction shows up only when automation replaces the usual ticket queues. A simple Terraform plan can turn those JSON bundles into live roles, while an Azure AD dynamic group handles incremental adds and drops without human clicks. If someone moves from Sales-AE to Sales-Manager, HR changes one field, and the system removes the old access before layering on the manager entitlements.
Keep the matrix evergreen by tagging each permission with an owner and review date inside the CMDB. Quarterly, route a report to owners showing which roles granted what, then force an approve-or-remove decision. The audit trail is automatic: who changed the JSON, when the pipeline ran, and what entitlements landed. Compliance teams get proof, security gets least privilege, and new hires walk away with only what they need, nothing more and nothing less.
Leading access control companies like Coram can also provide these advanced tools that help organizations achieve this level of control and responsiveness, offering AI-driven automation, real-time access monitoring, and seamless policy enforcement across complex environments.

Enforce Multi-Factor Authentication
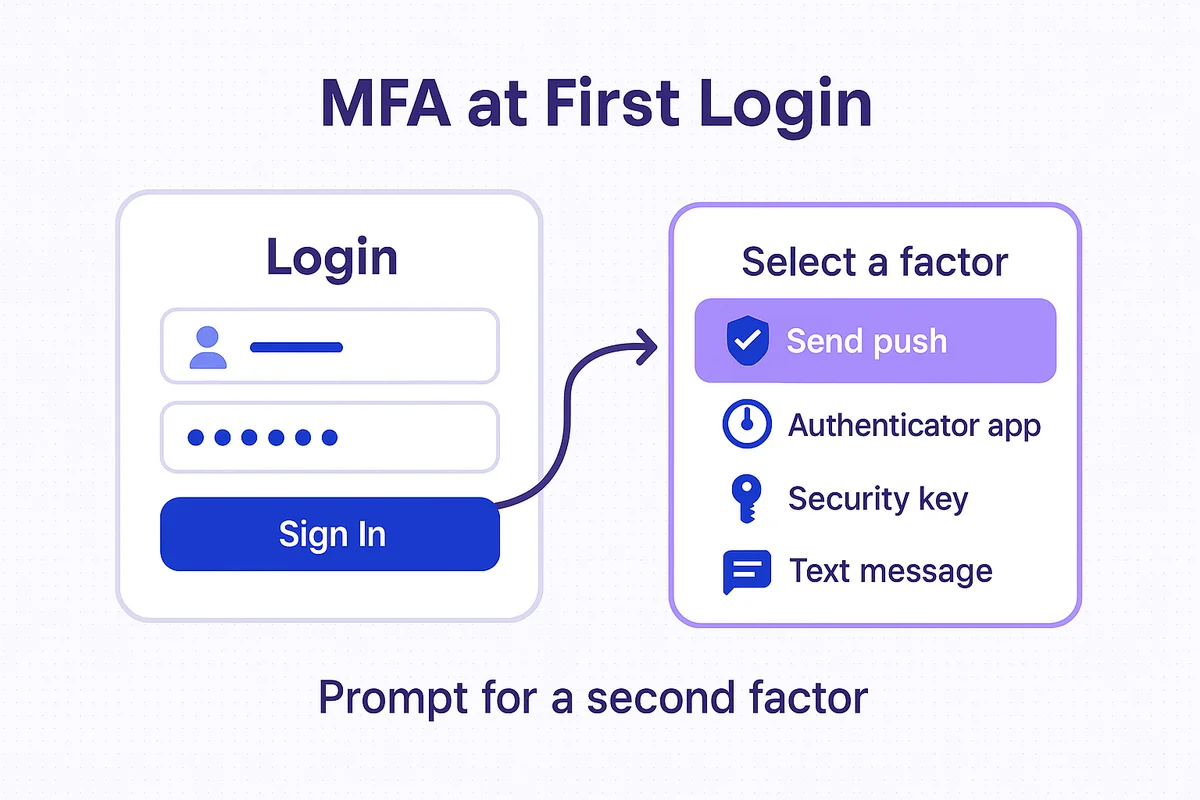
When a new hire reaches the login screen for the first time, multi-factor authentication (MFA) should appear immediately. Running on passwords alone, even for a day, gives automated credential-stuffing tools time to poke around. Prompting for a second factor at that first login shuts out attackers while the employee gets oriented.
Offer multiple options so enrollment feels quick rather than forced. Most teams accept any of these factors that meet NIST AAL2:
- Push notification from Duo or Microsoft Authenticator
- Time-based one-time code from an authenticator app
- FIDO2 hardware key such as YubiKey
- Verified SMS as a fallback that expires in five minutes
MFA guards the front door, yet session rules control how long it stays open. Configure conditional access to limit logins from unknown IP ranges, set idle timeouts to thirty minutes, and require passwordless sign-in the moment a supported device appears. When Intune tags a laptop as non-compliant, the IdP should cut off GitLab access within seconds, not hours.
Regulators and security auditors now assume MFA is enabled by default. SOC 2, ISO 27001, and most customer security questionnaires simply expect it, and Microsoft notes that 99.9 percent of automated account-takeover attempts fail once a second factor is in place. Keeping audit evidence simple helps later; store enrollment timestamps, device IDs, and any bypass events in the same log bucket you use for SSO activity.
Even with clear docs, plenty of users still stumble during enrollment. Keep a short “first-day” checklist in reach:
- Confirm the phone’s clock is set to automatic time
- Ask users to try Wi-Fi and cellular in case push fails
- Clear existing tokens before re-registering a recycled phone number
- Offer a temporary code so work can start while support investigates
Fold these steps into your onboarding playbook, and security stays in charge without slowing down that first morning.
Assign Correct SaaS License Tiers
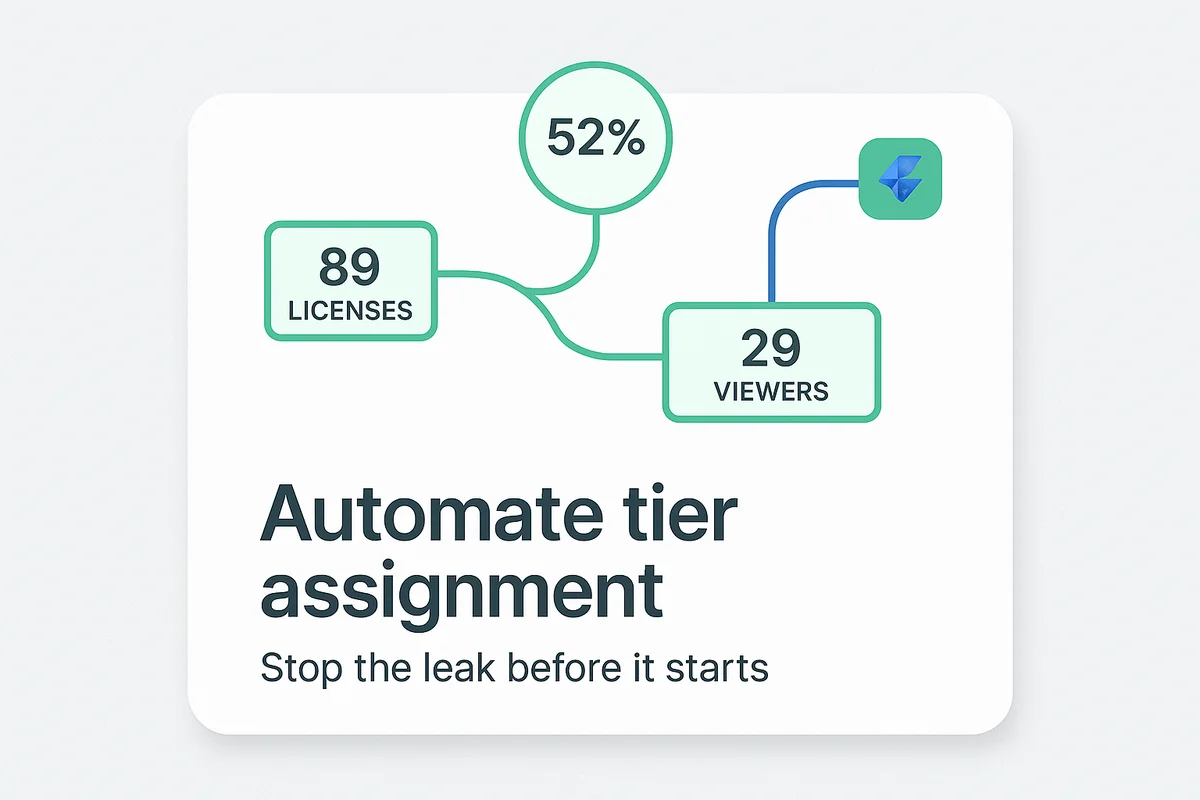
Tracking licenses sounds mundane, yet it can drain budgets faster than forgotten cloud workloads. If you automate tier assignment the minute an employee lands, you stop the leak before it starts.
Plenty of SaaS vendors quietly expose their license controls through a straightforward API endpoint. A single POST to /subscriptions/{id}/assign in the Figma admin API flips a user from free Viewer to paid Editor. When this call sits inside your onboarding playbook, HR system data decides the tier rather than someone eyeballing a spreadsheet. Finance likes the predictability; new hires like having the right tool set without a help-desk ticket.
Build a lightweight rules engine that turns job title and location into spend caps. For example, anyone tagged “Contractor” receives only viewer or read-only seats. Staff engineers in high-cost regions might default to premium seats because latency reductions matter more than pennies. The same logic can reserve a pool of floating licenses for interns so you never hit a hard stop during peak hiring months.
Automated checks still need human guardrails, so surface exceptions before they become invoices. A daily Lambda function can compare active seat count against cost-center budgets, then post a quick digest to Slack. If Creative burns through its Adobe allotment mid-quarter, the director sees the alert and decides whether to free seats or approve more spend. No surprise true-ups at renewal.
Make the entire license-management setup visible to everyone who touches budgets or security reviews. A shared Notion page that lists license targets, current usage, and savings makes procurement reviews painless and helps security spot orphaned entitlements left by role changes. The page updates itself through webhook feeds and doubles as audit evidence during SOC 2 reviews.
Here are a few tactics worth folding into your onboarding pipeline, each proven to shave real dollars off the IT budget:
- Map HR data to specific SKU codes before the user object hits the SaaS API.
- Trigger seat reassignment when a role changes, not just during exits.
- Reclaim unused seats automatically after 30 days of inactivity, logging the reclaimed value per user.
Create Self-Service SaaS Request Workflows
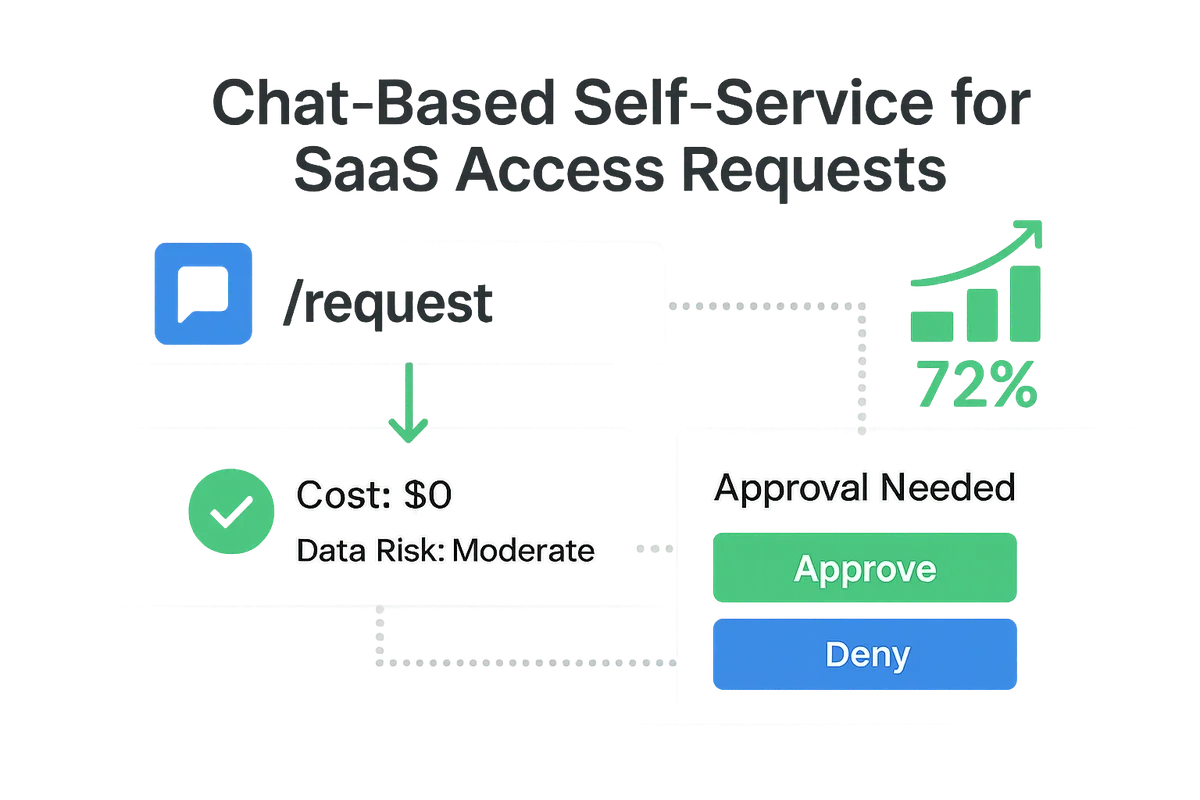
Employees still bump into fresh SaaS needs long after onboarding, and IT can’t foresee each one. Meeting those requests quickly without losing control starts with a chat-based self-service workflow that feels like sending a DM while still giving Security a clean audit trail.
A typical flow kicks off when a user types /request in Slack or Microsoft Teams and picks the app from an adaptive card. The bot pulls cost and data-risk details from your SaaS inventory, then asks two quick questions: business purpose and sensitivity of data involved. Because the bot reads the employee’s profile from the IdP, it auto-fills department and manager, shaving minutes off the form.
The next step is straightforward: route the request to the right approver. The manager receives a rich notification with one-click approve or deny buttons, while a background webhook opens a ticket in ServiceNow or Jira Service Management. If the request touches regulated data, a second approver from Security can be inserted before provisioning kicks off. Every decision, timestamp, and comment lands in the ITSM record, satisfying auditors without extra screenshots.
Collecting the same details for every request turns into real value later. Finance teams can filter tickets by “business purpose” to spot overlapping tools, and Security can flag apps that store personal data but lack encryption. Zylo’s 2023 SaaS Management Index showed companies that tag requests with purpose and owner reduced shelf-ware by 30 percent in the first year, a direct budget win.
Rolling this out feels manageable when you break the project into small pieces:
- Build the request form in your chat platform’s low-code builder.
- Map form fields to ITSM ticket fields through a webhook or middleware like Workato.
- Create approval rules that reference IdP attributes, not hard-coded email lists.
- Set the ticket’s resolved status to trigger your existing provisioning automation.
- Schedule monthly reports that highlight denied requests and orphaned tickets.
Start small with three high-demand apps, gather feedback, then expand. Within a quarter, employees stop guessing “who owns Asana” and IT gains a searchable ledger of every SaaS choice the company has ever made.
Sync Directories with SCIM
User details change weekly, and your SaaS stack needs to keep up. Left unchecked, stale records cascade into license waste, misrouted emails, failed security alerts, and a backlog of IT tickets.
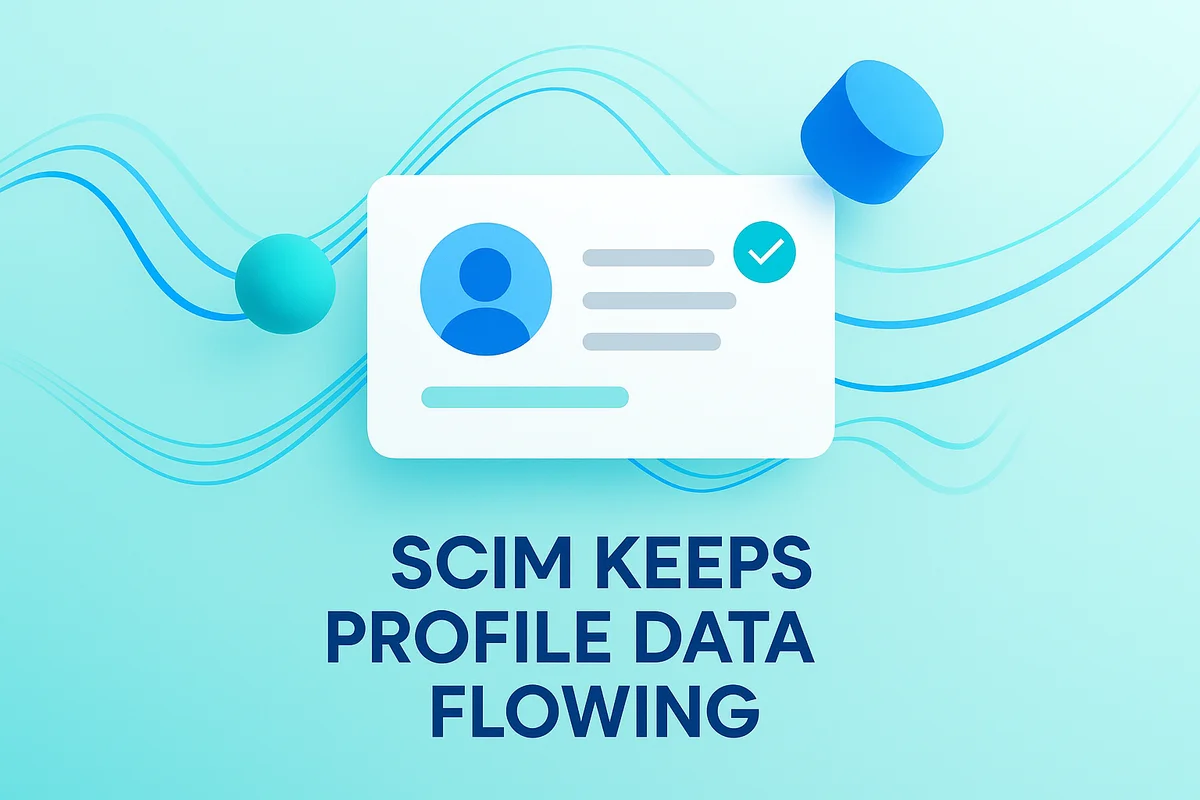
SCIM keeps profile data flowing from your identity provider to each cloud app without spreadsheets or midnight scripts. Instead of waiting for IT to update names, titles, or phone numbers by hand, the IdP sends a JSON payload the moment HR edits the record. That update lands inside every connected tool almost instantly, so sales doesn’t email the wrong alias and finance doesn’t inflate seat counts for departed staff.
Most modern apps speak SCIM, but each one hides the switch in a different place. In Asana you flip it on under Admin Console → Security, paste the bearer token from Azure AD, then map fields like department and manager so boards auto-sort by team. Zoom takes two steps: enable the “Automatic User Provisioning” toggle, then set a default license type for new accounts so you never hand out an accidental Large Meeting add-on. That five-minute setup means new hires appear in both apps, complete with profile pictures, before they finish orientation.
At a protocol level, versions still trip plenty of people up. Some vendors still run SCIM 1.1, which ignores custom attributes unless you build a schema extension. If you absolutely need a field like costCenter, define it in the IdP once, then reference the full URI in every PATCH call. When a connector refuses the update, grab the app’s /ServiceProviderConfig endpoint to confirm supported operations rather than playing ticket tennis with support.
Keep a concise, easily referenced checklist on hand to spot sync drift:
- Confirm the daily delta report shows zero failed updates.
- Compare user counts in the IdP and target app.
- Audit for duplicate accounts created outside SCIM.
- Verify critical attributes such as
roleandstatuspopulate correctly.
Enforce Device-Based SaaS Access
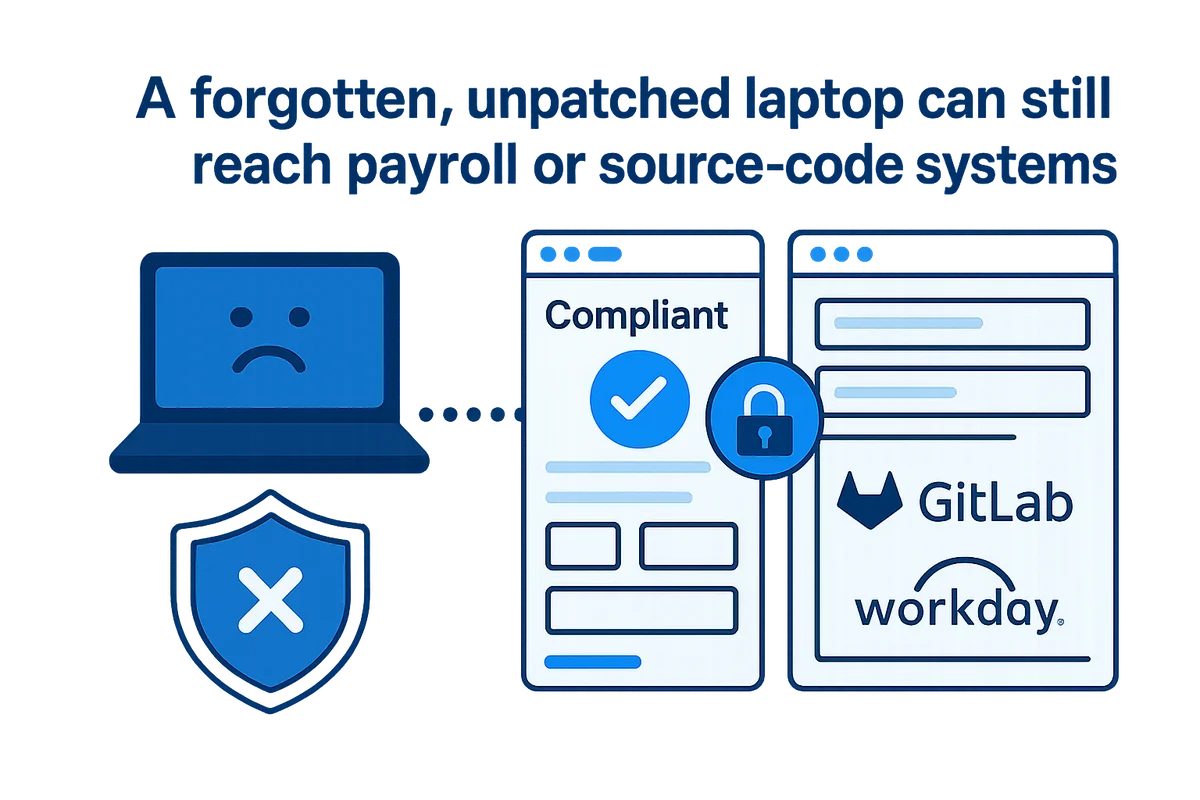
A strong identity plan collapses if a forgotten, unpatched laptop can still reach payroll or source-code systems.
Tie SaaS logins to mobile device management and that gap closes fast. Conditional access in Azure AD or Okta treats the device as a second factor, reviewing encryption, OS version, and threat signals before granting access. If the laptop fails even one check, the user lands on a remediation page rather than sensitive dashboards, removing the risk without a ticket.
Rolling out these compliance checks across your device fleet is straightforward. In Microsoft Intune create a compliance policy that enables FileVault or BitLocker, blocks operating systems older than two versions, and flags jail-broken phones. Map the policy to a “Compliant” group, then tell Azure Conditional Access to allow GitLab and Workday only for that group. Teams running all-Apple hardware can mirror the setup in Kandji with a single blueprint that verifies Secure Boot, notarized apps, and an active firewall.
- Full-disk encryption required before a token is issued
- Automatic OS patch check every eight hours with a 48-hour grace window
- Real-time antivirus status pulled from the endpoint security API
- Block login from browsers missing a modern TLS version
- Silent enrollment of a recovery key into the company vault
- Location-based rule that blocks logins from embargoed countries
- Forced device check-in every 30 minutes to prevent drift
When a device drifts out of compliance, automation should fix the issue rather than lock the door. Intune can push a Company Portal alert that guides the user through encryption or an update, while Kandji can run a script that re-enables the firewall, logs the action in Slack, and retries the login. The self-service flow keeps people working and saves the help desk.
Microsoft saw a 99.2-percent drop in credential-based attacks at companies combining MFA with device compliance. Lock down the endpoint, tie it to identity, and every other control in your onboarding playbook gains leverage.
Create Onboarding Checklist and Audit Log
During a hire’s first hour, IT changes stacks quickly across multiple SaaS tools. A shared, living checklist inside a single workspace keeps every step visible to IT, managers, and auditors at once. When that sheet sits in Confluence or Notion, anyone with the right role can watch tasks flip from pending to done in real time, ensuring every welcome gift and security rule lands on schedule.
Use one checklist template for every team instead of scattered copies in private drives. Fill it with every mandatory action, not just the headline-grabbing first-day rituals. The list usually covers:
- HRIS record received and identity created
- SSO linked to IdP and baseline MFA enforced
- Role group applied and license tier assigned
- Device compliance confirmed via MDM policy
- New hire notified of self-service request bot
Checking a single box can do more than simply mark progress. Behind the scenes, that click triggers a webhook that pings downstream systems. Mark “license tier assigned,” and an API can bill the cost center, update finance, and stamp a timestamp in the activity table without another mouse movement.
A checklist alone is hollow unless every change lands in an immutable log. Stream each action to a write-once store such as AWS S3 with Object Lock so even root admins cannot rewrite history. Add the user’s GUID, the Jira Service Management ticket ID, and the exact JSON payload that touched the SaaS API so future reviewers see the full story. That detail saves hours when an auditor asks why a marketing intern briefly held GitHub admin rights six months ago.
When auditors can filter by employee email, date, or control name and instantly view the chain of custody, they stop chasing edge cases and close the file faster. That smaller audit window puts the engineering team back to building sooner.

Schedule Access Reviews and Offboarding
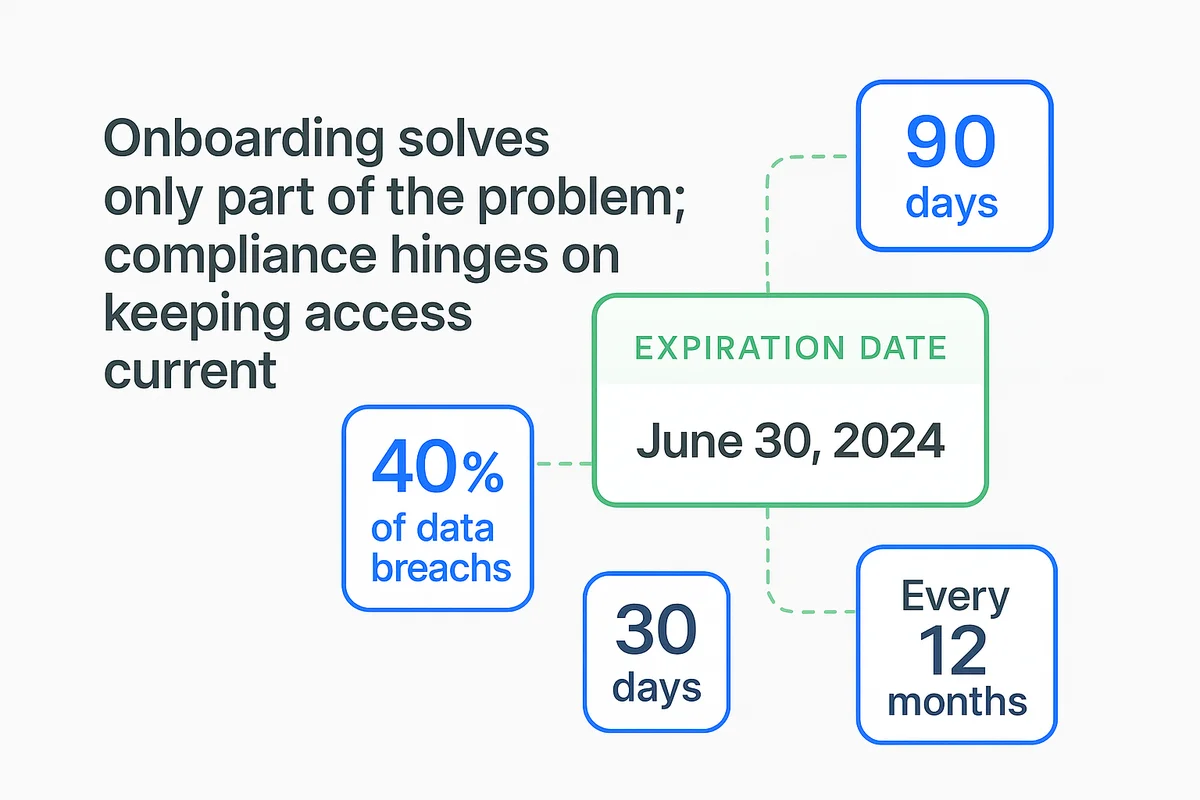
Onboarding solves only part of the problem; compliance hinges on keeping access current. Gartner estimates that 40 percent of data breaches trace back to accounts that should have been disabled. Waiting for a manager to file a ticket is slow and risky, so bake the timing into the workflow from day one. Every SaaS seat should carry an expiration date the moment it is assigned, and the clock should trigger both reviews and offboarding actions without additional clicks.
Access certifications work best when they feel routine, not punitive. Set your identity platform to email managers a quick checklist that auto-populates the user’s current entitlements, then expires after seven days to force a decision. A simple cadence keeps the workload predictable:
- 30 days after hire for the first sanity check.
- 90 days to catch role changes that slipped past HR.
- Every 12 months to align with SOC 2 and ISO annual audits.
Tie each approval or removal to a ticket ID so auditors can retrace the decision path later.
Effective offboarding requires minimal human involvement when the right hooks are in place. When an HRIS marks a departure in Rippling or BambooHR, a webhook should fire that deactivates the directory object, revokes OAuth refresh tokens, and frees paid licenses simultaneously. Many teams add a five-minute delay to let critical workflows finish, then run a scripted sequence that touches every high-risk system in priority order, for example: Salesforce, AWS, GitHub, Slack. If a system is offline, log a retry event so nothing slips through the cracks.
More than a few data-retention rules can block immediate deletion. Create a “parking lot” group with zero privileges that freezes the account while maintaining mailbox or repository data until Legal signs off. After the retention window closes, a second automation can purge the account and update the immutable onboarding log that tracks every lifecycle event.
Conclusion
New employees hit the ground running once IT automation strips away first-day friction. When identity creation, single sign-on, role mapping, multi-factor prompts, and license right-sizing run in a single flow, teams reduce manual work and deliver access without a sea of tickets. The same system also supports self-service requests, SCIM sync, device checks, and audit trails.
Automating these onboarding steps makes setup repeatable, boosts productivity, and meets compliance requirements without slowing the business.
Audit your company’s SaaS usage today
If you’re interested in learning more about SaaS Management, let us know. Torii’s SaaS Management Platform can help you:
- Find hidden apps: Use AI to scan your entire company for unauthorized apps. Happens in real-time and is constantly running in the background.
- Cut costs: Save money by removing unused licenses and duplicate tools.
- Implement IT automation: Automate your IT tasks to save time and reduce errors - like offboarding and onboarding automation.
- Get contract renewal alerts: Ensure you don’t miss important contract renewals.
Torii is the industry’s first all-in-one SaaS Management Platform, providing a single source of truth across Finance, IT, and Security.
Learn more by visiting Torii.
Frequently Asked Questions
Automating identity creation ensures that new hires can start their work immediately without delays caused by manual account setup, leading to increased productivity from day one.
Single Sign-On (SSO) simplifies login for new employees, allowing them to access multiple applications with a single set of credentials, thus improving efficiency.
Role-based access control ensures that new employees receive appropriate permissions based on their job roles, minimizing security risks associated with over-provisioning access.
MFA enhances security during the onboarding process by requiring additional verification steps, making it more difficult for unauthorized users to gain access to sensitive systems.
Automating license tier assignments ensures that employees receive the correct licenses based on their roles, preventing budget waste from unnecessary or unused licenses.
A self-service SaaS request workflow streamlines the process for employees to request new applications, ensuring efficient handling while maintaining security oversight.
Syncing directories with SCIM automates user details updates across applications, reducing manual data entry errors and ensuring accurate information is available in real time.

