3 Ways to Add Users to Your OpenAI Account in 2026
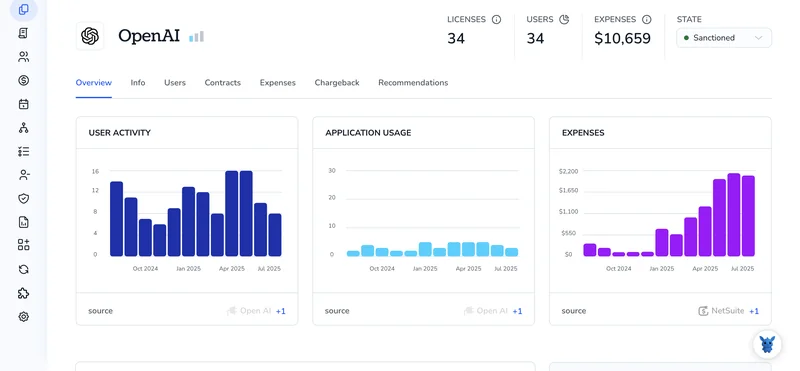
Managing who can access your OpenAI account matters for collaboration, security, and billing. I know it can feel tricky; this guide lays out three practical ways to add users: invite teammates, have new users register, or grant direct access when needed.
I’ll walk through each method, explain relevant roles and permissions, and give quick tips to avoid common setup problems.
Table of Contents
Use OpenAI’s UI
Here, you’ll use the OpenAI UI to add a user to your organization and set their role.
Open the organization or account settings
- Sign in to your OpenAI account.
- Click your profile or organization name in the top-right corner.
- Choose
Manage organizationorOrganization settingsfrom the menu (label may vary).
Find the members or people page
- In organization settings, open the
Members,People, orTeamtab. - This page lists current members, pending invites, and role info.
Invite a new user
- Click the
Invite memberorAdd userbutton. - Enter the person’s email address in the field provided.
- Pick a role for them. Common roles are:
Owner- full control, billing and admin rights.Admin- manage members and settings, but not necessarily billing.Member- regular access to organization resources.Billingor similar - access to billing only.- Optionally confirm any workspace or project access if that option appears.
- Click
Send inviteto send the invitation.
What happens after you invite
- The person receives an email with the invite and must accept it.
- Their status on the Members page will show as
Pendinguntil they accept, thenActive. - If they don’t get the email, ask them to check spam or to sign in and look for the pending invite.
Manage invites and user roles
- To change a user’s role, select the user and choose
Edit roleor similar. - To remove someone, select
RemoveorRevoke invitenext to their name. - You can resend an invite from the pending entry if needed.
OpenAI’s documentation on organization and user management outlines these UI steps and lists role permissions, so check that reference in your admin view if you need exact label names or a deeper description of each role.
Use Torii
Rather than handling OpenAI user provisioning directly through OpenAI’s interface, you can manage it via Torii, a SaaS Management Platform. SMPs let organizations centralize control of their SaaS apps and integrations, making it straightforward to programmatically onboard/offboard users, view subscription info, and perform other account tasks.
Instead of performing the change manually in OpenAI each time, Torii lets you automate the flow so the user is added automatically whenever a defined trigger occurs. Triggers might include a new hire, someone leaving the company, a contract renewal, or other HR or IT events - saving time when these operations repeat often.
To add a user in OpenAI directly from Torii, follow these steps:
1. Sign up for Torii
Contact Torii, and ask for your free two-week proof-of-concept.
2. Connect your OpenAI account to Torii
Once your Torii account is active, link your OpenAI account (if you already have one) to Torii. Here are the instructions for the OpenAI integration.

3. Create a Torii workflow for OpenAI
In Torii, build an automated workflow that adds a user in OpenAI. Go to the Workflows section, define the trigger event, then configure the action to add the user in OpenAI. After that, whenever the trigger fires, Torii will carry out the update automatically.
Use OpenAI’s API
Here you’ll use OpenAI’s SCIM (v2) API to provision a new user into your organization. The guide shows the minimal request, required fields, and how to check the result.
Gather an admin API key
- Use an organization-level API key that has provisioning/SCIM permissions.
- Keep this key private and call the API over HTTPS.
Build the SCIM create request
-
Endpoint:
POST https://api.openai.com/v1/scim/v2/Users - Required headers:
Authorization: Bearer YOUR_ADMIN_API_KEYContent-Type: application/scim+json
- Minimal JSON body (SCIM v2 core User schema):
{
"schemas": ["urn:ietf:params:scim:schemas:core:2.0:User"],
"userName": "[email protected]",
"name": {
"givenName": "New",
"familyName": "User"
},
"emails": [
{
"value": "[email protected]",
"type": "work",
"primary": true
}
],
"active": true
}
Example curl to create the user
Run a single HTTP request. Replace the token and email values:
curl -X POST "https://api.openai.com/v1/scim/v2/Users" \
-H "Authorization: Bearer $OPENAI_ADMIN_KEY" \
-H "Content-Type: application/scim+json" \
-D '{
"schemas":["urn:ietf:params:scim:schemas:core:2.0:User"],
"userName":"[email protected]",
"name":{"givenName":"New","familyName":"User"},
"emails":[{"value":"[email protected]","type":"work","primary":true}],
"active":true
}'
Check the response
- Success returns HTTP 201 and the created user object. Expect fields like
id,userName,active, andmetawith timestamps. - If you get 409, the user likely already exists. If 400, validate required fields and JSON shape.
Save the returned user id
Extract id from the response for future calls (updates or deactivation). You’ll use that id in other SCIM requests.
Common variations and optional fields
- Add
externalIdto map to your identity provider. - Include SCIM enterprise extensions if your setup uses attributes like
employeeNumber. Follow SCIM attribute names when adding extras.
Minimal troubleshooting tips
- Ensure
Content-Typeisapplication/scim+json. - Verify the token used is an admin/provisioning key. Regular API keys may not allow SCIM calls.
- Check for rate limits or org policies if requests fail repeatedly.
Security and hygiene
- Use a dedicated admin key for provisioning and rotate it regularly.
- Log only non-sensitive parts of requests and responses; never store raw API keys.
That’s it - create the JSON, POST to the SCIM Users endpoint with an admin key, then confirm the 201 response and save the user id.
Frequently Asked Questions
You have three options: invite teammates through the OpenAI interface, trigger automatic provisioning with Torii workflows, or send a SCIM v2 POST request to OpenAI’s /v1/scim/v2/Users endpoint using an admin API key.
OpenAI offers standard roles such as \"Owner\" for full control, \"Admin\" for member and settings management, \"Member\" for everyday access, and \"Billing\" for payment tasks only. Choose a role during the invite and modify it anytime.
Torii connects to your OpenAI organization, then runs workflows triggered by events like new hires or role changes. The workflow automatically calls OpenAI’s integration to add, update, or deactivate users, removing repetitive manual steps and keeping records synchronized.
Use a POST request to https://api.openai.com/v1/scim/v2/Users with Authorization and Content-Type headers. Include userName, name, emails, and active attributes in SCIM JSON. A successful call returns HTTP 201 along with the new user object.
SCIM provisioning changes organizational identity data, so OpenAI restricts the endpoint to keys with admin provisioning scope. Regular API keys lack those permissions and return authorization errors; an admin key ensures the request proceeds securely.
Confirm the Content-Type is application/scim+json and the JSON schema is valid. Verify the admin key is correct, active, and has provisioning rights. Response 400 signals bad fields, while 409 means the user already exists.

