6 Platforms for ServiceNow Access Certification in 2026

Enterprise IT teams rely on ServiceNow to manage everything from incident tickets to change requests and asset inventories. The platform’s flexibility creates a governance challenge that most organizations underestimate until an audit reveals over-privileged accounts or orphaned access lingering from departed contractors. ServiceNow licensing typically runs hundreds of dollars per user annually, making unreviewed accounts both a security liability and a direct hit to the IT budget.
ServiceNow's multi-layered permission model combines roles, groups, and three types of ACLs (table, record, and field level). Without automated tooling, understanding who can access what becomes nearly impossible at scale.
ServiceNow structures access through a hierarchy that starts with roles controlling features and capabilities, flows through groups that inherit those roles, and terminates in Access Control Lists that govern table-level, record-level, and field-level permissions. A single user might belong to five groups, each granting different roles, with ACL scripts adding conditional access that only triggers under specific circumstances. Manual audits of this structure consume weeks of analyst time and still miss edge cases that automated tools catch in minutes.
Third-party access certification platforms connect to ServiceNow through SCIM 2.0 APIs, REST endpoints, or purpose-built connectors. Some focus exclusively on ServiceNow governance while others treat it as one application in a broader SaaS portfolio. This article examines six platforms worth evaluating for ServiceNow access certification in 2026, covering their discovery capabilities, review workflows, and integration approaches.
★ = low · ★★ = medium · ★★★ = high
| Tool | Ease | Cost | AI Capabilities | Reviews |
|---|---|---|---|---|
| Torii | ★★★ | ★★ | ★★★ | ★★★ |
| Nudge Security | ★★★ | ★★ | ★★ | ★ |
| One Identity | ★ | ★★ | ★★ | ★★ |
| MiniOrange | ★★ | ★★★ | ★ | ★★ |
| CloudEagle | ★★ | ★ | ★★ | ★★ |
| Ping Identity | ★ | ★ | ★★★ | ★★★ |
Table of Contents
Torii
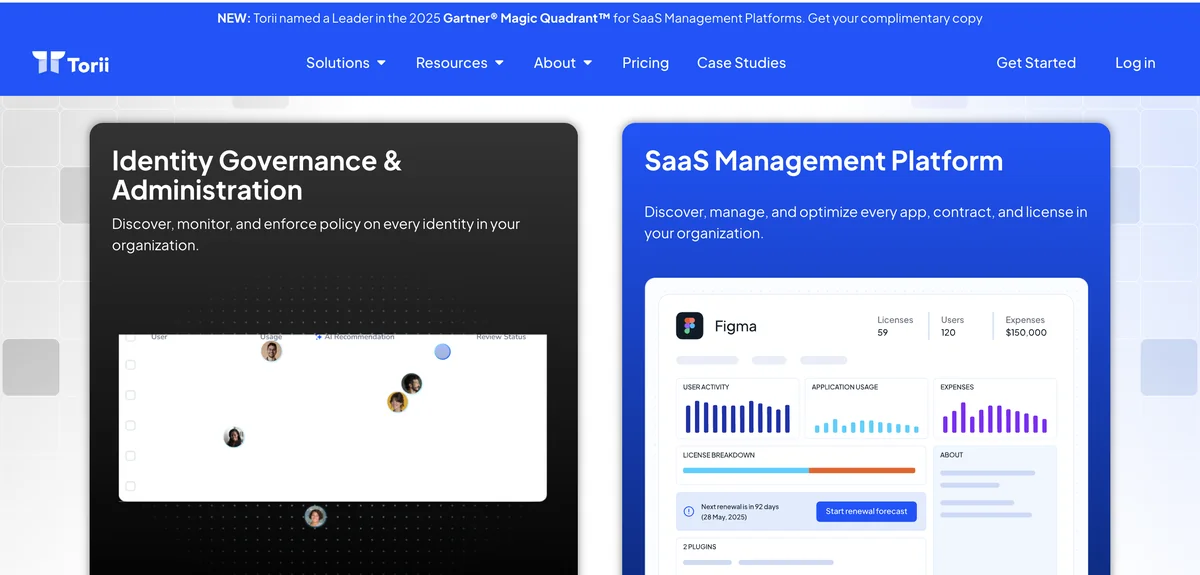
Torii positions ServiceNow as one component in a unified SaaS governance strategy rather than treating it as an isolated system requiring separate tooling. The platform discovers ServiceNow users through SSO and IdP integrations, direct API connections, and browser extension data, surfacing employee names, email addresses, job titles, departments, user status, and last used dates. For organizations running ServiceNow alongside dozens of other enterprise applications, this consolidated visibility proves valuable for identifying access patterns that span multiple systems.
Access certification workflows in Torii route review requests to the appropriate managers based on organizational hierarchy. Reviewers can approve, modify, or revoke ServiceNow access without context switching between systems. The platform flags suspicious patterns automatically, such as ServiceNow admin accounts that haven’t been used in months or employees whose department changed but whose access didn’t update to match. When certifications complete, workflow automation handles deprovisioning through ServiceNow’s SCIM integration or direct API calls.
Torii’s AI continuously monitors ServiceNow access patterns rather than relying solely on periodic campaign cycles. The system learns what normal access looks like for different roles and departments, flagging anomalies when users accumulate permissions beyond their peer group. Real-time Slack alerts notify administrators when action is needed, and immutable audit trails capture every certification decision for compliance documentation. Learn more at Torii.
Pros:
- Unified SaaS governance treats ServiceNow as part of complete application portfolio with cross-system visibility
- AI-powered anomaly detection identifies unusual access patterns before they become compliance issues
- In-place attestations let reviewers certify ServiceNow access without leaving their normal workflow
- Combined SaaS management and IGA eliminates need for separate tools while providing cost visibility alongside security
Cons:
- Enterprise pricing reflects comprehensive feature set and may exceed budget for organizations with limited SaaS portfolios
- Cloud-native architecture means organizations requiring on-premise deployment need alternative solutions
| Reviews: G2 rating of 4.5 out of 5 stars (302 reviews) | Capterra rating of 4.9 out of 5 stars (26 reviews) |
Nudge Security
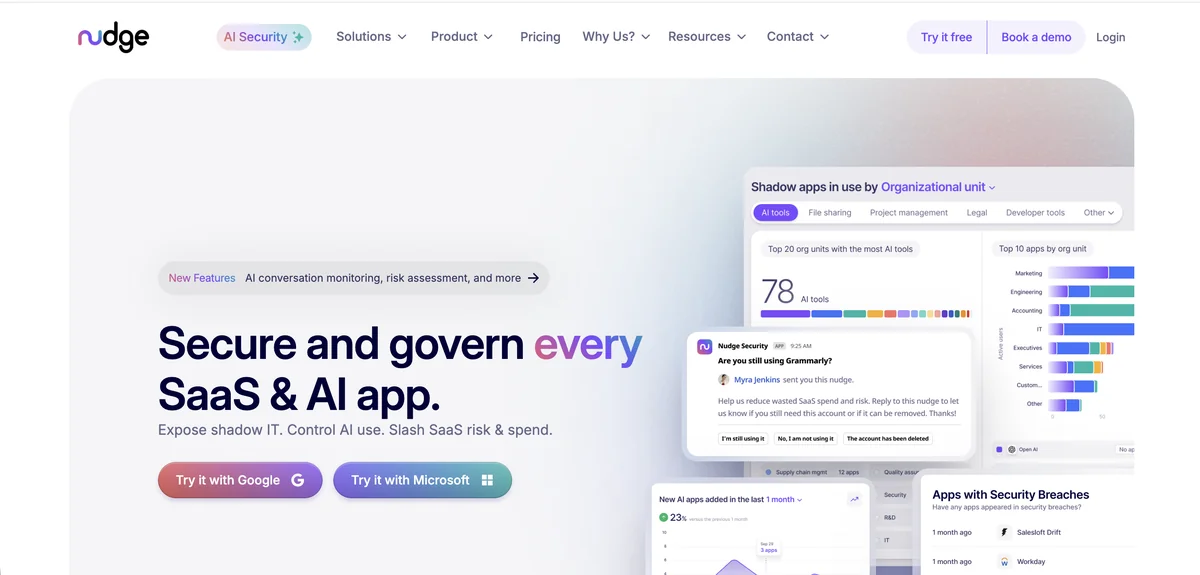
Nudge Security takes a fundamentally different approach to ServiceNow discovery by monitoring email confirmations, login notifications, and account creation messages rather than relying solely on API connections. This patented method catches ServiceNow instances that exist outside IT’s sanctioned provisioning channels, including sandbox environments that developers spun up for testing and never decommissioned. The platform achieves full visibility within approximately 75 minutes of initial setup without requiring agents, proxies, or browser extensions.
The User Access Review Playbook automatically categorizes ServiceNow alongside other discovered applications and creates compliance groupings for systematic certification. Reviewers receive nudges through Slack or email prompting them to confirm whether specific ServiceNow accounts remain necessary. Changes route to the appropriate app owners for cleanup, and the platform generates auditor-ready reports documenting all actions taken. This behavioral approach achieves an 83% compliance rate according to Nudge Security’s data, significantly higher than traditional blocking methods.
Lifecycle management capabilities address ServiceNow access throughout the employee journey. The Offboarding Playbook identifies all ServiceNow access for departing employees, eliminating the manual effort of checking multiple systems. The Abandoned Account Cleanup playbook surfaces ServiceNow accounts that haven’t seen activity, helping organizations reclaim licenses and reduce their attack surface. Explore at Nudge Security.
Pros:
- Email-based discovery finds ServiceNow instances that bypass traditional IdP monitoring and API integrations
- Deployment completes in approximately 75 minutes without agents or browser extensions
- Behavioral nudge approach achieves higher compliance rates than enforcement-based methods
Cons:
- Requires Google Workspace or Microsoft 365 for email-based discovery to function
- Nudges guide behavior rather than enforce it, meaning users can still ignore prompts
- Limited public reviews compared to more established platforms makes peer validation harder
| Reviews: G2 rating of 5.0 out of 5 stars (limited reviews) | Gartner Peer Insights rating of 4.7 out of 5 stars (22 reviews) |
ServiceNow evaluates access through three ACL types (table, record, and field level), with roles cached in server memory for performance. Users inherit permissions from multiple groups, creating cascading access that manual audits struggle to trace accurately.
One Identity
One Identity Manager connects to ServiceNow through its Starling Connect service and native SCIM protocol support, providing enterprise-grade governance for organizations with complex hybrid environments. The platform combines IGA with privileged access management under a single vendor umbrella, which matters for ServiceNow deployments where admin accounts require elevated oversight. Deep integrations with Active Directory and SAP make One Identity particularly relevant for enterprises where ServiceNow sits alongside significant Microsoft or SAP investments.
Attestation policies in One Identity define certification parameters including which ServiceNow objects get reviewed, how often reviews occur, and who serves as the responsible attestor. The platform supports multiple certification types covering user attestation by managers, external user certification for contractors with ServiceNow access, and role certification for validating ServiceNow application roles. Each attestation step creates audit-proof tracking that compliance teams can reconstruct for regulatory examinations.
The connector ecosystem includes over 6,000 pre-built application integrations through the OneLogin component, with native ServiceNow integration for ITSM workflows. Implementation typically requires partner involvement given platform complexity, but customers report significant automation benefits once deployed. The platform has managed identities for organizations that have used it for over a decade, demonstrating enterprise durability. Details at One Identity.
Pros:
- Unified IGA and PAM platform provides comprehensive governance for ServiceNow admin accounts
- Cost-effective compared to SailPoint and other enterprise IGA platforms with similar capabilities
- Native ServiceNow integration through Starling Connect simplifies ITSM workflow coordination
Cons:
- Attestation interface receives criticism for outdated user experience that frustrates reviewers
- Complex implementation typically requires partner involvement and weeks to months of deployment time
- Steep learning curve demands dedicated IAM expertise that smaller organizations may lack
| Reviews: G2 rating of 3.5 out of 5 stars | Capterra rating of 5.0 out of 5 stars (2 reviews) | Gartner Peer Insights rating of 4.4 out of 5 stars (155 reviews) |
MiniOrange

MiniOrange offers ServiceNow integration as part of its broader 6,000+ application connector library, providing identity governance at price points significantly below enterprise competitors. The platform handles ServiceNow user lifecycle from creation through changes to eventual removal, applying governance to employees, guest users, and service accounts. At $2-3 per user monthly, MiniOrange makes access certification accessible to organizations that cannot justify SailPoint or Okta pricing for their ServiceNow governance needs.
Access Governance capabilities focus on auditing, logging, and analyzing ServiceNow identity and access data. The platform supports SAML, OAuth, and OpenID Connect for ServiceNow authentication integration, with SCIM provisioning handling automated account creation and deprovisioning. Adaptive risk-based authentication assesses contextual factors like geographic location, device type, and user behavior patterns, triggering step-up authentication for ServiceNow access attempts that appear unusual.
The Access Governance Automation app integrates with Jira for organizations using that platform, enabling end users to submit ServiceNow access requests through familiar service management interfaces. Approval workflows route based on predefined rules to the correct approver, with instant provisioning once approvals complete. Granular logging captures every request, approval, and provisioning action for compliance reporting. Visit MiniOrange for more information.
Pros:
- Affordable pricing at $2-3 per user monthly opens access governance to budget-constrained teams
- Rapid deployment measured in hours rather than months typical of enterprise IGA implementations
- Extensive pre-built integrations including ServiceNow eliminate custom connector development
Cons:
- Limited native access certification features compared to dedicated IGA platforms like SailPoint
- Customer support quality varies significantly based on user reports, creating implementation risk
- Access governance automation features require Jira, which may not align with all toolsets
| Reviews: G2 rating of 4.5 out of 5 stars (264 reviews) | Capterra rating of 4.5 out of 5 stars (36 reviews) |
CloudEagle
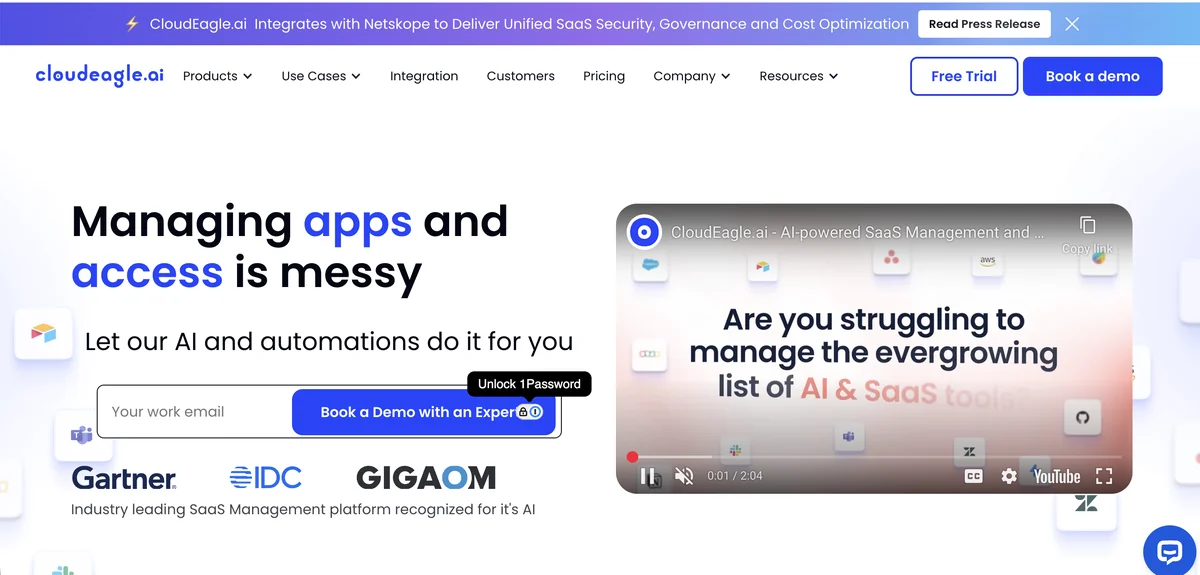
CloudEagle approaches ServiceNow governance through its unified platform that combines SaaS management, governance, and procurement capabilities. The system auto-collects ServiceNow user and access data from SSO, identity providers, and 500+ direct connectors, providing granular visibility into who has access to ServiceNow and what they can do within it. Access reviews can initiate immediately or schedule for later dates, with recurring cycles running automatically for continuous compliance.
AI-powered detection flags ServiceNow users with excessive permissions, inactive admin accounts, and accounts that haven’t logged in for 90 or more days. The platform prioritizes high-risk cases for immediate review while handling routine certifications through automated workflows. Slack-native workflows let reviewers approve ServiceNow access directly within their collaboration tools, dramatically improving adoption compared to systems requiring separate login portals.
Compliance reporting generates SOC 2 documentation in approximately 15 minutes according to CloudEagle, compared to hours or days for manual processes. Every approval, revocation, and exception logs automatically with timestamps and decision evidence. The platform supports both SCIM and non-SCIM applications from a single dashboard, handling ServiceNow alongside applications that lack modern provisioning standards. Explore at CloudEagle.
Pros:
- Slack-native workflows enable ServiceNow access approvals without leaving collaboration tools
- AI automatically flags over-privileged ServiceNow accounts and inactive admin access
- 500+ direct integrations ranked second among vendors in Gartner report for connector breadth
Cons:
- Steep learning curve reported by users navigating extensive feature set during implementation
- Integration inconsistencies occasionally require manual intervention for certain applications
- No API access limits custom development and data extraction for external reporting tools
| Reviews: G2 rating of 4.7 out of 5 stars (150+ reviews) | Gartner Peer Insights rating of 4.6 out of 5 stars (53 reviews) |
Ping Identity

Ping Identity brings nine consecutive years of Gartner Magic Quadrant leadership in Access Management to ServiceNow governance, offering AI-powered certification through its Autonomous Identity capabilities. The platform leverages machine learning to collect and analyze ServiceNow identity data, identifying access blind spots that traditional IAM solutions miss. For organizations already running Ping for authentication, extending to ServiceNow access certification provides architectural consistency across the identity stack.
Access Certification Templates provide standardized frameworks following industry best practices, while Certification Campaigns execute reviews based on those templates with defined certifiers and scope. AI-assisted decisioning provides recommendations that help reviewers make informed decisions quickly, with micro-certifications enabling ad hoc reviews for just-in-time access validation. The platform handles application access certification, role membership certification, account certification, and entitlement certification across ServiceNow environments.
PingOne Protect calculates risk in real-time using multiple predictors including bot detection, IP velocity, geovelocity anomaly, and user risk behavior analysis. High-risk ServiceNow access attempts trigger step-up authentication or route to security teams for manual review. Deployment flexibility spans SaaS, FedRAMP, private cloud, and on-premises options, accommodating organizations with strict regulatory requirements. Learn more at Ping Identity.
Pros:
- AI-powered Autonomous Identity evaluates millions of ServiceNow permissions per minute
- Nine-year Gartner Magic Quadrant leadership provides confidence in platform maturity
- Deployment flexibility includes FedRAMP and on-premises options for regulated industries
Cons:
- Complex initial setup requires significant IAM expertise and extends deployment timelines
- Identity Governance features require separate purchase from core PingOne platform
- Higher cost structure positions platform above mid-market budgets at $16,000+ annually
| Reviews: G2 rating of 4.5 out of 5 stars (264 reviews) | Capterra rating of 4.7 out of 5 stars (39 reviews) | Gartner Peer Insights rating of 4.4 out of 5 stars (612 reviews for Access Management) |
How to Choose
The right ServiceNow access certification platform depends on where ServiceNow fits within your broader identity governance strategy. Organizations treating ServiceNow as one application in a large SaaS portfolio benefit from platforms like Torii or CloudEagle that provide unified visibility across all applications. Enterprises with complex hybrid environments and existing investments in Microsoft or SAP ecosystems may prefer One Identity for its deep integration capabilities and combined IGA plus PAM approach.
AI-powered shadow IT discovery that finds unauthorized ServiceNow instances, unified SaaS governance treating ServiceNow alongside your complete application portfolio, automated license remediation, and real-time Slack alerts for certification deadlines.
Budget-constrained teams should evaluate MiniOrange for its accessible pricing at $2-3 per user monthly, though they should expect fewer native certification features than enterprise platforms. Organizations prioritizing shadow IT discovery above all else may find Nudge Security’s email-based approach catches ServiceNow instances that other tools miss entirely. For Fortune 500 enterprises requiring maximum AI intelligence and regulatory certification, Ping Identity’s proven scale and nine years of Gartner recognition warrant serious consideration despite higher implementation complexity.
Frequently Asked Questions
ServiceNow access certification reduces security risk and license waste by identifying orphaned accounts and over-privileged users. Automated certification helps auditors trace permissions across roles, groups, and ACLs, speeding cleanup and preserving costly per-user licenses.
They connect using SCIM 2.0 provisioning, ServiceNow REST APIs, SSO/IdP integrations, browser extensions, or purpose-built connectors. These methods enable discovery, automated attestations, and deprovisioning workflows while accommodating environments with non-standard or sandbox instances.
Vendors use SSO and IdP data, direct API pulls, SCIM provisioning logs, browser-extension telemetry, and email-based discovery that monitors confirmations and account notices. Combining methods is essential to detect shadow IT, developer sandboxes, and unsanctioned instances missed by single approaches.
Torii and CloudEagle excel at unified SaaS governance by treating ServiceNow as one application among many, providing cross-system visibility, automated certification workflows, AI anomaly detection, Slack-native approvals, and license remediation to streamline access reviews across an entire application portfolio.
Evaluate integration depth (SCIM, REST, AD/SAP connectors), deployment options (SaaS, on-prem, FedRAMP), AI detection capabilities, attestation workflows, ease of reviewer experience, implementation time, and total cost of ownership including license remediation and support.
Implement automated access certification campaigns, enforce offboarding playbooks, use AI to flag inactive or over-privileged accounts, and automate deprovisioning via SCIM or API calls. Regular audits and cross-application visibility help reclaim licenses and shrink the attack surface.

