3 Ways to Add Users to Your DigiCert Account in 2026
Managing certificates often involves developers, security leads, and auditors all at once. When they need access to your DigiCert console, you want a simple way to grant it without losing oversight.
Below, we unpack three practical methods for adding users, highlighting when each fits and which roles and privileges it unlocks. Use them to shape a flexible, safe workflow that grows with your team.
Table of Contents
Use DigiCert’s UI
Here, you’ll work inside the DigiCert CertCentral portal to add a new teammate.
Step 1. Sign in and find the Users page
- Log in to CertCentral.
- In the left menu, pick Account, then User Access. (Some accounts label it Users. Same place, same tools.)
Step 2. Start the “Add user” flow
- Select the blue Add user button in the upper-right corner.
- If the button is missing, your current role may block user management. Ask a Manager-level admin to improve your rights.
Step 3. Enter basic details
- First name
- Last name
- Email address (this becomes the username)
CertCentral sends the invite, so you don’t create a password here.
Step 4. Pick the user’s role
Choose one:
- Manager: full control, including billing and user management
- Finance Manager: sees orders and billing, can’t change settings
- Standard User: can request and manage certificates
- Viewer: read-only access
- Limited User: can only approve certificates they requested
Need a quick reminder on what each role covers? DigiCert’s “User roles and permissions” document includes a concise chart.
Step 5. (Optional) Narrow their scope
- Division: tie the user to a specific business unit.
- Allowed domains: list the domains they can work with.
- Groups: drop them into any existing CertCentral group for bulk permission handling.
You can skip these for now and tighten things later.
Step 6. Add an invite note (optional)
There’s a small text box for a custom message. A quick line like “Welcome to the SSL team.” makes the email feel more personal.
Step 7. Send the invitation
- Click Add User.
- The new user shows up in your list with a Pending status.
They’ll get an email from DigiCert with a link to create a password and finish setup. Once they log in, the status flips to Active, and they’re ready to request or manage certificates based on the role you picked.
Use Torii
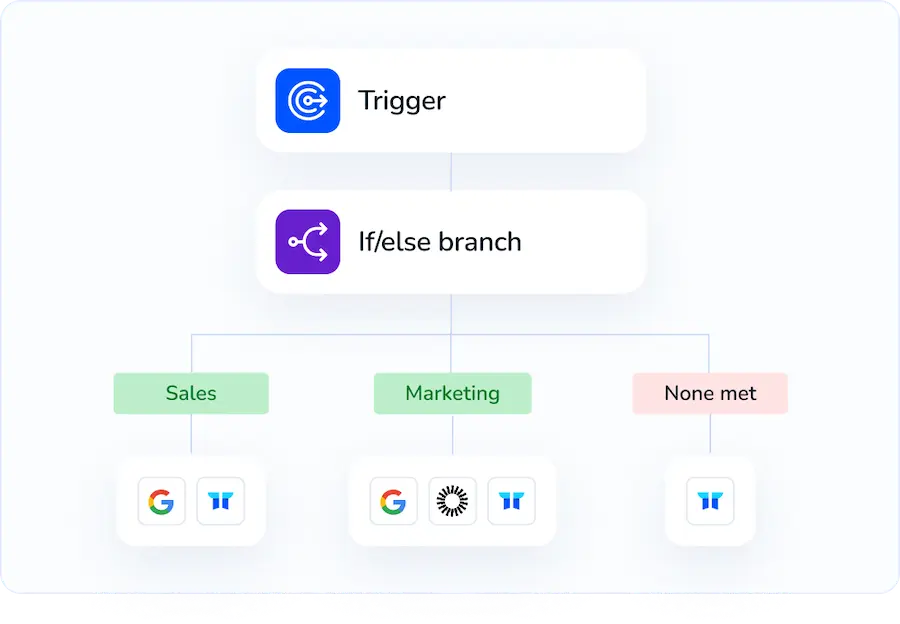
Instead of working with DigiCert directly, you can rely on Torii, a SaaS management platform, to create users in DigiCert. SMPs give teams a central dashboard for managing SaaS subscriptions and integrations, making it easy to add or remove employees, check license counts, and more.
Relying on DigiCert by itself means manually creating each account. Torii automates that step as soon as a trigger fires, such as a new hire, a departure, or a contract renewal, which saves time when the task repeats.
To provision users in DigiCert from Torii, follow these instructions:
1. Register for Torii
Contact Torii and request a free two-week proof of concept.
2. Link your DigiCert account to Torii
Once your Torii environment is live, link your existing DigiCert account. For details, see the official guide: DigiCert Integration.
3. Build a workflow for DigiCert inside Torii
Open the Workflows tab, pick a trigger, and add the action that creates a DigiCert user. After that, each time the trigger runs, Torii provisions the account automatically.
Use DigiCert’s API
Need to drop a new teammate into CertCentral without touching the web console? The User API has you covered. Below is the shortest path from “no user” to “user created.”
1. Make sure your API key is ready
DigiCert hands out the key inside CertCentral as soon as you request one from the dashboard. Copy it and store it in an environment variable so you’re not pasting it everywhere.
export DC_API_KEY="YOUR_DCGCERT_API_KEY"
You’ll pass this key in the X-DC-DEVKEY header on every call.
2. (Optional) Look up the division or container ID
If your account only has one division, you can skip this. If not, grab the right ID so the user lands in the correct spot.
curl -s \
-H "X-DC-DEVKEY: $DC_API_KEY" \
"https://www.digicert.com/services/v2/division?limit=100"
Copy the id value for the division you want. You can do the same for containers:
curl -s \
-H "X-DC-DEVKEY: $DC_API_KEY" \
"https://www.digicert.com/services/v2/container?limit=100"
3. Decide which roles the user needs
Role IDs vary by account, so fetch them once and reuse:
curl -s \
-H "X-DC-DEVKEY: $DC_API_KEY" \
"https://www.digicert.com/services/v2/user/access_roles"
The response shows something like:
[
{ "id": 1, "name": "Requester" },
{ "id": 2, "name": "Manager" },
{ "id": 3, "name": "Finance" }
]
Pick the IDs that fit the new user.
4. Build the request body
Start by creating a JSON file called new_user.json on your local system. At minimum you need username, first_name, last_name, email, and access_roles. You can include password if you want to set it yourself; leave it out and DigiCert will send a welcome email so the user can finish setup.
{
"username": "jdoe",
"first_name": "Jane",
"last_name": "Doe",
"email": "[email protected]",
"telephone": "+1 555 0100",
"division_id": 12345,
"access_roles": [ { "id": 1 }, { "id": 2 } ],
"language_code": "en"
}
Common extras:
container_idif you prefer to tie the user to a specific container.job_titlefor internal tracking.signature_allow_pass_onset totrueif the user can pass on e-sign requests.
5. Call the Create User endpoint
Send the POST request shown below using the JSON file you just created as the payload.
curl -X POST \
-H "X-DC-DEVKEY: $DC_API_KEY" \
-H "Content-Type: application/json" \
-D @new_user.json \
"https://www.digicert.com/services/v2/user"
If the call succeeds, the service returns a response similar to the one below.
{
"id": 67890,
"username": "jdoe",
"status": "invited"
}
Store the id if you plan to update or deactivate the user later.
6. Verify the invitation status
If you didn’t set a password, the user’s status will be invited. DigiCert emails them automatically. To check whether they finished onboarding, poll the user record:
curl -s \
-H "X-DC-DEVKEY: $DC_API_KEY" \
"https://www.digicert.com/services/v2/user/67890"
When status flips to active, they’re good to go.
7. Troubleshoot common errors
- 400 Bad Request: A required field is missing or misspelled. Check your JSON keys.
- 409 Conflict: Username or email already exists. Try a different one or look up the existing user.
- 403 Forbidden: Your key lacks permission to create users. Confirm your own role and API scope.
With those steps complete, you’ve successfully added a new teammate entirely from the command line. You accomplished it with cURL and an API key, leaving the web UI for someone else.
Torii for SaaS Management
Looking to streamline and control your SaaS landscape across the company? Torii’s SaaS Management Platform can help:
- Uncover shadow IT: AI-driven discovery spots unsanctioned apps in every corner of the business, all without disrupting users.
- Reduce spend: Trim wasted budget by removing idle licenses and combining overlapping tools.
- Automate onboarding & offboarding: Hand off user-lifecycle tasks so teams save hours and avoid errors.
- Receive renewal reminders: Get timely alerts before contracts expire, giving you space to negotiate.
Torii delivers a unified SaaS Management Platform that becomes the single source of truth for Finance, IT, and Security teams.
Discover the full feature set and pricing by visiting Torii.
Frequently Asked Questions
You have three ways to add teammates to DigiCert CertCentral: use the portal's Add User button, trigger an automated workflow in Torii, or call the User API's POST /user endpoint. Pick the method that suits your team's workflow and technical skills.
CertCentral offers five default roles: Manager with full control, Finance Manager for billing-only tasks, Standard User for certificate requests, Viewer for read-only access, and Limited User who can approve only their own orders. Choose the role that matches the person's duties.
Yes. After connecting your DigiCert account to Torii, you can build a workflow that auto-creates or deactivates users based on triggers like new hires, departures, or renewals. The automation saves manual clicks, keeps license counts accurate, and speeds onboarding.
The POST https://www.digicert.com/services/v2/user endpoint creates a new CertCentral user. Supply an X-DC-DEVKEY header plus a JSON body containing username, name, email, and access_roles (and optional division or container IDs). A successful call returns the user's ID and invited status.
During the Add User flow, expand the Optional Scope section, then set Division, Allowed Domains, or Groups fields. These filters bind the account to a business unit or domain list, limiting what certificates they can view or request without affecting others.
Manager is the super-admin: they control billing, certificate orders, account settings, and user management. Finance Manager sees orders, invoices, and payment details but cannot modify settings or invite new users, making it ideal for accounting teams that need visibility without administrative power.

