#1 in Shadow IT Discovery & Action
The most advanced discovery platform helps you understand and optimize your app usage, software spend, and drive employee productivity
Most of your tech stack is hiding in the shadows
Shadow IT: Why is it a growing problem?
Shadow IT is a risk for organizations because employees use unsanctioned applications and devices that may not be adequately protected, making data vulnerable to hackers. To ensure their data is safe, companies should have clear rules about using technology and train their employees accordingly.
Shadow IT security measures
Without shadow IT security measures in place, vulnerabilities can be introduced without being detected, making them difficult to manage due to their lack of visibility. Incident responses are also hindered by complications in tracing malicious activity and creating an appropriate response plan.
What are “Shadow IT” applications?
Shadow IT applications can pose serious risks to organizations through security vulnerabilities, compliance issues, operational clashes, and more. Businesses should use assurance and testing services as part of a comprehensive security plan in order to mitigate any potential risks .
What is Shadow IT CASB utilized for?
Shadow IT CASB solutions provide visibility, monitoring, and encryption to help protect confidential data in cloud-based services from potential security threats.
Shadow IT in the cloud and how it affects cloud computing from a cloud security perspective
Shadow IT is the use of unauthorized online services and applications within an organization, creating security risks such as data breaches. To reduce this risk, organizations need to keep an eye on what users are doing and make sure that cloud technology vendors follow best practices and have enough security in place.
Shadow IT tools
Shadow IT tools like Torii can help you find out which employee apps are being used across your organization. Click the “Request a demo” button today to book a demo.
How Torii illuminates Shadow IT
Find Every App
See sanctioned and Shadow IT apps in one unified view
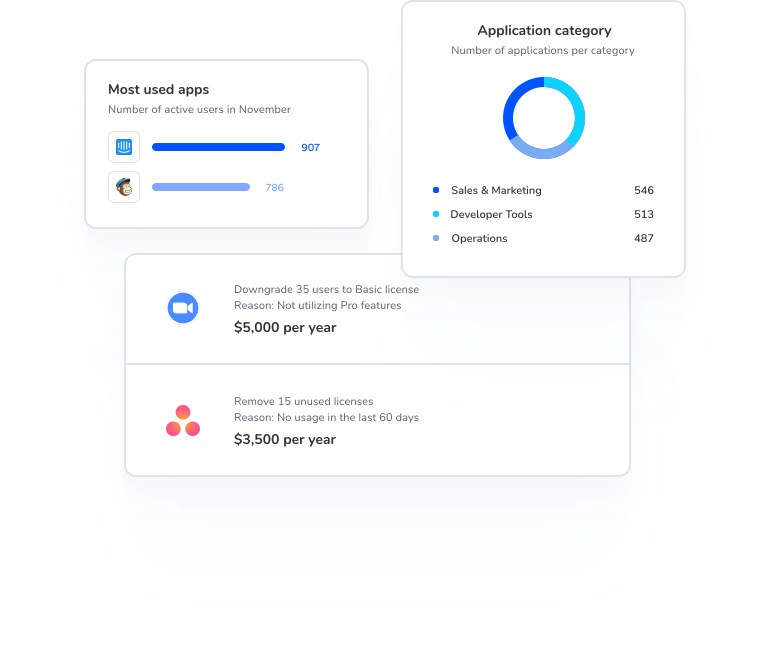
“With Torii, we could finally see every single SaaS tool we were using in the company. It enabled us to review their popularity and usage, determine which applications were redundant and which ones we could cut down.”
Ron Peres
Sr. Director, Global Corporate IT & Information Systems
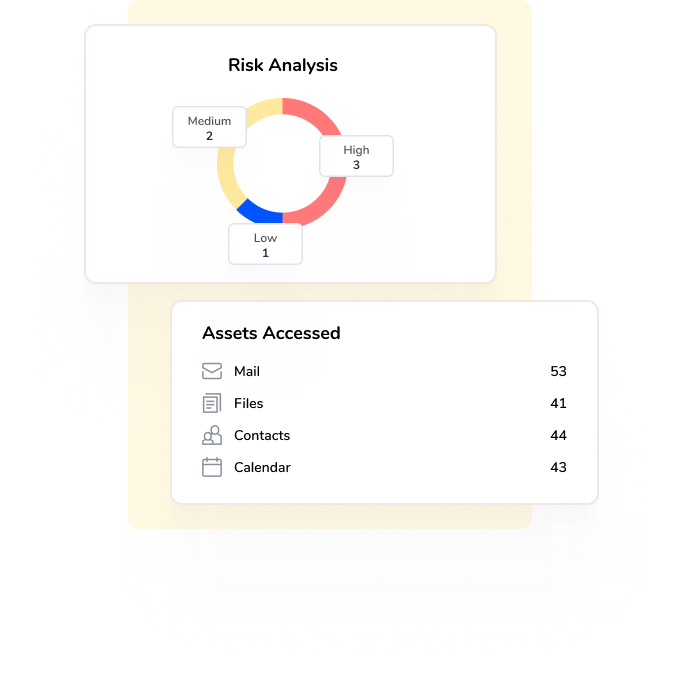
Shadow IT Risk Mapping
Identify risky apps in your Shadow IT portfolio based on their permissions to modify sensitive data
Don't just see Shadow IT: do something about it
Torii's customers have:
3x
$1m
Saved more than $1m a year on unused SaaS accounts
75%
Cut hours spent on manual IT tasks by at least 75%
See Torii in Action
Learn how Torii can automate your SaaS management.