#1 in Shadow IT Discovery & Action
The most advanced discovery platform helps you understand and optimize your app usage, software spend, and drive employee productivity
Most of your tech stack is hiding in the shadows
What is shadow IT
Shadow IT refers to any technology used inside an organization without explicit approval, which can cause data breaches, security issues, and compliance risks.
Shadow IT examples
- Productivity tools like Office 365 and Slack
- Google suite apps like Gmail and Drive
- Collaboration Tools that include storage like Dropbox
- Bluetooth sharing tools like Apple AirDrop
Shadow IT services
Shadow IT services pose a risk to organizations as they are often not secure and can cause unauthorized chaos, strain on resources, and difficulties if system failures occur.
Shadow IT projects
Shadow IT projects are designed to provide immediate solutions that work around existing hardware and software constraints, use virtual or cloud-based resources, and take advantage of advanced technologies like distributed networks and data encryption techniques while helping organizations remain agile.
What is shadow IT in cloud computing
Shadow IT in cloud computing is a dangerous issue as it can lead to data breaches and other cybersecurity issues, compliance violations with hefty fines, and increased costs due to unauthorized services being used without prior knowledge.
Shadow IT systems
Shadow IT Systems can be helpful but must have proper oversight and security protocols in place and remain under the organization’s IT team for monitoring.
How Torii illuminates Shadow IT
Find Every App
See sanctioned and Shadow IT apps in one unified view
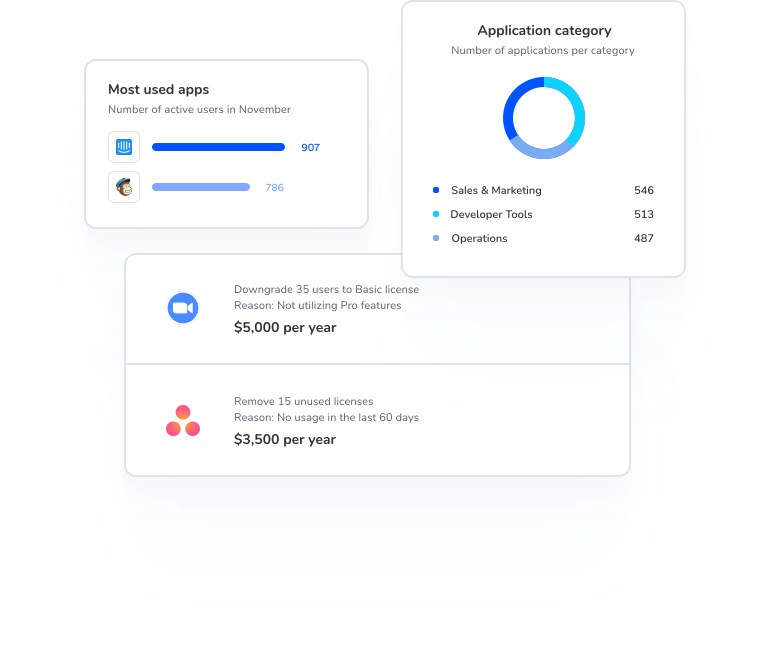
“With Torii, we could finally see every single SaaS tool we were using in the company. It enabled us to review their popularity and usage, determine which applications were redundant and which ones we could cut down.”
Ron Peres
Sr. Director, Global Corporate IT & Information Systems
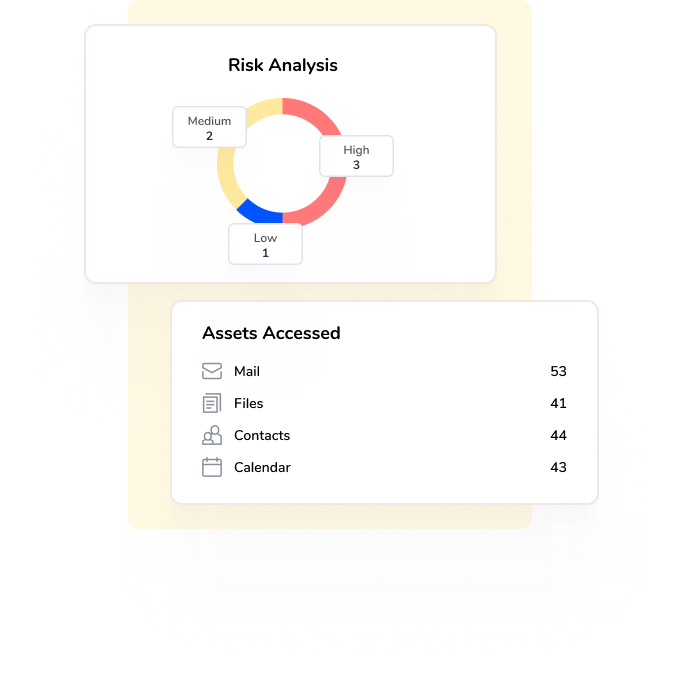
Shadow IT Risk Mapping
Identify risky apps in your Shadow IT portfolio based on their permissions to modify sensitive data
Don't just see Shadow IT: do something about it
Torii's customers have:
3x
$1m
Saved more than $1m a year on unused SaaS accounts
75%
Cut hours spent on manual IT tasks by at least 75%
See Torii in Action
Learn how Torii can automate your SaaS management.